We are happy to introduce the new Cyber Triage Online File Reputation Service that reduces the configuration overhead for our users and gives them more information about collected files.
This service is used by the new 2.12 release and is part of our efforts to make front-line cyber responders as efficient as possible.
What Is the Online File Reputation Service?
The Cyber Triage Online File Reputation Service fuses data from multiple sources to provide a single answer about if a file is likely to be a threat or not. The first roll out integrates malware-related data from:
In the coming months, we’ll be incrementally adding additional features. For example, it will provide information about whether an item is common or rare. This allows Cyber Triage users to know if other computers in the world (without knowing which specific computers) also have this file.
The results look just like how they did before. You get to see the score assigned by Cyber Triage and how it came to that score:
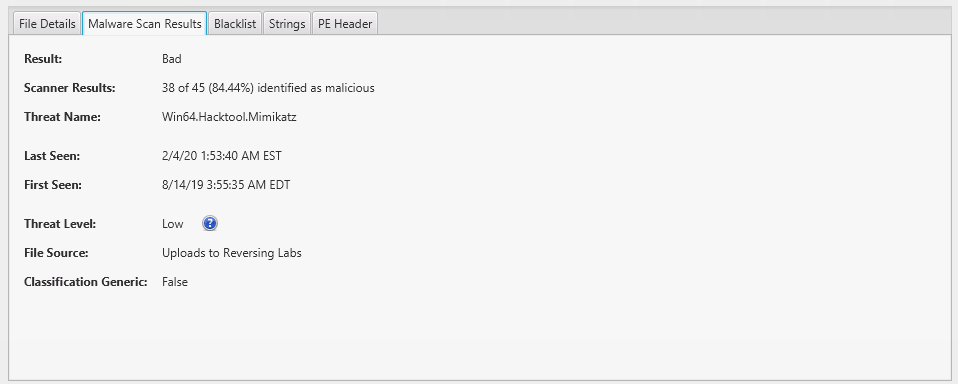
Why Is It Helpful?
This service is going to give Cyber Triage more comprehensive results with less setup. Specifically:
- NSRL: You no longer need to locally download the NIST NSRL and update it. Previous versions of Cyber Triage would use a local copy of the NIST NSRL and then directly query Reversing Labs if the file was not in the NSRL. Now, you don’t need to worry about downloading and configuring a local NIST NSRL.
- Frequency: One big challenge of DFIR is knowing what is normal on a system and it can be difficult to remember which files and processes are common. The first release of this service is focused on integrating the NSRL with ReversingLabs, but the next release will focus on providing frequency information. Over the summer, the service will return, for a given hash, if it is unique, rare, or common. This can help you determine if a suspicious file is unique to your host or just new to you.
- Fuzzy Matching: Sometimes a malware author slightly changes its malware and therefore changes its MD5. A future version of the service will return malware results for files that are similar to the one that you have using an algorithm such as ‘ssdeep’.
- Surge Usage: We get requests from consultants who need surge usage of malware scanning. This service will allow us to provide that without issuing new license files.
How To Use It?
When you upgrade to the next version of Cyber Triage (2.12), you’ll automatically start using it if you have a valid malware scanning license. If you previously configured a local copy of the NSRL, it will continue to be used until you disable it in the options panel.
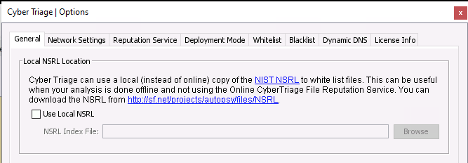
If you are installing Cyber Triage for the first time on a computer, it will use the service by default.
If you are using Cyber Triage Lite (the free version), then this whole topic is not relevant because it doesn’t provide malware scanning.
What If I’m Not Online?
We have some customers who do their analysis in an air-gapped environment and cannot reach the new service. If that is you, then you’ll need to rely on the local copy of the NIST NSRL to white list files.
We are working on a solution for air-gapped environments, but it’s not ready yet. The basic idea is that you’ll be able to export a text file with hashes from the host, move that to an Internet-connected computer, query the service to get results, and then move that text file back into Cyber Triage.
Conclusion
We are always working to make your job easier and this new service means you need to worry less about configuration and you’ll soon be able to get more insight about the frequency of a file.
If you are a Cyber Triage customer, check out the 2.12 release for this new feature.
If you are not a Cyber Triage customer, then fill out this form to try out our agentless DFIR solution to get better endpoint visibility.