We love customer feedback and the Cyber Triage 2.13 release is all about solving challenges brought to us by our users. The first challenge is how to interface with malware scanning from air-gapped networks? The second challenge is about evaluation, what if you do not have great evaluation data? We offer solutions to both problems in this release.
To try the latest version of Cyber Triage, click here.
Offline Malware Scanning
Cyber Triage comes with a subscription to the Cyber Triage file reputation service, which is supported by the 40+ malware engines in Reversing Labs. This service provides a lot of value to our users because it gives them broad coverage to know if files on the system are malware.
However, not all of our customers are able to take advantage of this feature because they run Cyber Triage on an air-gapped network. Some are law enforcement or consultants who analyze disk images in an isolated lab. Others are security teams who work on classified networks. When they would see what Cyber Triage could do when connected to the Internet, they would always ask us how to get the equivalent functionality.
Now, they can. Cyber Triage has a solution for air-gapped networks. It looks like this:
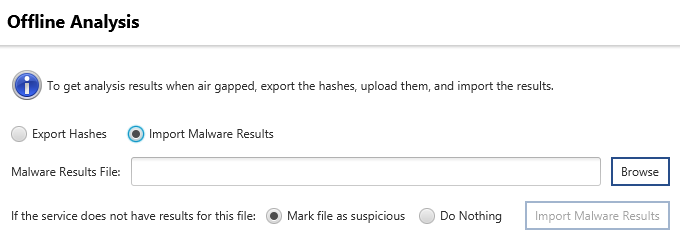
- You export the MD5 hashes of the collected executable files to a text-based JSON file that you can easily review before you copy it over the air gap.
- You upload the text file to a web page on the Internet. It will look up the hash values and send you a text-based JSON response.
- You copy the response back over the air gap and import it into Cyber Triage.
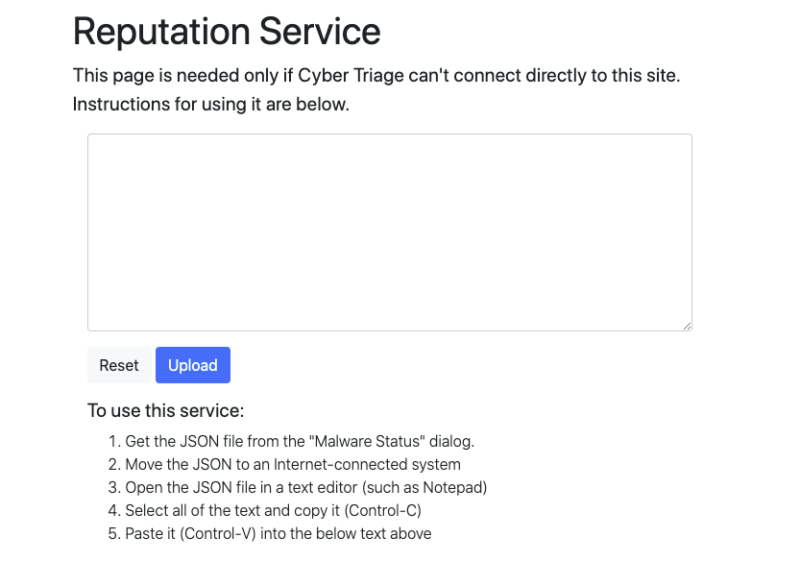
Voila. You have results from 40+ engines about the collected files if they were already uploaded by someone else. If the file has never been seen before, you can choose to have the file marked as suspicious so that you are aware that it is unique.
Evaluation Data
A second common request was for evaluation data. Apparently, most people don’t have copies of compromised systems lying around…
So, we made a small data set with a simple scenario and corresponding video. The scenario involves some PowerShell, backdoors, and living off the land.
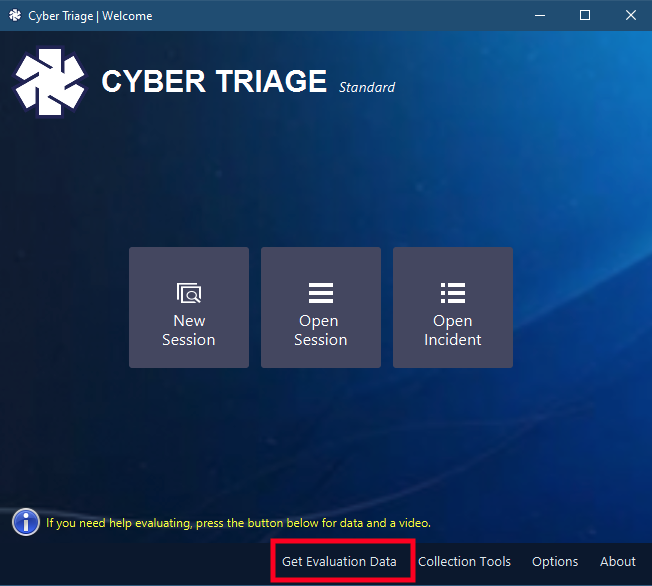
When you launch Cyber Triage with an evaluation license, you’ll now get a button on the bottom to get evaluation data.
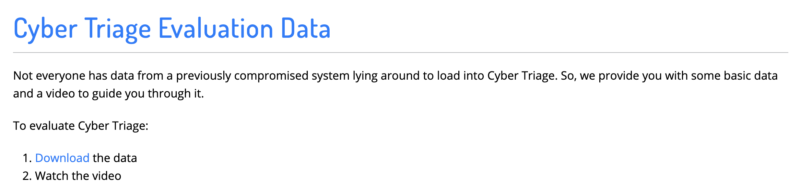
That will bring you to a webpage with data and a corresponding video that will guide you through it.
There’s even a challenge at the end with a couple of questions for you to answer.
We Listen!
Our goal is to make front line cyber responders more efficient and if you struggled with getting malware results from an air-gapped network or evaluating intrusion-related software, then try the latest version of Cyber Triage out.