What Is It?
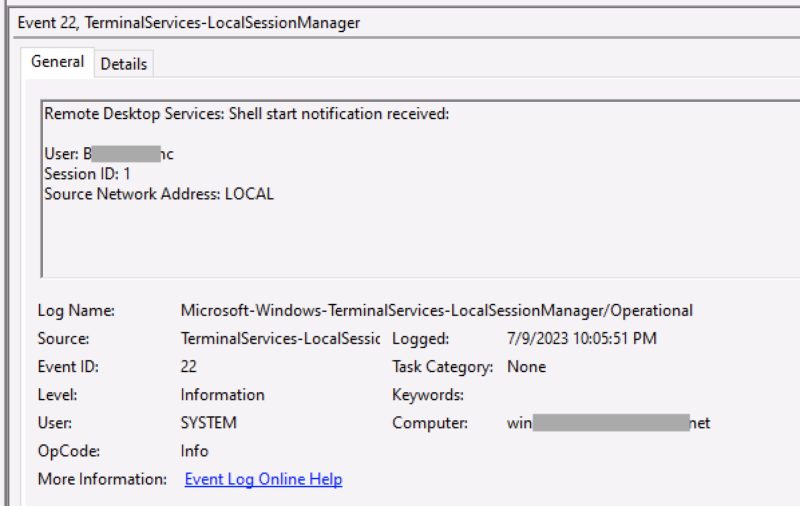
This event is created when a new local session is created for either a local or remote interactive login.
- Event Log: Terminal Services – Local Session Manager
- Event ID: 22
- Event Description: “Shell start notification received”
The Local Session Manager is responsible for creating or finding existing local sessions to support interactive logins. Note that local sessions are different from logon sessions. Local sessions represent the logon sessions, desktop layout, processes, etc. associated with an interactive logon. Learn more about sessions here.
Artifact Family
This event is in the Inbound Logon artifact family. It is related to both incoming Windows RDP connections and local interactive logins.
When Does It Get Created?
Event 22 is created when a new local session needs to be created. That happens after a user successfully authenticates for a local or remote interactive logon session and the user does not already have an existing local session.
For example:
- After a user logs out (not just a disconnect), then the next login for each user will create this event.
- After a system restart, then the first login for each user will create this event.
In our testing, this event follows an Event 21 by a few seconds. Event 21 indicates the local session was created. This event, Event 22, seems to indicate another interim step in the process of creating the local session.
What Data Is Stored?
This event has three fields of interest:
- Timestamp of when the successful login occurred
- User and domain name for account being logged into
- Remote IP address if it is a remote interactive session or “LOCAL” if it’s a local interactive session
Note that this is the same data that you’ll get from Event 21.
Relevance to DFIR?
This entry will show you when a user logged into the system. It has the same information as other events, such as:
- Remote Connection Manager – Event 1149
- Local Session Manager – Event 21
- Security Log – Event 4648
But, these events are all in different event log files and could cycle at different rates. So, you may find this event even if the others have been overwritten or deleted.
Usage in Cyber Triage
Cyber Triage collects and parses the Local Session Manager event log. It uses this event to determine when a logon session started.
Sources
- https://ponderthebits.com/2018/02/windows-rdp-related-event-logs-identification-tracking-and-investigation/
- https://dfironthemountain.wordpress.com/2019/02/15/rdp-event-log-dfir/
- http://blog.kiddaland.net/2015/02/remote-desktop-connections-terminal.html
- https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-r2-and-2008/ee891214(v=ws.10)



