This post explains the technical aspects of jump lists for IT, cybersecurity, and digital forensics professionals.
It answers questions like:
- What is jump list cache?
- How are jump list caches structured?
- What applications use jump lists?
So if you want to understand the details of this data artifact, you’re in the right place.
Let’s get started.
Jump to…
What Is A Jump List?
What Is Jump List Cache?
More on the Forensic Value of Jump Lists
Where Are Jump List Caches Stored?
How Are Jump List Caches Structured?
How to Access Jump Lists
What Applications Use Jump Lists?
Top Jump List Analysis Tools
Analyzing Jump Lists with Cyber Triage
How to Do Jump List Analysis in 2025
What Is A Jump List?
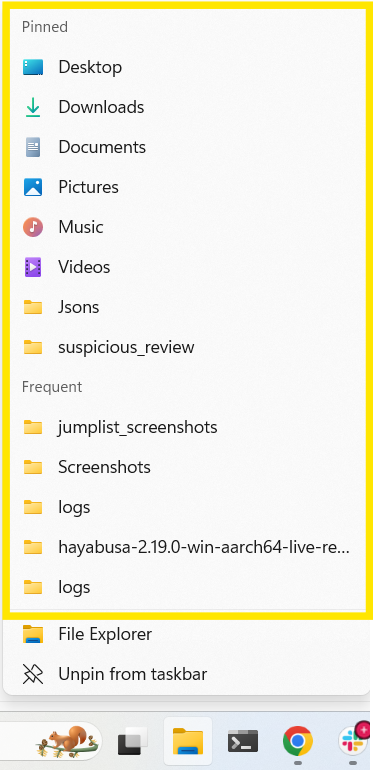
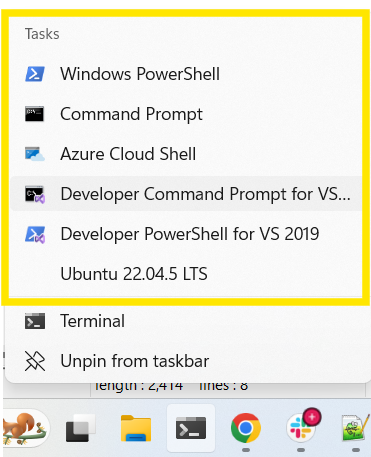
A jump list is a system-provided menu that gives quick access to recently and frequently opened files on a per-application basis. Additionally, jumplists provide users with easy access to common tasks or custom actions if an application chooses to provide such features. You can access them via the Taskbar, Start menu, or keyboard shortcut. Microsoft introduced jump lists in Windows 7, and it is still supported by the desktop device family.
Jump list menus display:
- User interactions with files, folders, and websites
- User executions of common application tasks
- User executions of custom-defined actions specific to an app
 |
 |
|
The user behavior displayed on the jump list menu varies by app. This is because each app defines jump list activity differently. |
|
What Is Jump List Cache?
A jump list cache is the data used to create the jump list menus. It contains information like paths to recently accessed files, timestamps for file access, number of times files were accessed, and the applications used to access files. This data can be valuable for digital investigators when they want to understand user activity on a system.
More on the Forensic Value of Jump Lists
DFIR expert Brian Carrier explains: “Jump lists provide insight into understanding what files a user has accessed, how often files have been accessed, and when they were last accessed. This can be useful when trying to establish user behavior patterns which can be correlated with evidence from other data artifacts.”
Where Are Jump List Caches Stored?
Jump list cache data can be stored in two different locations depending on the functionality implemented in an application’s jump list.
| Where Jump List Caches Are Stored |
|---|
| %appdata%\microsoft\windows\recent\automaticdestinations\*.automaticDestinations-ms |
| %appdata%\microsoft\windows\recent\customdestinations\*.customDestinations-ms |
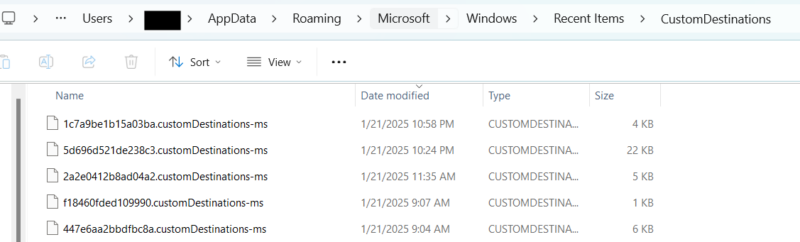
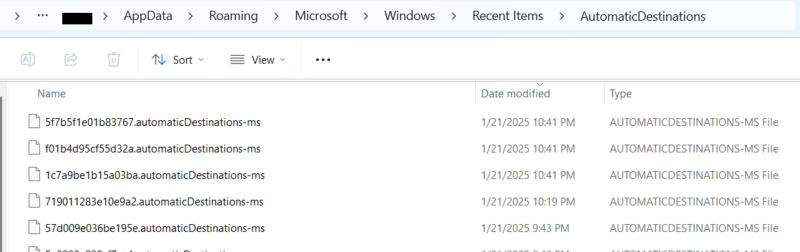
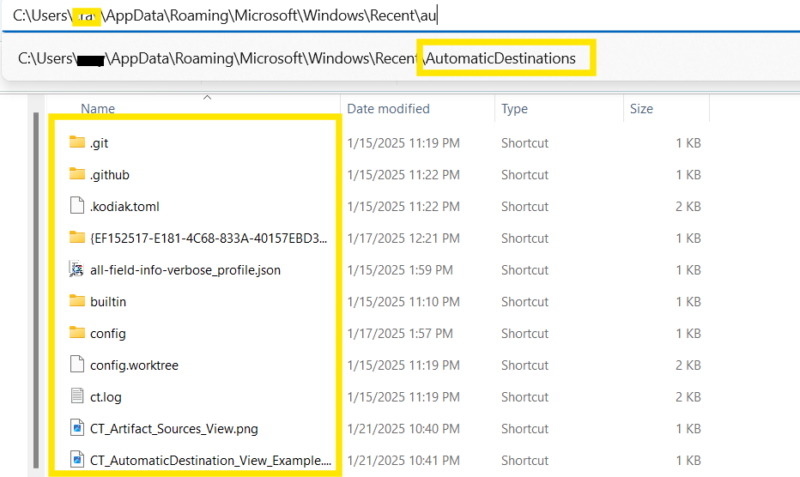
It’s important to note that you cannot manually navigate to the jump list cache from Windows Explorer — even with settings that allow you to view hidden or system-protected files. To get to the jump list locations you must type in the automaticDestinations/customDestination folder into the address bar.
How Are Jump List Caches Structured?
There are two types of jump lists — custom destination lists and automatic destination lists — and their caches are structured differently.
Custom Destination Lists
The structure of custom destination lists is simple compared to automatic destination lists. They are essentially binary files with a bunch of MS-SHLLINK files concatenated together. Each link file represents an entry in the jumplist. This type of jump list has the file extension “customDestinations-ms.”
Here’s how custom destination list data looks in a popular forensic tool, JLECmd:
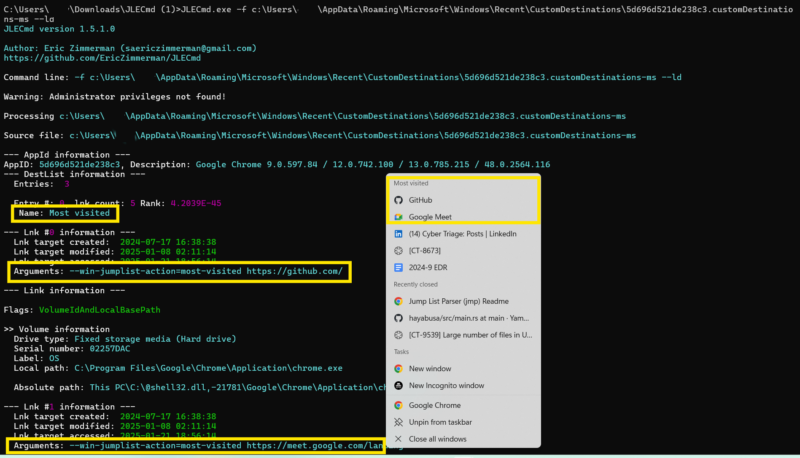
Custom destination lists are defined by the developers who created a given application, so what they contain differs by application. That said, the data stored is the kind normally found in a link file, such as:
- Jumplist file creation and modification date
- File creation and modification date for target file
- Lnk file creation or modification date
- Application based off file name
- Target arguments for tasks
- Target file path
- Target file size
Automatic Destination Lists
The file format of automatic destination lists is complex. The jump list data is stored in a Compound File Binary (CFB) format. This format is similar to a file system with storage objects (directories) and stream objects (files). A special “folder” called “DestList” contains the most important information, including the lnk files. This type of jump list has the file extension “automaticDestinations-ms.”
As the name suggests, these jump lists are “automatically” generated by Windows. They can only handle listing recent items or most frequently used items as defined by Microsoft. They have all the data custom destination lists have, plus:
- Last accessed date
- Frequency count
- Pinned status
Here’s how automatic jump list data looks in a popular forensic tool, Cyber Triage:
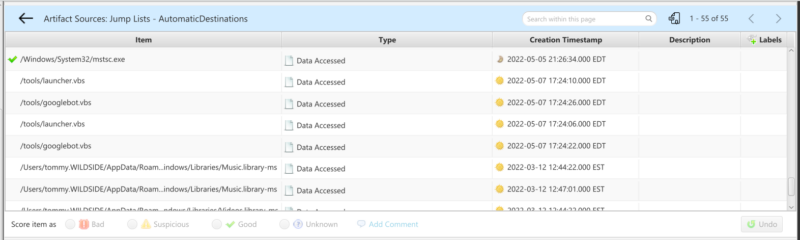
For a detailed breakdown on parsing both types of jump lists, check out this in-depth blog post.
How to Access Jump Lists
Accessing jump lists in Windows is straightforward.
Here’s how:
| Method | Access Instructions |
|---|---|
| Taskbar | Right-click the application’s icon in the taskbar to see the jump list. If it’s not on the Taskbar, right-click its icon and select “Pin to Taskbar.” |
| Start Menu | Search for the application in the Start menu. Hover over or right-click to see the jump list. |
| Keyboard Shortcuts | Press Win + Alt + [Taskbar Number] to open the jump list on a pinned application. Ex: If it’s the third icon on the taskbar, press Win + Alt + 3. |
What Applications Use Jump Lists?
All Windows desktop applications can use jump lists however, not all applications choose to.
Here are the categories and examples of each:
| Application Type | Examples |
|---|---|
| Default Windows | File Explorer, Notepad, and Microsoft Office Programs. |
| Third-Party | web browsers, media players, and messaging platforms. |
Top Jump List Analysis Tools
Here are four of the best open-source and commercial tools for the forensic analysis of jump lists.
| Name | Description | Download |
|---|---|---|
| JLECmd | JLECmd was designed for jump list analysis. It rapidly parses and decodes Jump List files, providing detailed insights into user activity on Windows systems. | Free Download |
| Autopsy | Autopsy is an open-source digital forensics platform that can correlate jump list data with other types of evidence within a unified case management view. Autopsy supports file system analysis, keyword searching, and timeline generation. | Free Download |
| FTK | FTK allows investigators to easily acquire, mount, and explore jump lists. It has a simple interface for manual review of Jump List contents. It also allows investigators to view and extract jump list files from disk images or live systems. | Free Download |
| Cyber Triage | Cyber Triage automatically collects digital evidence (including jump list data), analyzes, and scores according to its level of suspicion. | Free Trial |
Which tool should you use? Here’s what DFIR expert Chris Ray recommends: “There are many tools that can do the job. It comes down to knowing what the tool can and can’t do. If you don’t know how the tool works, stick with what you know. You can always verify findings with multiple tools.”
Analyzing Jump Lists with Cyber Triage
Cyber Triage differs from other forensic tools that parse jump lists because it abstracts away lower-level details not needed for triage investigations. The idea is to not overload the user with information so they can more easily review data and later drill down as artifacts become relevant to an investigation.
In the case of jump lists, the core information is represented in the form of a “data accessed” artifact. This category of artifact is used to focus on what files and folders users have accessed on a system.
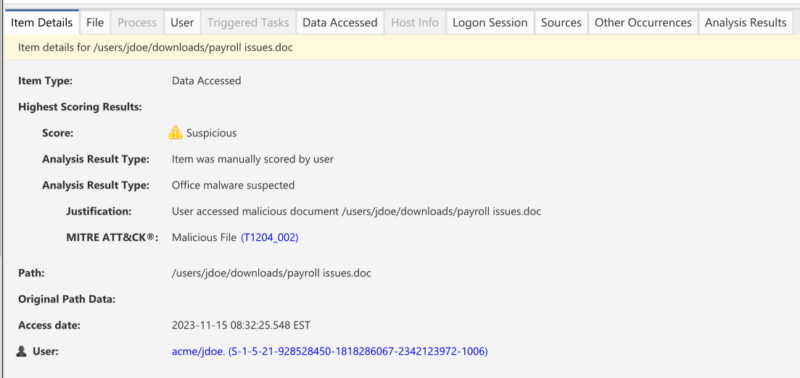
When you have a data accessed event that is of interest, you can then pivot to other related information that may be of interest: such as associated user, file information (malware scan status), logon sessions, source of the artifact, and other hosts that may have the same artifact on it. Furthermore, you can jump to the timeline to see what happened before and after that event.
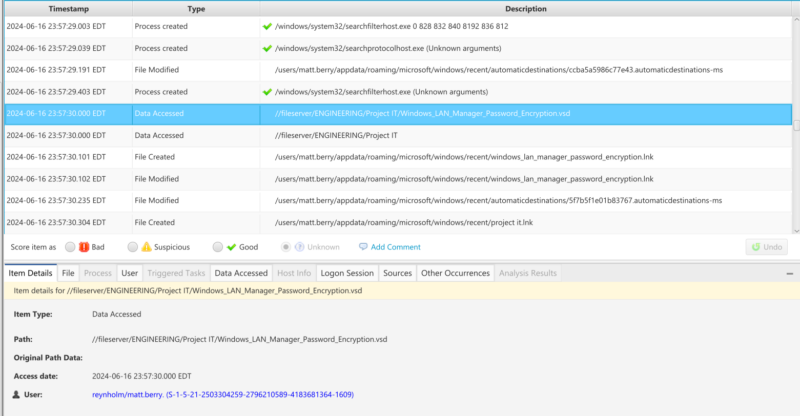
The sources tab will provide insight into where the artifact came from — in this case the jump list — and allow an investigator to do additional analysis on the source file if needed.
For example, the user could export the jump list of interest and run JLECMD.exe to get the full details to do a more deep dive forensic analysis.
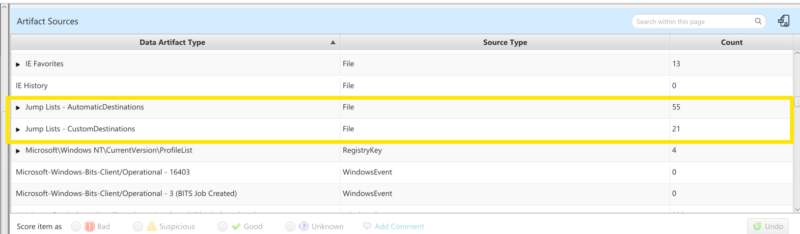
You can also focus in on a specific data artifact type if that is your standard workflow process by viewing the Artifact Sources table. Here you can see both jumplists entries and their associated information artifacts that we create.
How to Do Jump List Analysis in 2025
If you were wondering, “What is jump list cache?” hopefully, you have your answer now (and more). The truth is, digital investigators are better off not memorizing the technical details of different data artifacts like jump lists.
That’s what software is for.
Cyber Triage is just such a tool. It automatically collects evidence, analyzes, and prioritizes items by how suspicious they are.