As we talk to corporate security teams about how they respond to incidents and EDR alerts, we find it useful to highlight the Endpoint Triage step in their response process. Endpoint Triage allows you to make decisions about what to do with an endpoint.
Do you wipe it or escalate it?
We’re going to do a series of posts on this topic. This is the first where we cover the topics of what endpoint triage is and when to do it.
What is Endpoint Triage?
Endpoint Triage is a short digital investigation that allows you to make prioritization decisions about what to do with the device:
- High-priority devices get immediate attention.
- Lower-priority devices can wait.
Triage is used in many types of digital investigations and the underlying goal is the same as medical triage: prioritization. Medical triage is focused on prioritizing patients. It’s not about a specific diagnosis. It’s about identifying who needs immediate medical attention.
For intrusions, the core goal is often to identify the impact of a computer compromise. A company will make different decisions based on if there was lateral movement and the type of malware found.
Endpoint Triage focuses on:
- Was there malware?
- Was data exfiltrated?
- Was there lateral movement?
What is Alert Triage?
While they have similar names and are both performed by the security team, alert and endpoint triage have different goals. Alert triage identifies the priority of an EDR or other security alert.
Alert triage focuses on:
- Is the alert real or a false positive?
- What is the potential impact of the alert?
- How critical are the hosts associated with the alert?
Based on questions like the above, the alert could transition to an Endpoint Triage phase for the hosts involved with the alert.

Example SOC Alert Review Process
Let’s consider some example scenarios.
EDR Malware Alert
A company’s EDR generates an alert for malware on a laptop:
| Alert Triage | Endpoint Triage | Incident Declared |
|---|---|---|
| The SOC analyst (or MSSP) reviews the alert. They determine it’s not a false positive, and the malware has the potential for remote access. | The laptop is triaged, and it is determined that the attacker exfiltrated data. | Based on the endpoint triage findings, an incident is declared, and the incident response plan is started. |
SIEM Alert for Failed Logins
A company’s SIEM generates an alert for repeated failed logins to a server:
| Alert Triage | Endpoint Triage |
|---|---|
| The SOC analyst reviews the alert and identifies that there were attempts for accounts that do not exist (possible spray attack) and attempts for the admin account. Admin account was successfully used for a login later that day. | The server is triaged to look for anomalous activity and nothing was found. The internal employee who performed the login was identified and confirmed it was not an attacker. |
Endpoint Triage with Cyber Triage
One way to effectively perform endpoint triage in your SOC is with Cyber Triage. Cyber Triage will collect and analyze the data needed to assess the priority of a host.
Typical process:
- Alert Triage: The analyst reviews the alert and decides to escalate
- Deploy Collector via EDR: The analyst deploys the Cyber Triage Collector program via the EDR agent.
- Automated Analysis: Cyber Triage analyses and scores artifacts.
- SOC Analyst Review: The analyst logs into Cyber Triage to review the artifacts scored as bad and suspicious. These will help them identify if data was exfiltrated, lateral movement occurred, and what types of malware were found.
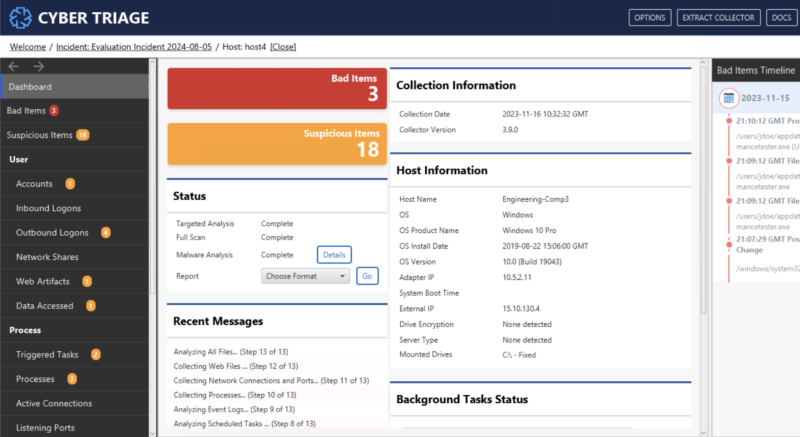
- Make a Plan: Based on the results, the company can decide to escalate or wipe the system.
Endpoint Triage Reduces Your Risk
Endpoint triage is a critical step in any corporate security team’s procedures. Even if you outsource your SOC to an MSSP, you will have situations where you are given an alert to handle. You need to be able to triage the host associated with the alert to determine the scope.
If you need an endpoint triage solution, try the 7-day evaluation of Cyber Triage.
You can also contact us if you have any questions or thoughts.
