We’ve gotten used to websites suggesting products based on our past purchases and browsing habits. Now, your DFIR tool can do the same (well, it will recommend artifacts and not movies or books).
The 2.9 release of Cyber Triage is out, and one of its features is the Recommendation Engine. We’ll focus on that in this blog post, but other notable things in this release include:
- Collection and analysis of WMI actions to detect malware persistence
- Encrypted communications between the collection tool and server
- Running the “malfind” module from Volatility on memory images
You can get the latest version from here.
The Winding Investigation Path
When investigating an endpoint, you are trying to answer one or more questions about it, such as if it has malware or suspicious user activity (see our blog series for more info on this process).
There is no single way to conduct an investigation, just like there is no single way to solve any problem.
Different examiners find different pieces of evidence in different orders. They (hopefully) all come to the same conclusion, but the path is different.
The trick to the process is finding the path. Most people start with some basic ideas, find some evidence and clues, make some assumptions, test some hypotheses by looking for more data, and continue to iterate based on what they find.
There are two common challenges:
- Forgetting: As you are hot on the pursuit of some evidence, you may notice some (you think) less important clues. When your current pursuit dries up, you need to try something else. Hopefully, you remember that clue from before because it could be relevant.
- Awareness: As you find one piece of evidence, you may not realize all of the implications of that evidence. You may not realize that the suspicious process also had a network connection open to a remote host and a search for other connections with that host will reveal other systems.
Both of these challenges result in longer and potentially less comprehensive investigations because not all clues are followed up on.
Making Investigations More Direct
We see a two-pronged solution to these problems.
- Forgetting Problem: Make sure it’s easy for you to tag something when you think it’s suspicious so that you don’t forget. Even better, add a comment about why you thought it was suspicious. This has been a long-term feature of Cyber Triage. You can mark any collected item as “Suspicious” to remind yourself to come back and look at it.
- Awareness Problem: Let your automated DFIR software remind you and make you aware of possible connections. Software is great at making connections and patterns. That’s the world of artificial intelligence and machine learning. If it can recommend books or movies you may like, it can recommend files you may like too.
Both of these solutions are now in incident response software Cyber Triage with the introduction of the Recommendation Engine.
Cyber Triage Recommendation Engine
Let’s take a look at the Recommendation Engine in Cyber Triage.
It runs when you mark an artifact, such as a process or startup item, as “Bad” or “Suspicious”:
When you mark the item, the Cyber Triage Recommendation Engine will search for related items and display them to you. Those will get displayed to you so that you can mark them as “Suspicious,” which is how it later reminds you to take a look at them. All related items will be shown, but only those that are not yet marked as “Bad” or “Suspicious” can be checked.
Here is an example after marking a Windows Scheduled Task as “Bad”:
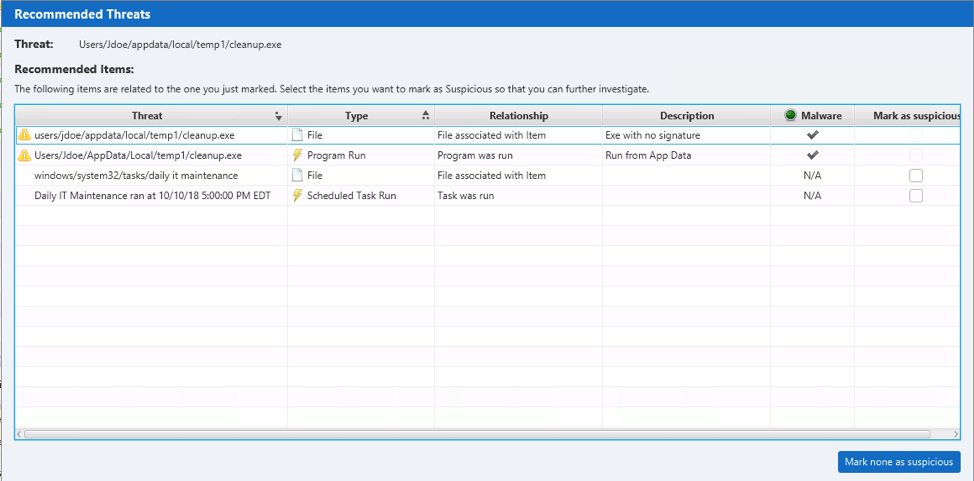
It allowed the user to mark the following as suspicious:
- Associated executable file that was run
- Associated “Program Run” entry
- The Scheduled Task file that may have timestamps about when it was created
- An event log that shows when the task was executed
These clues can point to when the task was created, reveal what happened after it ran, and make it easier to find the corresponding executable for additional analysis.
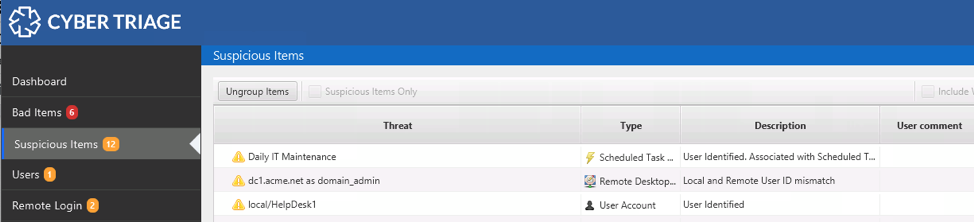
Suspicious items can be easily found at any time using the “Suspicious Items” menu on the left:
Example Recommendations
Let’s look at some example situations and what you may get for recommendations:
- You mark a process as “Suspicious” or “Bad.” You’ll likely see recommendations about:
- The executable file the process was loaded from
- Network ports and active connections
- User associated with the process
- Startup entries that may have launched that process
- Program run entries that may show when it was launched
- You mark a remote desktop login as “Bad.” You’ll likely see recommendations about:
- The local user
- The remote host
- You mark a program run entry as “Suspicious.” You’ll likely see recommendations about:
- A process if there is one running
- The executable file that was run
- The user who ran the program
- WMI Actions or Scheduled Tasks associated with the program
All of these recommendations ensure that you see all possible clues and remember them.
I Recommend You Try Cyber Triage
Speed is critical to incident response and following up on every clue is important to coming to the correct conclusion. The Recommendation Engine helps to get conclusions faster.
To try the latest version of Cyber Triage, you can download a free evaluation from here.