You can now use Yara signatures in Cyber Triage to search endpoints for new or advanced malware during incident response. Yara allows malware researchers to define binary patterns that can be easily shared. When you configure Cyber Triage with Yara rules, they will be applied to all collected files, such as startup items and scheduled tasks.
Yara is one of two major features in the most recent 2.2.0 release of Cyber Triage. The release also includes the integration of Volatility for memory forensics. Check our blog next week to learn more.
Why Yara?
Everyone knows that antivirus and antimalware tools are not perfect. They may not recognize malware that just came out or your organization could be attacked with custom malware written just for you. That’s where Yara comes in.
When new malware breaks out consultants write Yara rules for malware that is not being detected by traditional antivirus. Those Yara rules are then shared within the community.
Now, Cyber Triage users can use those Yara rules when investigating endpoints. This gives consultants broader coverage when hunting in an enterprise and allows companies to scan for the latest threats.
The Cyber Triage Integration
Cyber Triage’s agentless collection tool makes copies of many files that may contain malware. This includes startup items, programs the user executed, scheduled tasks, and more. When those files come back to Cyber Triage, they will still be sent to OPSWAT for analysis by many antivirus engines and they will now also be analyzed using Yara rules.
Files that are found to match Yara rules will be marked as “Bad.” They are considered blacklisted items, as you can see in this example:
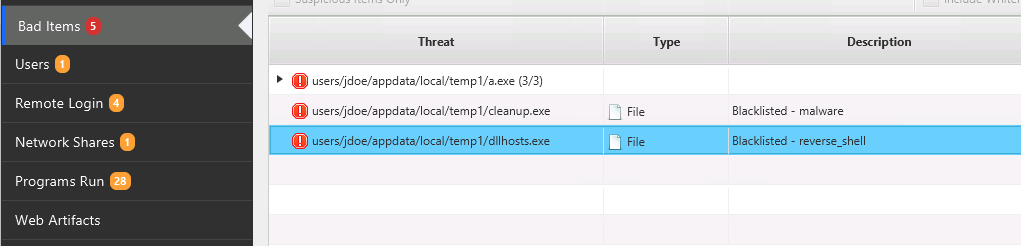
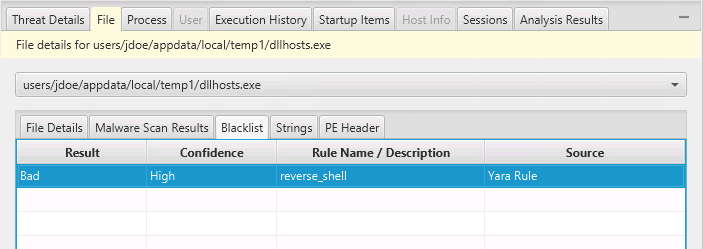
You can see the details of what rule matched the file in the blacklist viewer at the bottom of the screen. In the below example, we can see that this file matched a reverse_shell Yara rule:
Adding Rules
To add Yara rules into Cyber Triage, you need to copy the “.yar” files into a specific folder. You can find that folder is by using the button in the “Options” panel.
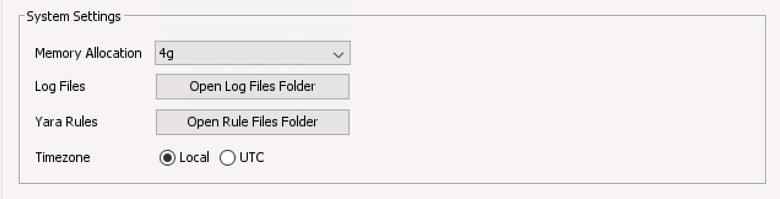
Note: Every time you start a new session and investigate an endpoint, Cyber Triage will compile the rules. Therefore, if you add any rules while a host is being analyzed, they will not take effect until the next session.
More For Advanced Users
The Cyber Triage team is busy adding features that advanced users and consultants need to quickly identify compromised systems. Yara rules give users more control over what is searched for and the Volatility integration allows users to pull in memory images and find hidden processes and files.
To get an evaluation copy 2.2.0, fill out this form. If you’d like a demo or quote, send an email to sales@cybertriage.com.