Our latest Cyber Triage release has a few DFIR features that came directly from customer requests while they hunted around their environments for signs of SolarWinds-based incidents. This post covers those features, namely:
- Collect all DLLs of running processes
- Rescan files after collection for updated IOCs and Yara rules
Both of these features allow you to get a more comprehensive investigation of endpoints and servers.
If you’re interested in trying out these Cyber Triage features or any others (which are also awesome), you can sign up for a free evaluation here.
Collect More Windows DLLs
Nearly every Windows application needs to get functionality from a “dynamic link library” (DLL). The DLLs can be shared amongst applications and allow for easier updates and reduce executable file sizes.
But, they can also be used by attackers:
- DLL Injection is a method whereby attackers get a process to launch a malicious DLL instead of the intended good one
- Some malware exists in a DLL file instead of the original EXE file, such as what happened with SolarWinds.
When the latest version of the Cyber Triage collection tool is run on a live system, it will collect DLLs of running processes in addition to the associated EXE file. All of these files will be sent back to Cyber Triage, stored in the database, and scored to determine if they are malicious.
The DLLs can be sent to the File Reputation Service to get a score based on 40+ malware scanning engines as part of Reversing Labs.
Rescan Collected Files
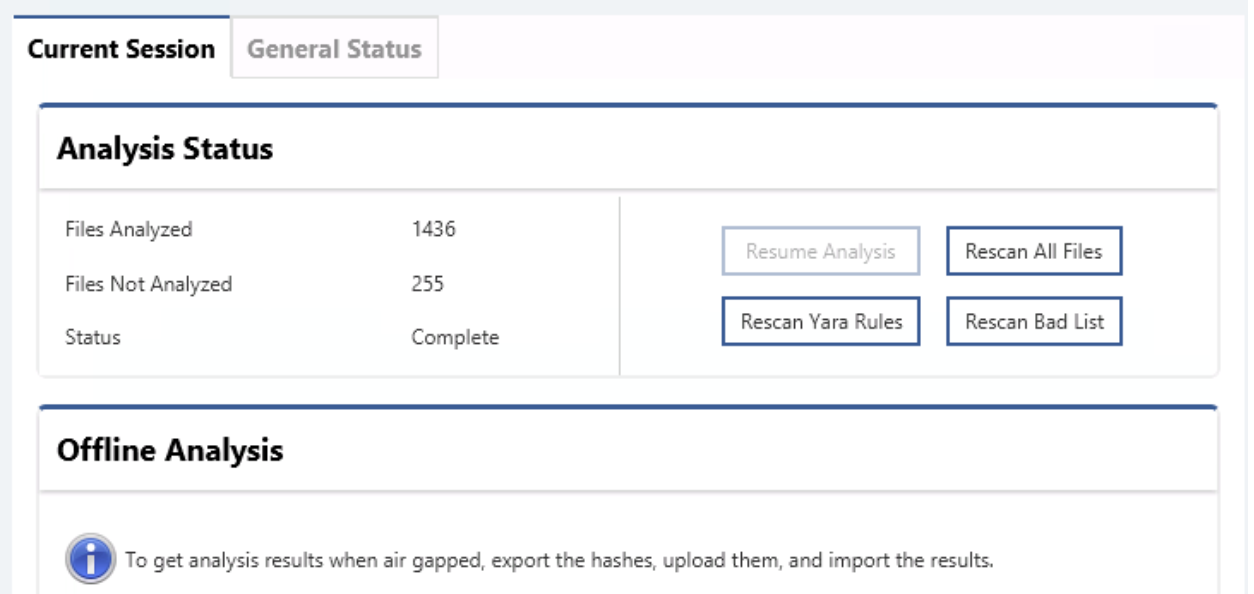
When artifacts come into Cyber Triage, they are stored in the central database and then scored using several techniques. One such technique is to look up items in an IOC list (“bad list”) and scan files with Yara rules.
In the new release, you can now update your threat intelligence (bad list and Yara rules) and rescan the already collected files. This means that when you are on the front lines of an evolving situation, you can update your settings and determine if your systems match one of the rules.
You can do this in the same part of the UI that has always allowed you to rescan files using the malware scanning feature. Now simply choose “Rescan Yara Rules” or “Rescan Bad List.”
Try It Today
Cyber Triage has always been focused on making sure your investigations are as fast and comprehensive as possible. Try out an evaluation version today to see how it can save you valuable time during your examinations and incident response.