How to explain jump lists forensics to an old-school detective:
Jump lists are fingerprints. They connect people to places and things.
Jump lists forensics?
Fingerprint powder.
From basic facts to the best tools, this blog post delivers the latest on how (digital) sleuths use this Windows artifact.
Jump to…
What Are Jump Lists?
Why Do Jump Lists Forensics?
Technical Basics of Jump Lists
Forensic Basics of Jump Lists
Tools for Jump Lists Forensics
Jump Lists Forensics with Cyber Triage
The New (Jump List) Detectives
What Are Jump Lists?
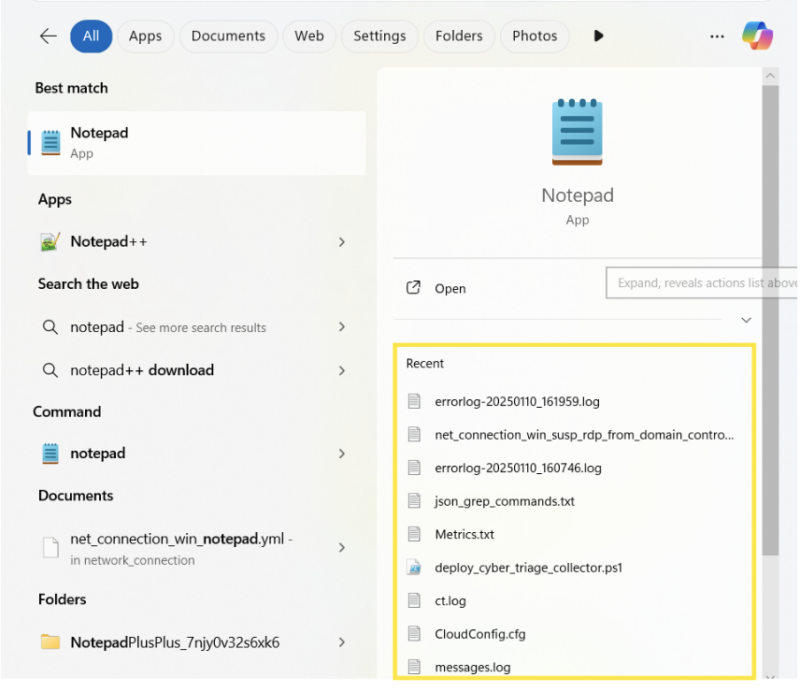
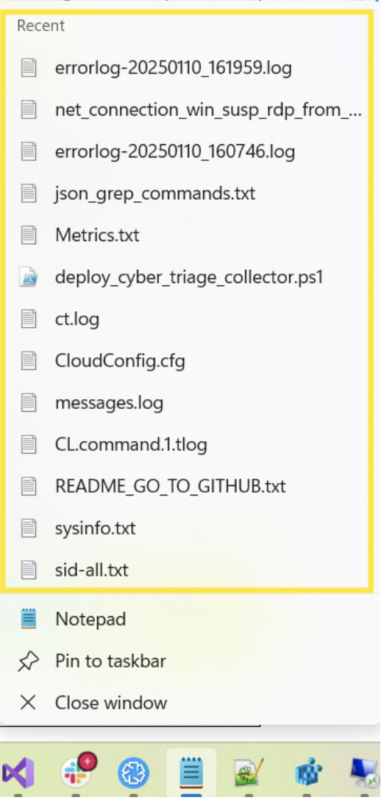
Jump lists are data artifacts that record user interactions with applications and files. They give you easy access to recently and frequently used files, folders, and applications. You can access jump lists via the Start menu or by right-clicking taskbar icons:
Jump lists were introduced in Windows 7. They are only supported by the desktop device family.
Why Do Jump Lists Forensics?
Jump lists help investigators understand user behavior and system activity. As DFIR expert Chris Ray explains, “Jump lists are valuable when you need to figure out what a user has accessed. This is especially useful in ransomware and insider threat investigations that involve data exfiltration.”
Jump lists forensics are useful for:
- Identifying files a user has accessed (most often with a last access time)
- Identifying applications used to access files
- Identifying the frequency files have been accessed
- Providing evidence of files no longer exist on the system
Jump lists are one example of what we call “Data Artifacts.” Prefetch and MUICache are other examples. Classic DFIR focuses at this level, learning subtle differences between artifact types and approaching investigations Data Artifact by Data Artifact.
We recommend thinking about investigations using higher-level computing concepts instead. Brian Carrier, author of File System Forensic Analysis, explains: “You don’t care about jump lists. What you really want to know is what users have accessed what resources at what time. This is a higher-level concept that cuts across multiple Data Artifact types. This is about all the ‘Data Accessed’”
Learn how to use higher-level concepts for more efficient investigations from Brian.
Technical Basics of Jump Lists
There are two types of Jump Lists:
- Automatic Destination Lists
- Custom Destination Lists
Here’s a technical overview of each:
| Automatic Destination Lists | |
|---|---|
| Definition | System-generated lists tracking files recently accessed by an application |
| File Location | %AppData%\Microsoft\Windows\Recent\AutomaticDestinations |
| File Extension | .automaticDestinations-ms |
| File Format | Microsoft Compound File Binary (CFB) |
| Key Info | Target file paths accessed, last accessed timestamp, associated application ID, and file accessed frequency |
| Custom Destination Lists | |
|---|---|
| Definition | Application-specific lists manually defined by developers |
| File Location | %AppData%\Microsoft\Windows\Recent\CustomDestinations |
| File Extension | .customDestinations-ms |
| File Format | Binary data of sequential list of MS-SHLLINK (link files) |
| Key Info | Target file paths accessed and associated application ID |
Forensic Basics of Jump Lists
Here’s how investigators use jump list components and features:
Target File Accessed
| Definition | Forensic Relevance |
|---|---|
| The file name and path of the file accessed. These files are grouped by the applications that they are accessed with. | Provides evidence a user has accessed the specified file. The referenced file does not need to exist which can help prove a file once existed and the user had access to it. |
Application ID
| Definition | Forensic Relevance |
|---|---|
| The jumplist filename is a hash-like value of the Application IDs (App IDs) used to open the target file. | The hash-like value of the App ID can be used to infer the application used to open a file. This can serve two purposes:
|
| More on Application IDs
For example, the file 1bc392b8e104a00e.automaticDestinations-ms is for Microsoft Remote Desktop Connection (mstsc.exe). 1bc392b8e104a00e is the AppID representing an installed app, and it’s identical across all hosts where the app is installed. Default lists can be used to map these IDs to an application. AppIDs are calculated by default on the program’s the full path. However, that can be changed by programs as well. Here’s an excellent resource on AppIDs and how to calculate the hash-like value seen in jumplists. |
Last Accessed Timestamp
| Definition | Forensic Relevance |
|---|---|
| AutomaticDestination entries will have a timestamp that represents the last time it was accessed by a user within the given application. | Access timestamps can be used to show when a user had access to a file and build out timeline activity. |
Usage Frequency Counters
| Definition | Forensic Relevance |
|---|---|
| Jump list entries can include a record of how often a file or task has been accessed. | You can use usage levels as context or to prioritize. High-usage files can be used to understand baseline activity. Low usage files may indicate unusual (AKA suspicious) activity. |
LNK File Details
| Definition | Forensic Relevance |
|---|---|
| Both jumplists contain details for the LNK file that point to the target file. More details can be found here. | LNK file details can provide information about the target file creation and modify dates which can be useful when the file no longer exists on the system. |
Tools for Jump Lists Forensics
There are many tools for parsing jump list files. Each has advantages. Some of the most common tools investigators use for jump lists forensics are:
Autopsy
Autopsy is open-source forensic software you can use to correlate jump list data with other evidence in a unified case view. Autopsy was created by Brian Carrier, author of File System Forensic Analysis. It’s free, open-source, and can parse much more than just jump lists.
JLECmd
JLECmd is a command-line tool specifically for jump list analysis. JLECmd was created by Eric Zimmerman, a former FBI agent and current SANS instructor. It’s free, open-source, and provides the most forensic details from jump lists as it’s a specialized tool specifically designed to handle them. He also has a detailed blog post on how to parse jump lists here.
Cyber Triage
Cyber Triage is DFIR software that automatically collects and analyzes jump list data. It prioritizes data by how suspicious it is and shows associated data worth review. Like Autopsy, Cyber Triage was created by Brian Carrier. Its main advantage is that it abstracts away data artifacts and provides high level information artifacts like data access instead of jump lists and focuses on the highest value data along with scoring and automation to help investigators focus on the data that matters the most.
Jump Lists Forensics with Cyber Triage
Now let’s take a look at how to do jumplist forensics with a newer tool, Cyber Triage.
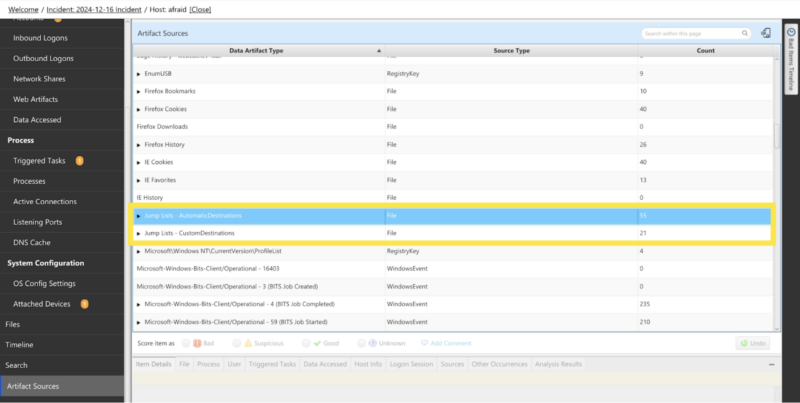
Cyber Triage parses both jump list types (customDestination and AutomaticDestination) to create Data Access artifacts:
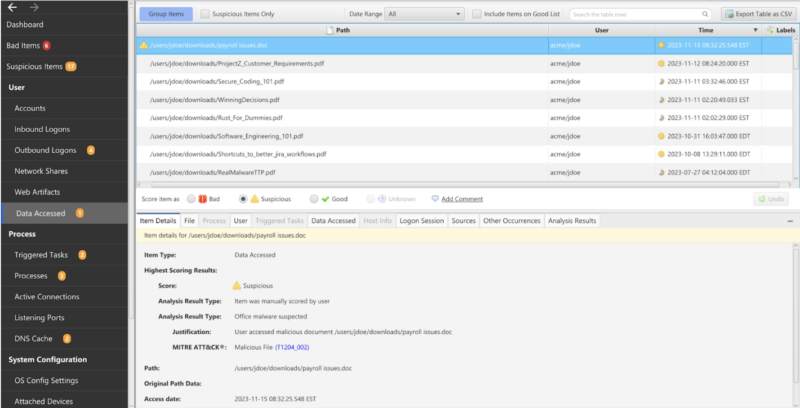
Cyber Triage shows what users have accessed files at what time:
Cyber Triage view of Data Accessed artifacts:
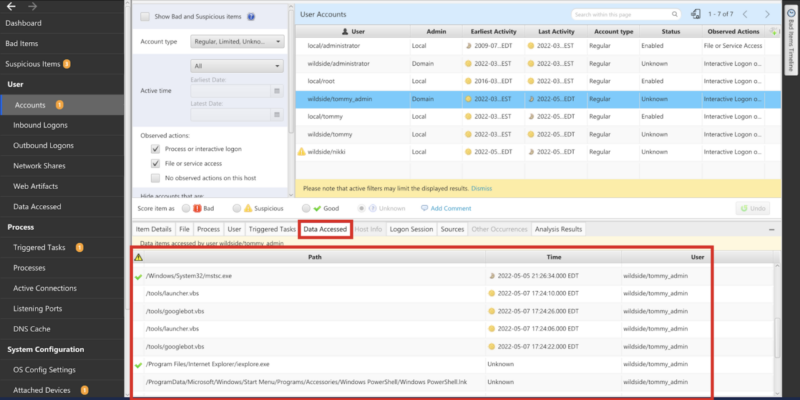
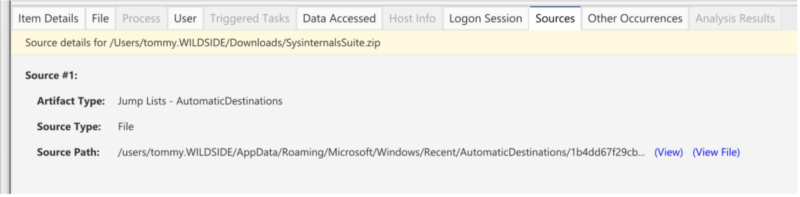
In this case an automaticDestination jump list.
Advantages of Cyber Triage for jump list forensics:
- Cyber Triage collects the associated files. This is useful for cases where you need to do further analysis on the documents a user opened.
- Cyber Triage identifies other suspicious things. Cyber Triage applies heuristics and malware scanning to associated files. For example, if a user opens a phishing email and runs a malicious Word doc, the software will check for malicious macros and show the user opened the bad Word doc.
- Cyber Triage shows you before and after. Artifacts are put into the software’s host timeline. This allows you to see what happened before and after a user access event
- Cyber Triage integrates with the Recorded Future Triage sandbox. Cyber Triage allows you to upload suspicious files to our sandbox to get full reports on what occurs when the file is opened.
The New (Digital) Detectives
Okay. You’ve paid your dues. You know the DFIR deal with jump lists. The next step isn’t more trees, it’s the forest. Let Cyber Triage take care of the details. The MUICache, ShimCache, and… jump lists of the world.
Download a free 7-day trial version today.