When DFIR consultants or law enforcement get to a customer site, it can be hard to know where to start a digital investigation, or how to prioritize incident response collections. A common technique is to perform a high-level analysis on many computers and use the results to decide where to dig deeper.
The latest Cyber Triage release (2.7) makes that easier by allowing you to queue up a set of computers to start analyzing. You can then review the results and make decisions about where to start focusing.
This blog discusses this new feature included in the team version.
The Need for a Queue
Cyber Triage customers requested a queue in two situations:
- They integrated Cyber Triage with an orchestration system or SIEM, and a series of alerts were generated at nearly the same time. The number of alerts exceeded the number of simultaneous collections that Cyber Triage was licensed for. A queue was needed to ensure that each alert was properly investigated.
- They needed to scan 50 or 60 computers at a customer site to understand what was normal, what was suspicious, and other low hanging fruit. A queue allowed them to submit IP addresses or hostnames once and wait for the results to start coming in.
A queue has been a critical request for several of our largest customers, and we finally delivered it.
Using a Queue
The queue is only available if you have a team license of Cyber Triage. If you integrate the team server with your orchestration system or SIEM, the queue will simply just work. It is transparent and nothing special needs to happen from you.
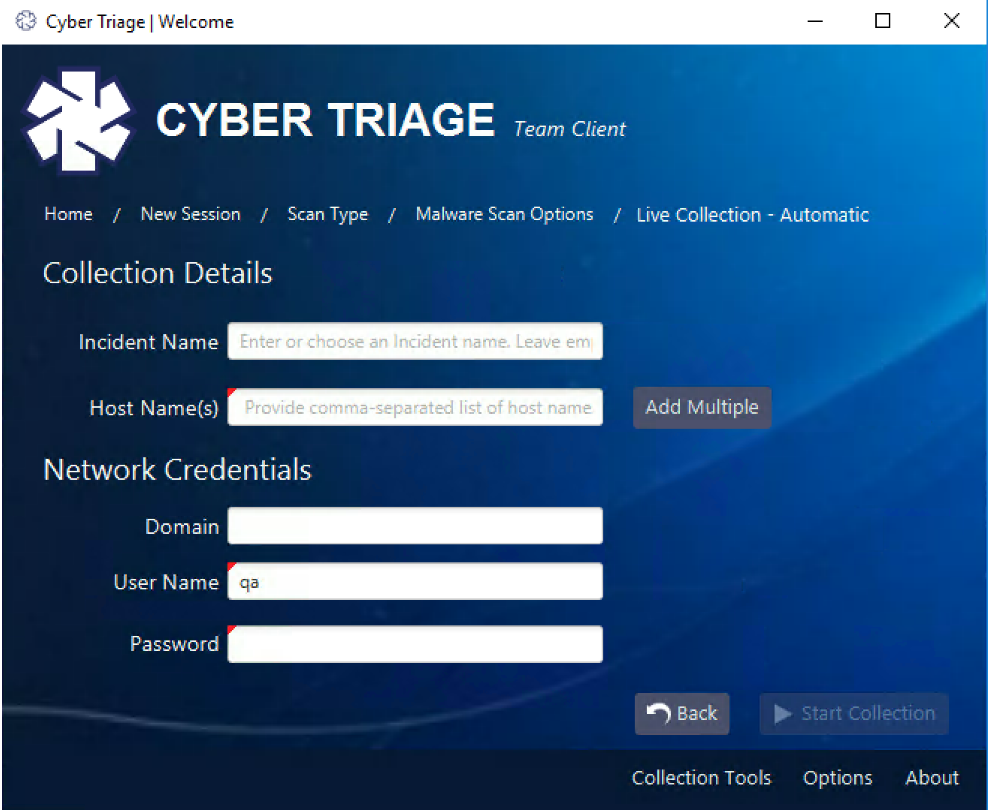
If you want to manually queue up a collection of hosts, create a “New Session” like you normally would. But, you’ll see a new “Add Multiple” button next to the “Host Name” field:
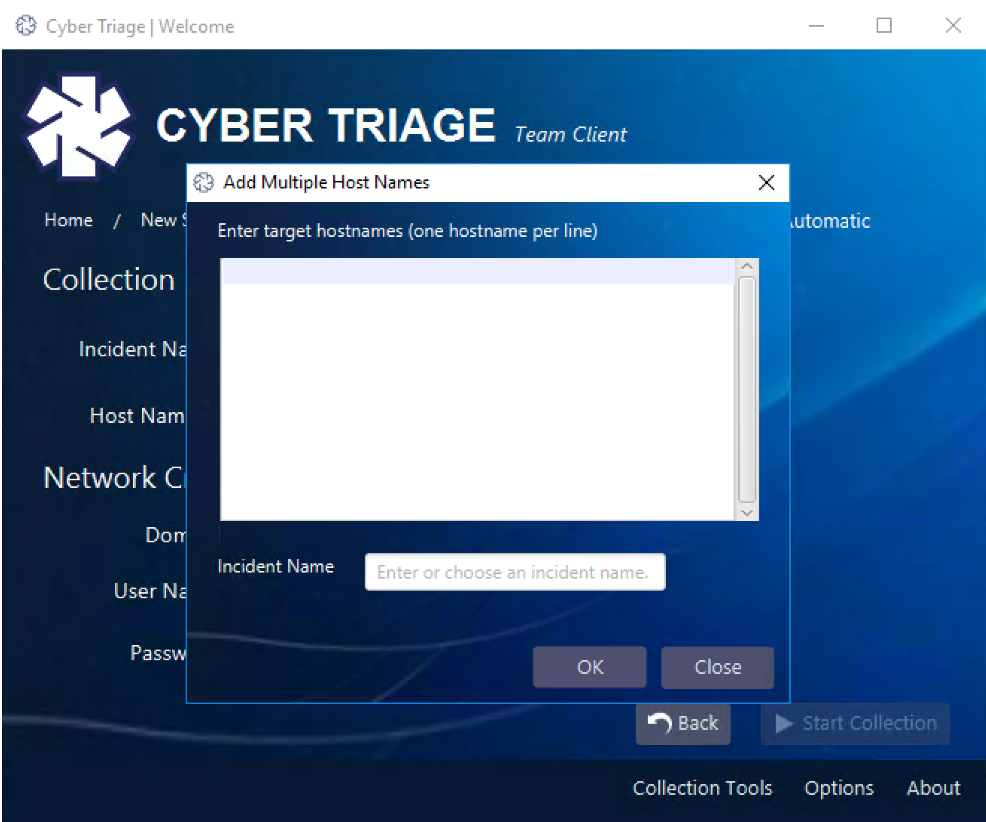
Pressing this will give you a dialog to enter a list of hosts, one per line:
You will also need to pick the “Incident Name” to group the results. This is to ensure that they are easy to find and correlate.
After you press “Start Collection,” it will validate the credentials. Then, it will bring you to the “Incident Dashboard” so that you can see when the hosts have been collected and analyzed.
Spend Less Time Waiting
If you have many hosts to analyze and don’t want to wait around for the results, click here to try out the latest Cyber Triage.
If you want to specifically try the queueing feature, send an email to sales@cybertriage.com. Ask us for the team version evaluation license, and we’ll get right back with you.