The Cyber Triage Malware Scanner Module for Autopsy allows digital forensic examiners to identify malware and backdoors on a disk image or other data source. This helps determine who had access to the suspect system.
Know Who Had Device Access
The goal of many digital investigations is to tie activity back to a person who can be held responsible. It’s relatively easy to identify who had physical access and computer accounts.
But, identifying covert access is much harder. Defendants may try to assert that the digital evidence was placed there by an attacker, the so-called “Some Other Dude Did It” (SODDI) defense.
The best way to refute that claim is to know if there was covert access backdoor software. Scanning a suspect’s or victim’s system for malware can help you to know what access methods existed.
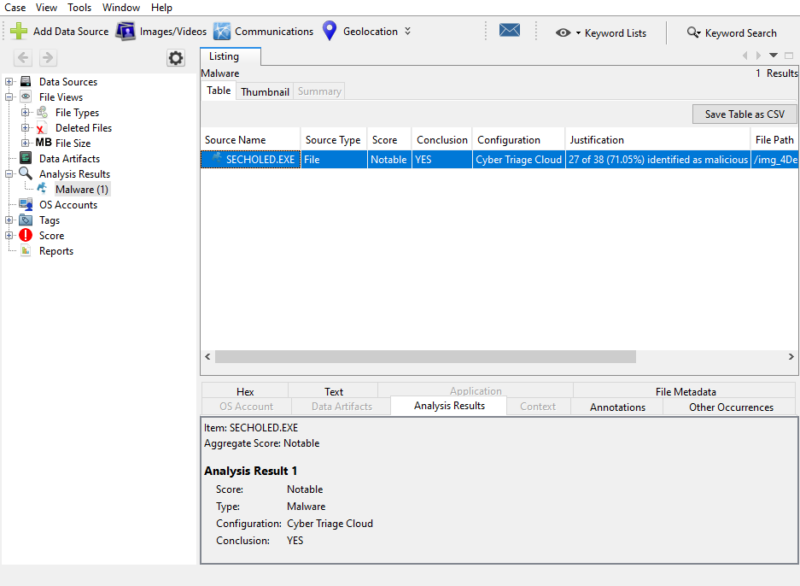
Scan with 40+ Malware Engines
The Cyber Triage Malware Scanning module uses 40+ malware scanning engines to make a decision on if an executable is malicious. This gives you much broader coverage than relying on a single tool, which may incorrectly miss a backdoor.
Don’t Introduce Malware Into Your Lab
Many labs will scan for malware on disk images by mounting the image and using a single, local malware scanner. In addition to the risk of relying only on a single engine, this also introduces the risk that you could launch the malware while it is mounted. This would infect your system and the lab.
The Cyber Triage Malware Scanning module does not write the files to your computer. It uses hash values and uploads files directly to an online analysis service.
How It Works
The Cyber Triage Malware Scanning module is an Autopsy ingest module you can enable when parsing a data source.
Technically, the Malware Scanner Module will:
- Ignore any file that is not a Windows executable (exe or dll)
- Ignore any file that was found in the NIST NSRL (if you enabled that)
- Query an online API with the file’s hash value to see if the file was already analyzed and has results.
- Optionally, upload the full file if the file has not been analyzed before
- Any file that is identified as malware will get scored accordingly.
You can use this module only if you are connected to the Internet. It cannot currently be used in air-gapped environments (though the full Cyber Triage application can).
Privacy
We understand that investigators get nervous about uploading files because they do not want to broadcast to the world that a file has been found. The Cyber Triage Malware Scanning module for Autopsy will:
- Only upload files if you choose to.
- Only upload executable files (no Office or PDF files)
- Only make results available to other Cyber Triage users who also have the hash. The results are not advertised to the public.
Licensing
The Cyber Triage Malware Scanning module is licensed based on the number of computers using it and the number of hosts being analyzed
- You can use a license only on one examiner system.
- The license includes a maximum number of hash lookups that can be performed either daily or weekly.
- The license includes a maximum number of file uploads that can be performed either daily or weekly.
How To Get It
The module ships with Autopsy. To use it:
- Purchase a license using a credit card from here.
- Follow the steps in the user manual
If you want to evaluate the module, you can get a one-time, short-term license by entering your information here.
How It Compares to Cyber Triage
This Autopsy module contains only the malware scanning features from Cyber Triage. It does not include:
- Offline malware scanning capability
- Triage collection tool
- Scoring and parsing of intrusion-related artifacts
- Recommendation engine
- Integrations with other security tools
If you are interested in an end-to-end intrusion investigation tool, then Cyber Triage may be a better fit for your needs.
Autopsy vs Cyber Triage
This is module integrates with Autopsy and uses Cyber Triage servers.
- Autopsy is an open source, general purpose digital forensics tool that can be used for all types of investigations.
- Cyber Triage is more automated and focused on malware, remote access, and user activity. It is faster than Autopsy at finding those types of artifacts.
Buy a Module License
Purchase a 1-year license and pick your lookup limits.
Try the Module for Free
Try it for free, for 7 days, with a limited number of lookups.