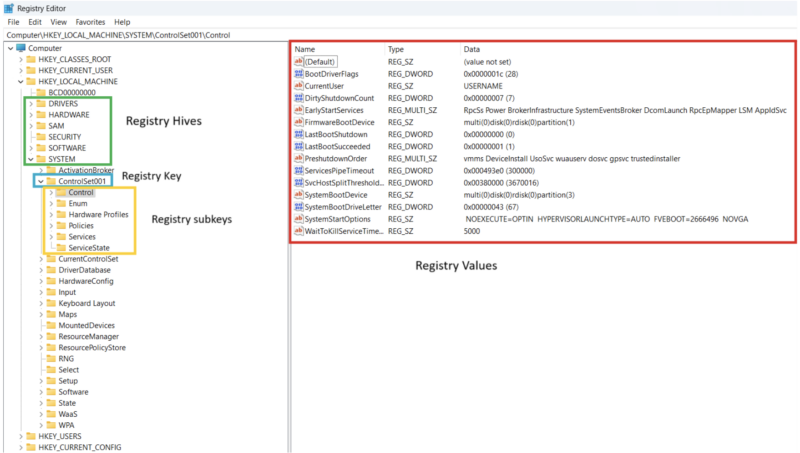
Registry forensics can play a critical role in an investigation because many types of artifacts can be obtained from registry hives.
You can get:
- Evidence of Persistence: Scheduled Tasks and autorun keys.
- Evidence of Execution: RunMRU, MuiCache, AmCache, Bam/Dam, etc.
- Evidence of Data Accessed: Shellbags, Open/SaveMRU, Office MRU, etc.
- OS Config Information: System audit settings, event log settings, etc.
(And more!)
This isn’t a comprehensive overview of the Windows registry. There are entire books about registry forensics, and much to discuss. Instead, we’ll provide an introductory overview of the registry and the registry forensics tools you can use to parse it.
Now let’s get started.
Jump to…
What Is the Windows Registry?
Where Do Registry Files Exist?
How to Access the Registry
Registry Forensics Tools
What to Watch Out for Doing Registry Analysis
The Fastest Registry Analysis Tools
What Is the Windows Registry?
The Windows Registry is made up of multiple registry files that are essentially databases that organize data in a tree structure similar to a file system.
There are several key terms one should understand when discussing the registry.
They are:
| Registry File | REGF formatted binary files used to store registry data.
Ex. C:\windows\system32\Config\SOFTWARE |
| Registry Hives | Logical grouping/view of registry data loaded in memory.
Ex. HKLM\Software |
| Keys | Named “folder” like objects that contain last write timestamps, subkeys, and values. |
| Subkeys | A key that is stored under another key, making a hierarchical structure. |
| Values | Can hold arbitrary data and made up of several components:
|
| Transaction Log | A log file that tracks changes to a registry hive to prevent corruption when adding/updating/removing data. |
| Last write times | A timestamp that records when a registry key was last updated. Updates to a key are represented by values added/modified/deleted to a key or subkeys added/renamed/deleted from a key.
These timestamps are often used in timelines to better understand activity that has occurred in the registry. |
Where Do Registry Files Exist?
This isn’t a comprehensive list of every registry hive on the system, just the most common with forensic value.
| SOFTWARE | |
|---|---|
| Registry Hive Location |
HKLM\SOFTWARE |
| Registry File Location |
C:windowssystem32configSOFTWARE |
| SYSTEM | |
| Registry Hive Location |
HKLM\SYSTEM |
| Registry File Location |
C:windowssystem32configSYSTEM |
| SAM | |
| Registry Hive Location |
HKLM\SAM |
| Registry File Location |
C:windowssystem32configSAM |
| SECURITY | |
| Registry Hive Location |
HKLM\SECURITY
|
| Registry File Location |
C:windowssystem32configSECURITY |
| DEFAULT* | |
| Registry Hive Location |
HKU\.DEFAULT and HKU\S-1-5-18
|
| Registry File Location |
C:windowssystem32configDEFAULT |
| NTUSER.DAT | |
| Registry Hive Location |
HKU\{USER_SID}
|
| Registry File Location |
%userprofile% (default: c:\users\USER_NAME\)
|
| Registry File Location** |
c:WindowsServiceProfiles* |
| USRCLASS.DAT | |
| Registry Hive Location |
HKU\{USER_SID}_Class |
| Registry File Location |
%localappdata%microsoftwindows (default: c:usersUSER_NAMEappdatalocalmicrosoftwindows) |
| AmCache.hve | |
| Registry Hive Location |
N/A |
| Registry File Location |
C:WindowsappcompatProgramsAmcache.hve |
| User.dat | |
| Registry Hive Location |
N/A*** |
| Registry File Location |
C:Users{USER}AppDataLocalPackages{APP_PACKAGE_NAME}SystemAppDataHeliumUser.dat
|
| UserClasses.dat | |
| Registry Hive Location |
N/A**** |
| Registry File Location |
C:Users{USER}AppDataLocalPackages{APP_PACKAGE_NAME}SystemAppDataHeliumUserClasses.dat
|
NOTES
* Represents user profile hive for system account (S-1-5-18). Details are found here.
** Where the NTUSER.dat is stored for system accounts like S-1-5-19 (Local Service), S-1-5-20 (Network Service), and any other virtual service accounts.
*** You will not see these hives loaded when viewing Regedit. These are user and app-specific and get merged with users NTUSER.dat data.
**** You will not see these hives loaded when viewing Regedit. These are user and app-specific and get merged with the users USRCLASS.dat data
The registry files under C:windowssystem32config used to be backed up automatically into C:windowssystem32configregback, but that is now disabled by default in Windows 10.
Interested in learning more about the actual binary structure of registry files and how data is stored?
Check out these references:
- Maxim Suhanov: Windows registry file format specification
- Joachim Metz: Windows NT Registry File (REGF) format specification
- Timothy D. Morgan: The Windows NT∗Registry File Format Version 0.4
Another great resource for learning more about the registry and its format is registry parsing libraries.
We will discuss these in our next section.
How to Access the Registry
Accessing registry data will depend on what type of analysis you are performing.
If you are doing a live triage, you can use System APIs or other tools to access the in-memory (loaded version) of registry hives. However, if you are processing a memory dump, a disk image, or offline registry files you’ll need different tools.
Our main focus will be on analyzing and parsing offline registry files, but we will briefly talk about the other two.
Memory Dump Analysis
Two common tools to process registry data from memory are:
Live System Analysis
Accessing registry hives currently loaded by the system can be done many ways, including:
- Using PowerShell cmdlets.
- Directly through Windows APIs.
- Using command line tools like reg.
- Using a forensic tool that can parse registry files.
- Using Regedit.exe or the more feature-rich Total Registry.
Offline Registry File Analysis
To access the data inside a registry file, you first need to parse the data. There are many registry parsers and libraries available in various programming languages.
Common ones we’ve seen:
| Name | Status | Notes |
|---|---|---|
| python-registry | Actively maintained. |
|
| regipy | Actively maintained. |
|
| yarp | Unknown. |
|
| Rejistry | Not actively maintained. |
|
| TSK Rejistry++ | Actively maintained. |
|
| notatin | Actively maintained. |
|
| regparser | Actively maintained. |
|
| libregf | Actively maintained. | |
| RegFI | Unknown. |
|
| Parse::Win32Registry | Unknown. |
|
| registry | Actively maintained. |
|
Many of the registry parsing tools (both command line and GUI-based) are built off of these registry parsing libraries. You aren’t normally going to use one of these libraries directly unless you plan on building your own scripts/app to do registry processing.
Registry Forensics Tools
Here are some common registry forensics tools that are actually used to view the registry or pull important registry data automatically:
| Registry Explorer | RegRipper4 | Registry Recon |
|---|---|---|
| Easy-to-use GUI to explore registry hives. | Command-line and GUI-driven tool to parse out registry data of interest (is not a registry viewer). | Easy-to-use GUI to explore registry hives. |
| Built-in plugins to parse out interesting registry data for easier viewing. | Built-in plugins to parse out interesting registry data. | Powerful and unique feature to rebuild registry view over time. |
| Bookmarks for key registry artifacts for easy review. | Does not handle transaction logs. | Handles transaction logs. |
| Handles transaction logs. |
What to Watch Out for Doing Registry Analysis
If analyzing offline files:
- Ensure your tool handles transaction logs.
- If it does not you can first rebuild the registry using a tool like RLA.
If doing live analysis:
- Ensure your tool can handle registry redirection if it’s a 32-bit application.
- Check to see if your tool will parse artifacts from new MSIX registry files. Learn more about this here.
When doing both:
- Be careful when inferring an artifact was added/updated based solely on a registry key’s last write timestamp. They can be updated for many reasons and can also be timestamped. Read more about this here.
- Understand your tool’s limitations. For example, if a registry key or value name has a NULL character in it, it will prevent that key and subkeys from being displayed in the regedit UI. You can read more about this here.