We’re super excited to announce the massive 3.10.0 release and all of its new features. This blog post covers the high-level basics of key new features and we’ll have follow on ones in the coming weeks to dive into them in more detail.
You can also attend the webinar on May 8 to see a live demo and ask questions.
You can also watch our webinar from May 8 to see the live demo.
This post covers:
- Analyzing Linux systems
- Analyzing domain controllers for account take over
- Fuzzy malware scanning with ImpHash
- Labels and an Excel Report
Analyze Linux Systems
You can now quickly analyze Linux systems, just like you can Windows.
Attackers don’t focus on only Windows systems and therefore you need to be able to investigate more than just Windows.
What We Did
We have added support into Cyber Triage for common Linux distributions! This is likely our oldest feature request on the books.
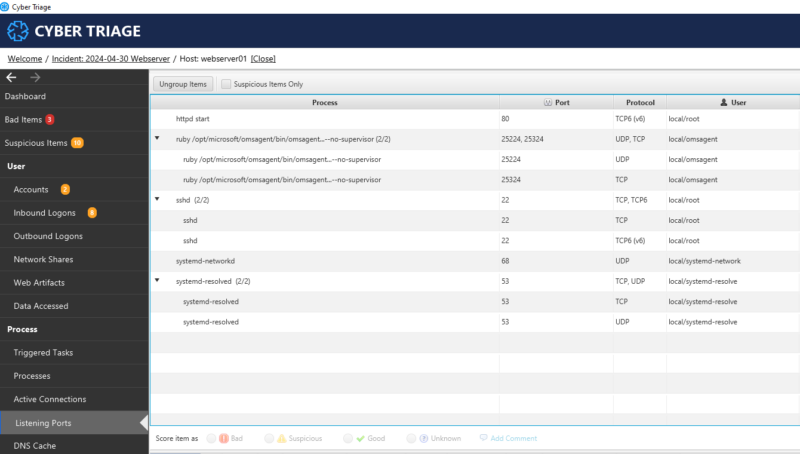
As of 3.10, you can collect from a Linux host using UAC and import the resulting files. Cyber Triage will then parse those files to create the high-level artifacts, such as user accounts, inbound logons, processes, and triggered tasks.
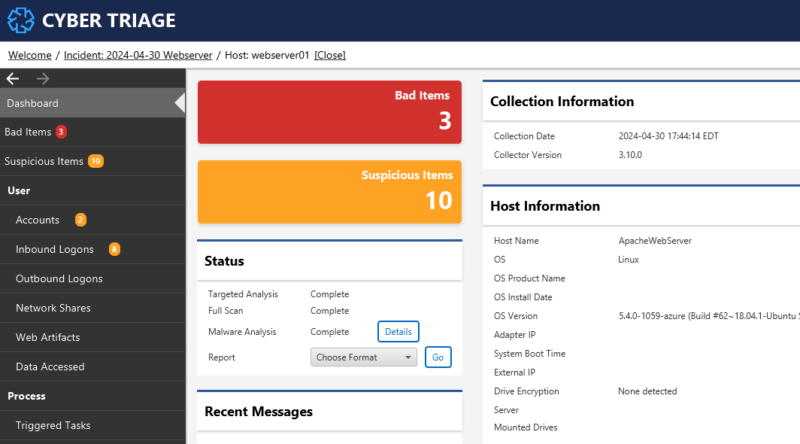
Cyber Triage will also apply its scoring to the items to detect anomalous OS activity and upload executables for malware scanning to Reversing Labs.
How To Use It
Adding a Linux host is as easy as:
- Collect from a live Linux system using UAC (disk images are not yet supported)
- Import the UAC collection as a “Add Host” option
- Cyber Triage will parse the various source files to create artifacts.
- The artifacts will be analyzed in the backend pipelines
- You can then view the results and focus on bad items, jump to timelines, and navigate the file system.
Analyze Domain Controller Logs
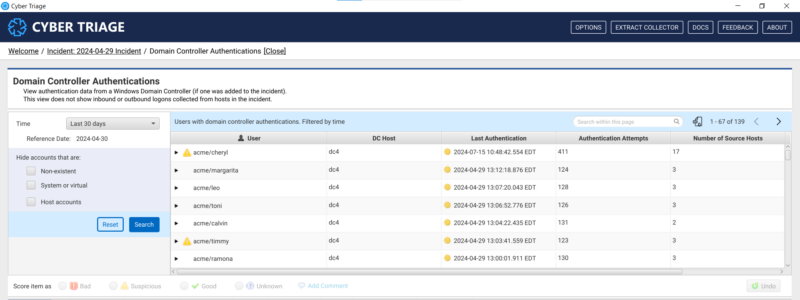
You can now quickly leverage domain controller authentications to identify compromised accounts and track their movements.
Domain Controller event logs can show each host that a user attempted to log into. As you are scoping an incident and know of a few initial systems that are impacted, the domain controller can quickly help you identify:
- What other systems a compromised account was active on
- What other accounts had anomalous behaviors
- If there were spray attacks, Kerberoasting, and other authentication attacks
But, the event log data is difficult to manually analyze and automated systems are needed to quickly identify which users and hosts to focus on.
What We Did
Cyber Triage 3.10.0 added three key concepts to make examining domain controllers easier:
- The Kerberos and NTLM authentication events are now parsed from the Security log.
- New scoring techniques were applied to detect anomalous user behaviors and attacks such as Kerberoasting.
- A new incident-level UI that shows the authentications between hosts even if those hosts have not yet been collected and analyzed.
Now, you can quickly review the authentication data and identify anomalous users and hosts.
How To Use It
To review domain controller data:
- Collect data from the domain controller like you would any other system. You can start the collection from an EDR, Powershell, or manually.
- Import that data into a Cyber Triage incident
- After the data is ingested and analyzed, open the “Domain Controller Authentications” interface from the Incident Dashboard

- You can then focus on the accounts that had the most destinations in the past 30 days and dive into where they were going.
Fuzzy Malware Scanning with ImpHash
You can now get malware information for a file whose hash is unknown and you don’t want to upload the content.
Attackers often make unique executables for each target so that it is hard to detect them as malware because the SHA256 hash value changes each time. The changes made by the attacker are often insignificant, but mean that responders and forensic examiners must upload files to be scanned.
Some teams are uncomfortable uploading file content and their only options are then to use basic static analysis techniques.
What We Did
Cyber Triage can now use the ImpHash fuzzy matching algorithm to determine if a file is similar to previously detected malware. This can be done without needing to upload content for a full analysis.
ImpHash is a hashing algorithm that does not look at every bit in an executable. It focuses on the import table, which attackers do not typically change. The import table lists out which libraries that an executable depends on.
It is much more work for an attacker to generate unique ImpHash values for every victim. Therefore, an attacker’s tools often all have the same ImpHash values.
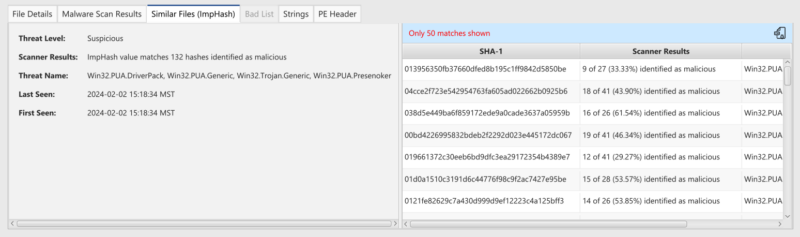
If a file’s SHA256 hash value is not already in the Reversing Labs database, then you can now choose to query its ImpHash value. That query will return a set of files that share the same ImpHash. Those files can then be reviewed to determine if any were malicious. If they were, then this file could be too.
How To Use It
You can enable ImpHash when you add a host to the incident. You can choose ImpHash instead of uploading unique files (though we still recommend uploading if you can).
Cyber Triage will use ImpHash as needed and score the files accordingly. When a file is flagged from ImpHash, you can see the similar files:
Add Labels to Artifacts
You can now annotate why items are relevant using labels and easily copy them into your final report using a new Excel report format.
This allows you to easily record what you learn as an investigation unfolds. The labels allow you to record why something is relevant and then include it in the final report.
What We Did
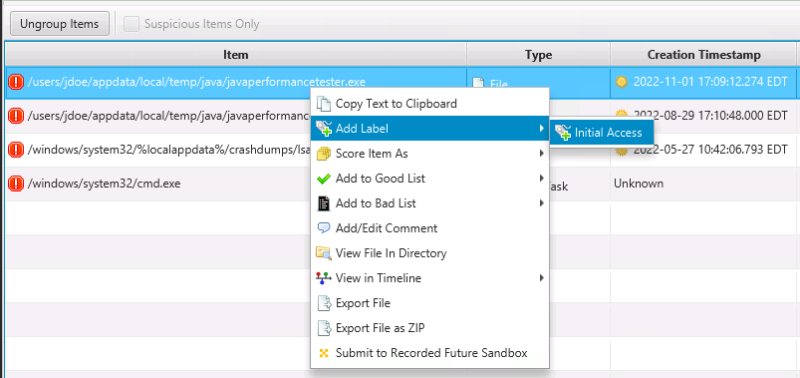
The 3.10 release added labels so that you can describe “why” an item is relevant to the incident. For example, you can add a label such as “Initial Access” or “lateral movement” to your bad items.
The labels are very flexible and can also be used to group related items.
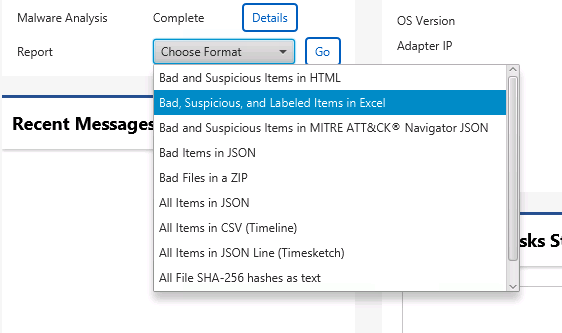
To also facilitate report writing, we also added a new Excel report that makes it easier to copy data into Word or Google Docs. The Excel format is easier to manipulate than the existing HTML report.
How To Use It
To add an existing label to a Bad or Suspicious item, right click on it and choose “Add Label”. You need to create the label names before you first use them.
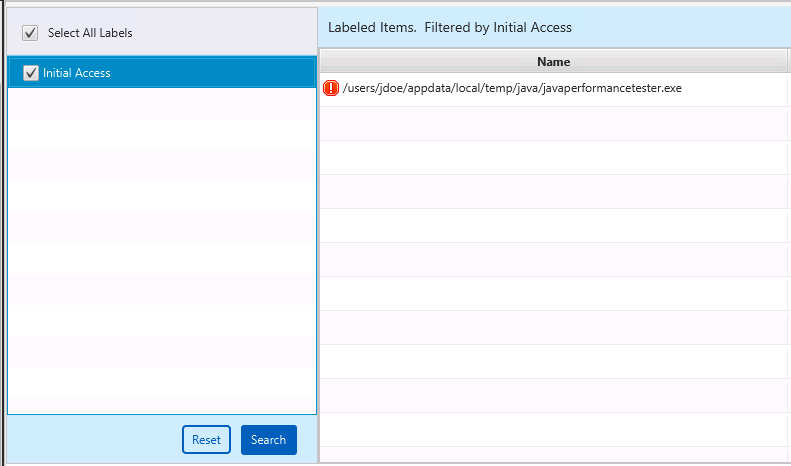
You can use the “Labeled Items” section at the bottom to see all items with a label.
To make an Excel report, choose “Bad, Suspicious, and Labeled Items in Excel” from the list of report options.
Conclusion
Digital investigations can be hard and we are always working on features to make them easier and make you more efficient. This release was big with a new OS, new major data source type, and new malware detection methods.
If you are already a customer, you should have the download link in an email. If you aren’t, then try out our 7-day free evaluation.