The Cyber Triage team likes to build stuff around themes and one of our current themes is about integrations. It has been a growing feature request. This blog post talks about our recent Phantom integration. Next time, we’ll talk about Splunk.
The Phantom integration makes your response team more efficient by automatically starting an analysis of a remote system so that the data is waiting for you when you have time to start working on the alert.
Orchestration Integration
Orchestration is all the rage in many companies because they want to automate as much of their security process as possible. This allows them to respond faster to incidents and therefore more quickly contain the damage.
Phantom allows you to connect your various security applications. Users can make “playbooks” that outline a series of actions to be performed for different types of alerts and scenarios. Each action can interact with a security application or perform some lookups.
When Cyber Triage is integrated with Phantom, you can add an action to your playbook that will cause Cyber Triage to collect and analyze data from a remote host.
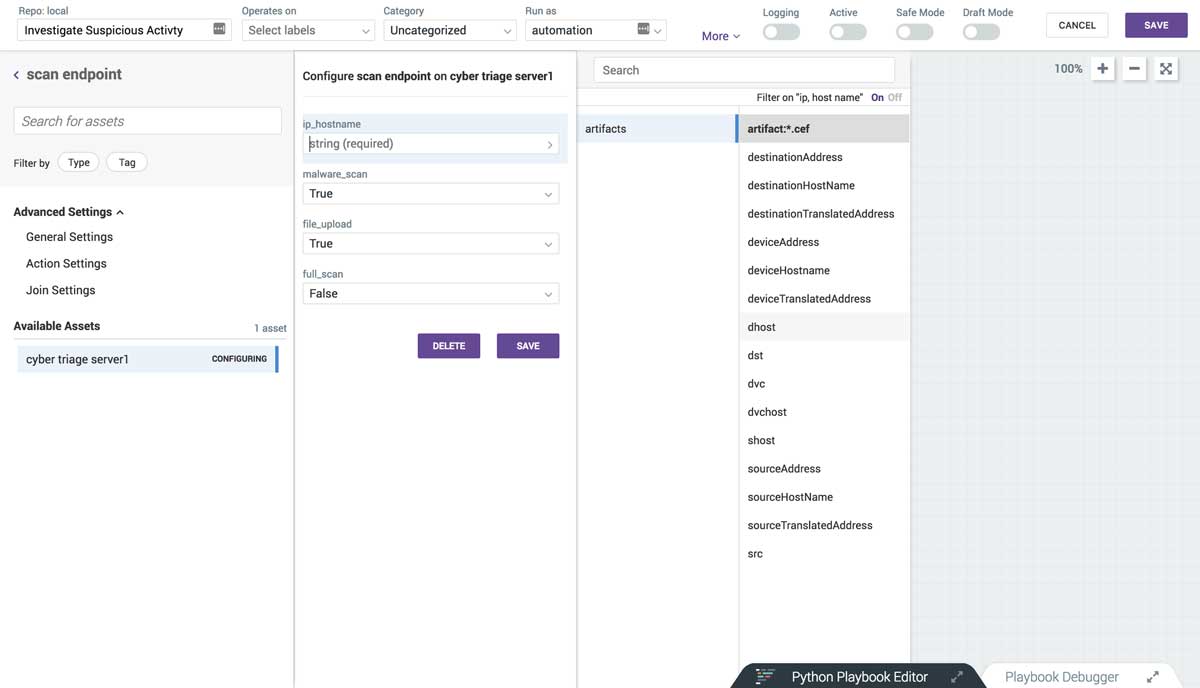
An example scenario is that your Tier 1 SOC analyst looks at an alert and she decides that the alert needs further investigation and endpoint and other data are needed. She could start a playbook to escalate the incident that:
- Updates a ticketing system
- Starts network collection to and from the endpoint
- Causes Cyber Triage to analyze the endpoint
Let’s look at how to make the integration.
Integration Requirements
The Phantom and Cyber Triage integration is easy to make. You’ll need:
- An installed version of Phantom
- Team version of Cyber Triage (the Lite and Standard desktop version will not work)
- Cyber Triage App from the Phantom App marketplace
To make the integration:
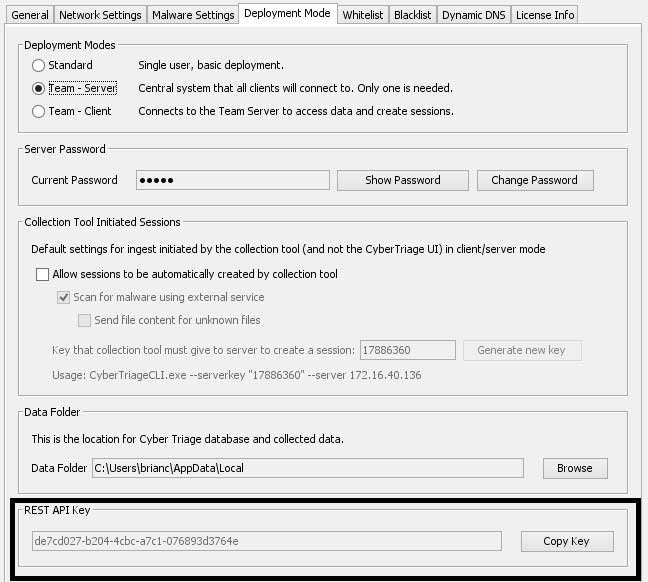
- Go to your Cyber Triage Team Server and get the REST API key from the Options panel.
- Install the Cyber Triage App from the Phantom interface.

- Configure the installed App and provide:
- Hostname where Cyber Triage Server is running
- REST API Key that we got from the previous Options panel
- Login and password of an administrator account on the remote endpoints
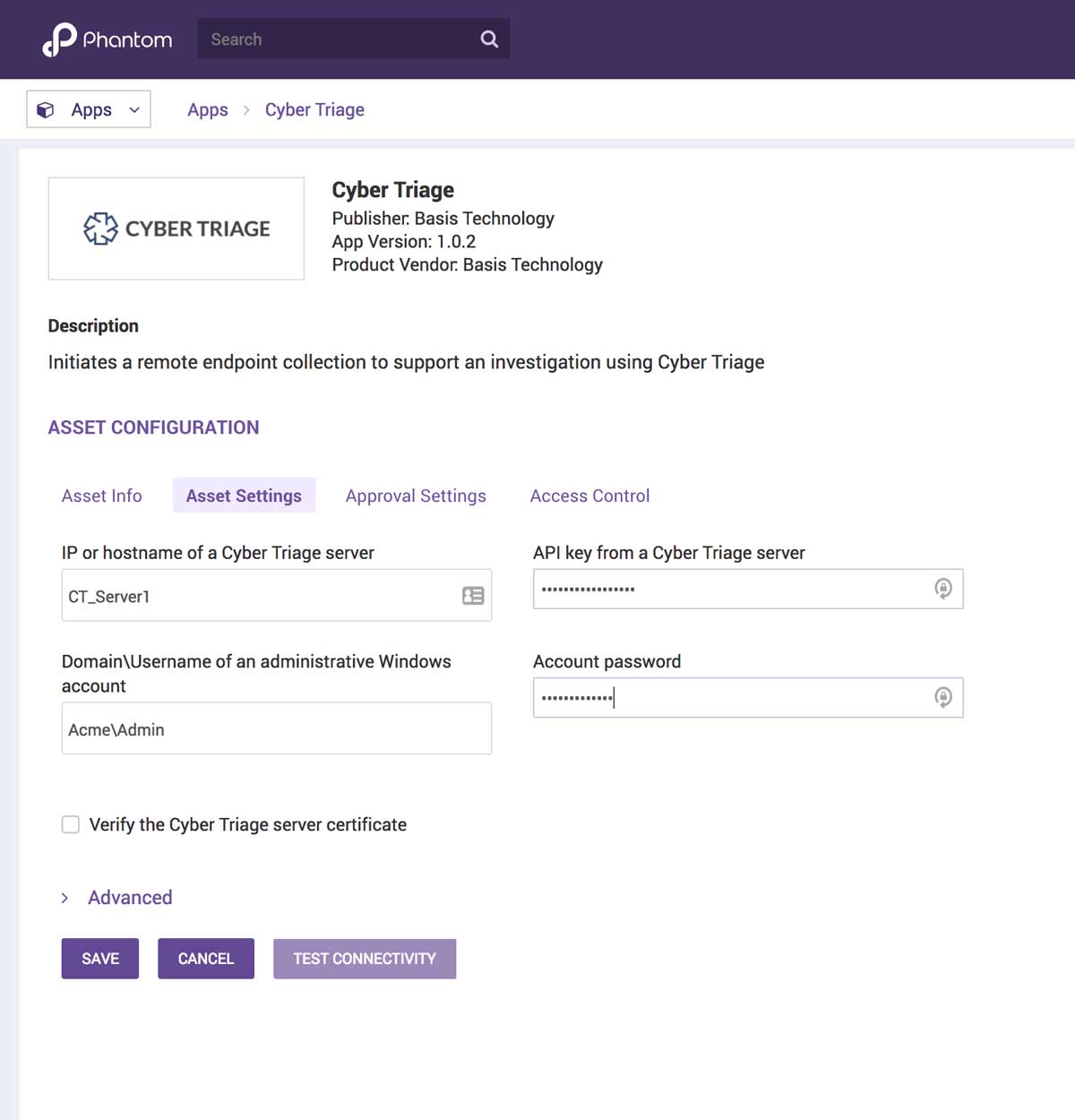
Once this data has been entered, you can test the integration using the “Test Connectivity” button, which will ensure that Phantom can communicate with the Cyber Triage REST API.
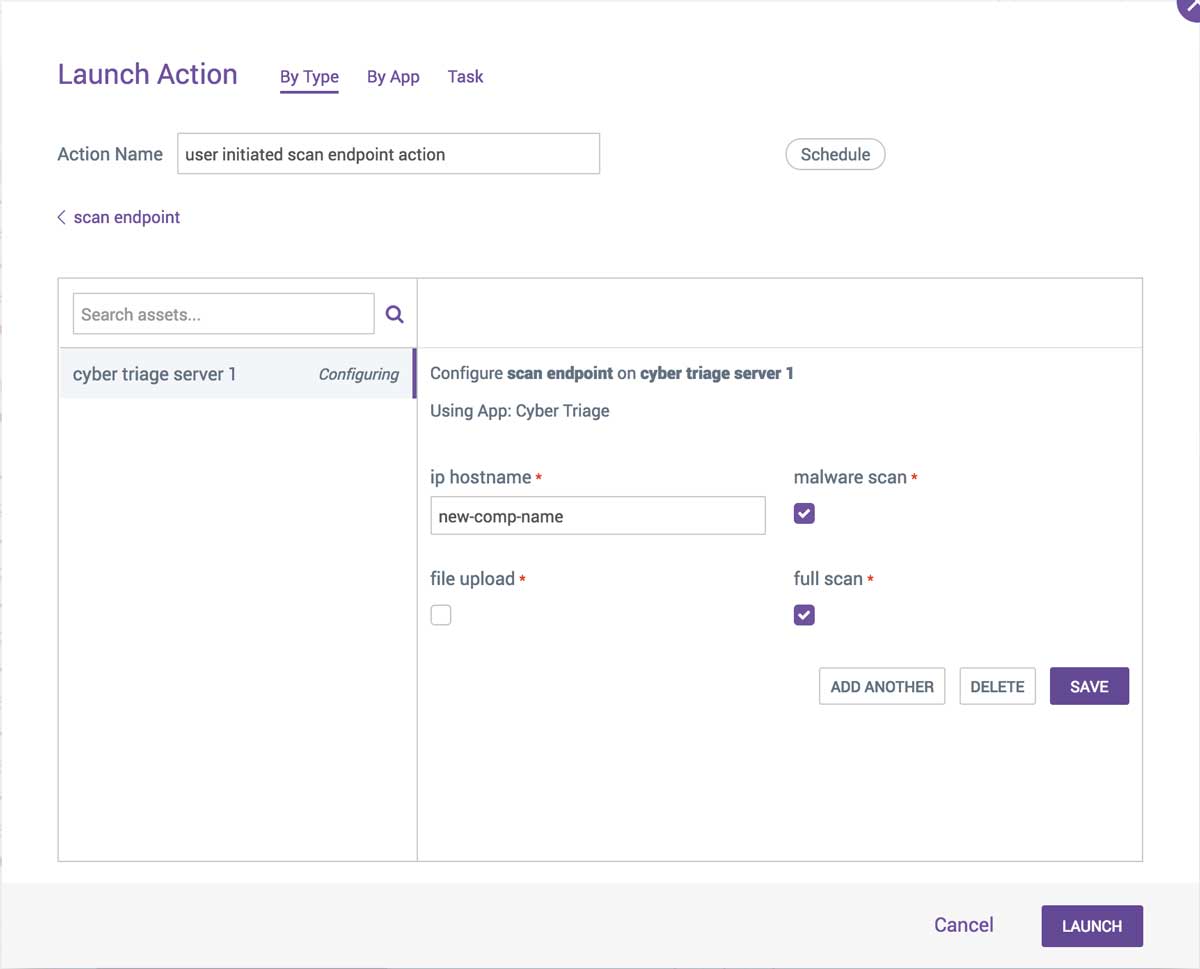
To use Cyber Triage as part of your playbooks, add the Cyber Triage “scan_endpoint” investigative action to it. The action requires an IP or hostname of the endpoint you would like to investigate. To have that value passed into the action, choose the field from the event that contains that data.
You can also choose to configure some of the analysis settings, such as uploading files to OPSWAT for malware scanning and whether to do a full or quick scan.
Faster Responses
When Cyber Triage is integrated with your other security applications, then you can more quickly investigate your endpoints and make some decisions about containment and resolution. If you are using Phantom and want to try Cyber Triage, use the form to get an evaluation copy of Cyber Triage. Email sales@cybertriage.com to upgrade that evaluation copy to the Team version.
Next up on the integration list is Splunk. If you want other integrations, send us an email at support@cybertriage.com.