The 1.6.1 release of Cyber Triage added a new automated analysis technique to make the life of an incident responder easier and more efficient. The new technique focuses on the programs that were run on the target system.
The motivation for analyzing these programs is to identify malware and tools that could have collected data from the system. With the increase of attacks that involve compromised credentials (versus malware), this information can be critical. The incident responder’s challenge is that hundreds of programs are run on computers and manually reviewing them is time consuming and error prone.
With the 1.6.1 release, Cyber Triage performs both fully and partially automated analysis on the programs that were run. Full automation comes from malware analysis using the OPSWAT Metadefender service. The new partially automated techniques help the responder identify the suspicious programs and ignore the rest.
Partial versus Full Automation
First, let’s define what we mean by fully versus partially automated. I call something fully automated when it requires no human interaction and partially automated when some human interaction is required. See my previous blog post on incident response automation for more details.
Fully automated is great from a time and resource perspective, but it is more likely to generate false positives unless the software knows everything (which is hard when responding to a computer that was not being monitored). Partially automated puts some pressure on the user to make some decisions, but hopefully the software is doing most of the analysis and the user is just approving the results.
We use both fully and partially automated techniques when analyzing what programs were run.
Finding Suspicious Programs That Were Run
Cyber Triage collects information about what programs were run by analyzing Prefetch, registry keys (using our open source rejistry++ C++ port of Willi Balenthin’s rejistry library), and other places. We then collect the executables using The Sleuth Kit to copy them even if they are locked (and not modify access times).
In previous versions of Cyber Triage, we applied an automated analysis technique on these programs to flag them if they were run out of an AppData or Temp folder (because malware often runs out of those places and we wanted to draw your attention to them). This worked great on many systems, but other systems had lots of false positives. In some rare cases, hundreds of them. In general though, it was only a few programs that were causing the false positives.
Many of the items had similar names and many of the files were deleted (so we couldn’t apply malware analysis techniques to the executable). For example, one system had over 5 entries in AppCompatCache for g2mui.exe being run, such as:
C:UsersjdoeAppDataLocalCitrixGoToMeeting1259g2mui.exe C:UsersjdoeAppDataLocalCitrixGoToMeeting2031g2mui.exe C:UsersjdoeAppDataLocalCitrixGoToMeeting2128g2mui.exe ...
Of the five files mentioned in the registry, only three of the corresponding files still existed. The files that still existed could be run through OPSWAT and considered safe if none of the 40+ engines thought it was malware, but what do we do with the other two entries?
Similarly, we had files such as this:
C:WindowsTEMP38D251C0-2A87-41E6-8B47-31E1BE1C9C3Edismhost.exe C:WindowsTEMP4F9E9A41-8988-4C7B-88A4-F4F04B8054EBdismhost.exe C:WindowsTEMPAB504037-EE8A-4EED-B784-6F7D3FF08E93dismhost.exe ...
These are from Windows Defender running. In this case, none of them had file content anymore. We needed a solution so that users could quickly review these programs and focus on the relevant items (which may have only 1 entry).
Helping the User
The latest Cyber Triage release continues to run the EXEs through OPSWAT and it also presents the first responder with suspicious programs to review. The interface allows the user to filter the types of programs and groups them based on similar names. The backend database provides information on other computers that also had that program. These features allow the responder to quickly get a high-level perspective.
For example, the previous examples about g2mui.exe and dismhost.exe are grouped so that the responder can see that 3 of the 5 g2mui.exe files came back clean from malware analysis and that none of the dismhost.exe files existed. Decisions can be made faster because they are grouped together.
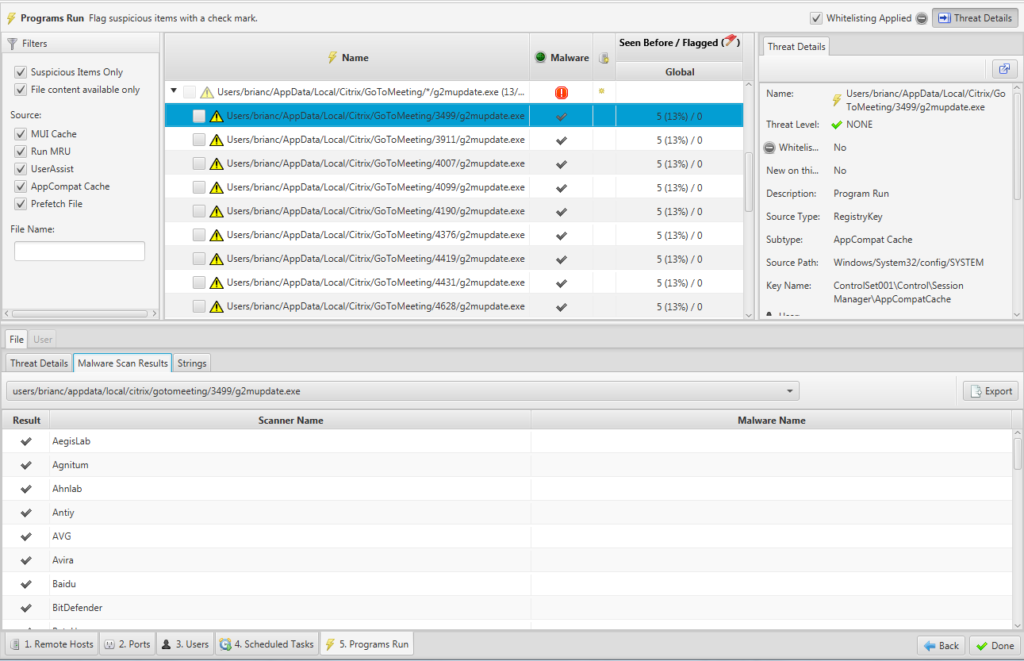
You can also use the filters to focus only on executables that were not deleted, which are obviously easier to draw conclusions about. These changes make it much easier and faster to review what programs were run on a suspected system during a triage.
Better Review Your Programs
Get a free eval copy of Cyber Triage so that you can more efficiently review programs and user activity in your environment. Our agentless approach makes it easy to try Cyber Triage and deploy it in your environment. Contact us to get a free evaluation copy.



