Our “Free DFIR with Cyber Triage Lite” series paused for a bit because of conference presentations and releases, but we’re back and continuing on the theme of reviewing the collected incident response data.
As you may recall, we covered how to collect data in the previous posts and then had one post on reviewing user-related data. In this post, we are going to talk about reviewing malware-related data.
You’ll want to read this article if you are looking for a free DFIR tool that gives you a UI to review your collected data and generate reports.
Divide and Conquer DFIR Process
Before we dive into the details of the Cyber Triage Lite UI, let’s review the Divide and Conquer DFIR process, which is how we approach digital investigations. You can skip this section if you’ve already heard us talk about this.
The basic concept is that you’ll start with an investigative question (such as “what did the attacker access”?) that is often hard to answer. The solution is to break it into smaller and smaller questions that can be answered with a single type of artifact. It uses the basic problem-solving technique of breaking a hard problem into smaller and easier problems.
As several of our previous posts and videos have outlined, we often break the questions down into groups about:
- Users: Was there suspicious user activity?
- Malware: Was there malicious programs?
- OS Configuration Settings: Was there malicious system changes?
Each of those is further broken down (we’ll break down users in the next section).
That’s the gist at the high-level. To learn more, refer to:
- Blog Series
- Online Video Course (3-hours)
What is Cyber Triage Lite?
Since it’s been a few weeks since our last post, let’s also review what Cyber Triage Lite is. Cyber Triage Lite is the free version of Cyber Triage. It uses the same Collection Tool, but it doesn’t have the analytics and scoring features of Cyber Triage Standard. For example, you’ll get the same UI as Cyber Triage, but it won’t have items marked as Bad or Suspicious.
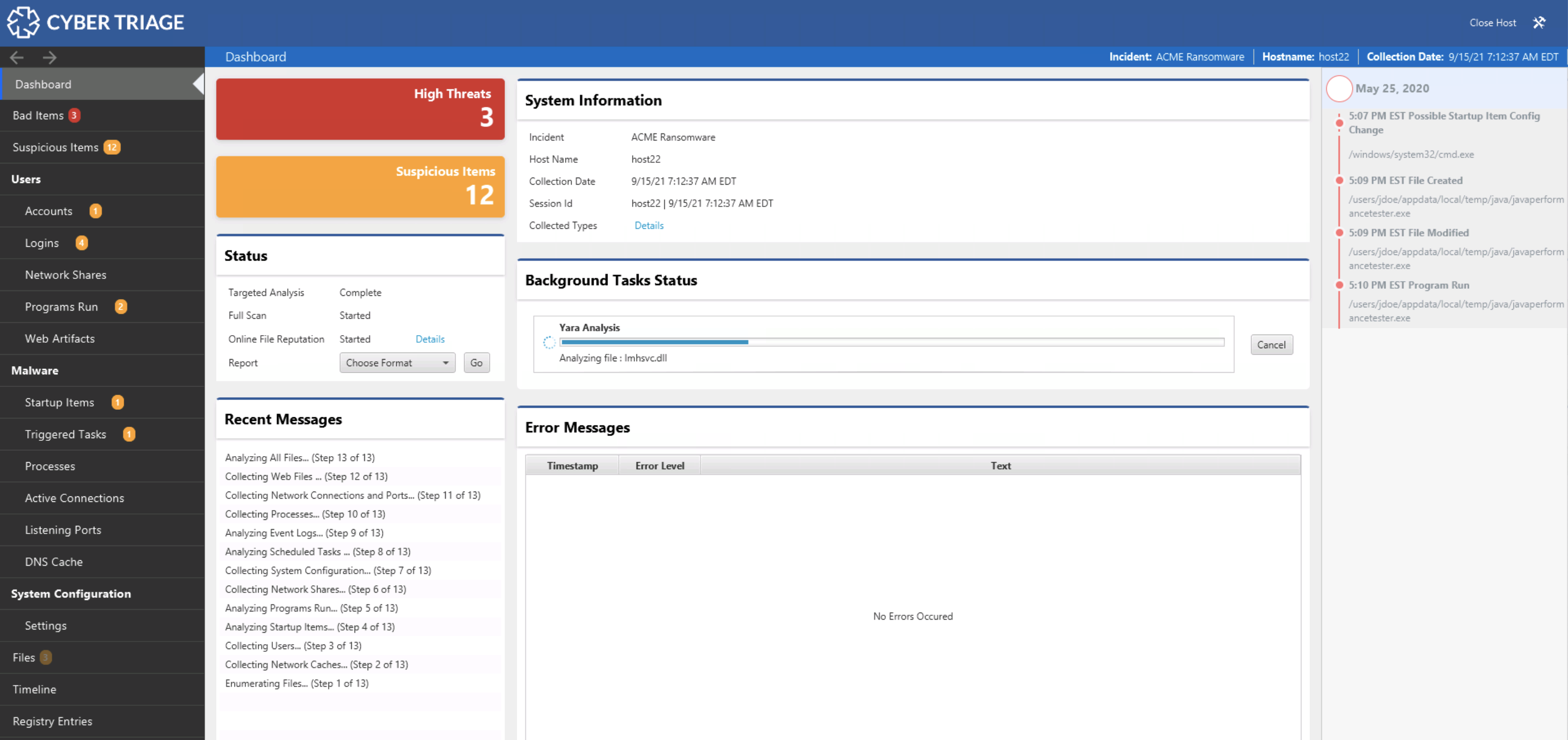
The main advantage of Cyber Triage Lite over other free DFIR tools is the UI. There are other free collection tools, but they give you a list of text files to review. Cyber Triage Lite gives you a UI to navigate and pivot with. That’s what this series is about.
Why We Look For Malware
Your DFIR investigation will likely look for malware because it’s a part of nearly every attack at some point in the process. Not every compromised computer will have it, which is why previously looked for compromised accounts, but it needs to be part of your review of any system.
Cyber Triage Lite allows you to look for malware and its UI is organized around the Divide and Conquer concepts.
The UI breaks the question of “Was there malicious programs?” into smaller questions that can be more easily answered. Notably:
- Are there malicious persistence mechanisms?
- Are there malicious processes running?
- Are there suspicious ports listening
- Are there suspicious network connections?
Are There Malicious Persistence Mechanisms?
Malware needs to be launched for it to run and do its malicious things. So, malware often has some way of starting itself even when a computer has been powered off.
There are two tabs in Cyber Triage that focus on the common persistence mechanisms:
- Startup Items: Programs or services run when the computer is powered on or a user logs in.
- Triggered Tasks: Scheduled tasks and WMI actions.
NOTE: Later this year, we will merge Startup Items into Triggered Tasks because their trigger is simply a user login or system power on. But, right now they are separate for historical reasons.
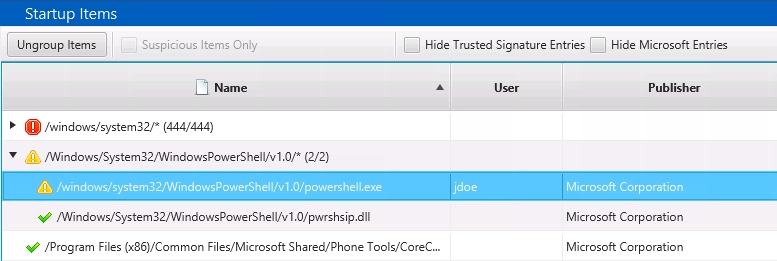
The Startup Items area shows files associated with the dozens of registry keys and Startup Folder items that are often called AutoRun items based on the popular SysInternals tool. This is where you’ll find entries from the Run, RunOnce, etc. keys.
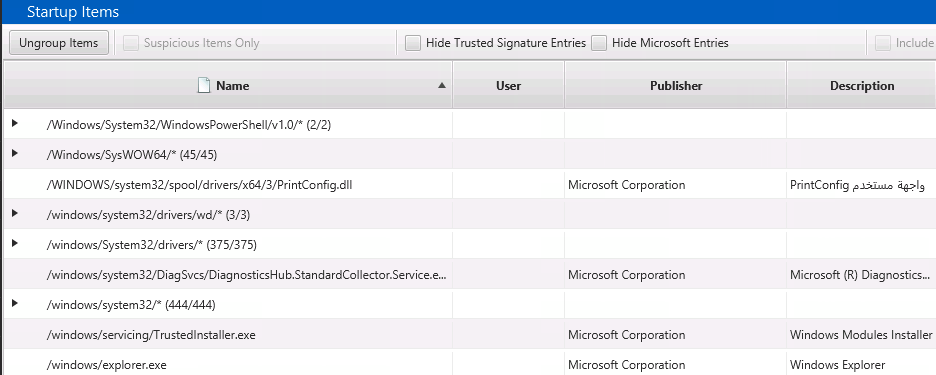
The Startup Items are grouped by parent folder to make it easier to identify the anomalous folders. In the above image, 444 items from ‘\windows\system32’ are grouped together. Of course, malware can place itself inside system32, so you can’t entirely ignore this folder. But, it shouldn’t be the first place you look.
Because there can be a lot of startup items, there are filters on the top to ignore Microsoft- and trusted-signed executables. Again, there have certainly been examples of malware that were signed, but it’s always good to start with a small set of data to look for less advanced threats.
Like the other views we saw in the previous blog post, the bottom part of Cyber Triage Lite is where it excels over looking at the outputs of command line tools. You can select an item and use the bottom to see details, including which of the many registry keys it could have came from:
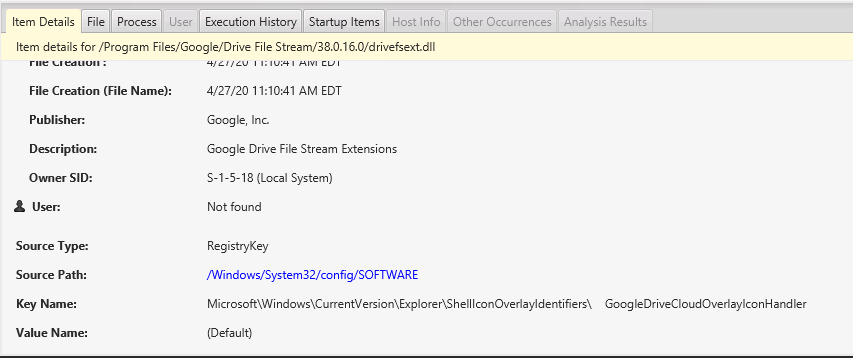
The Process Tab will show you if the startup item is still running. And, if so, if it has network ports open, active connections, etc.
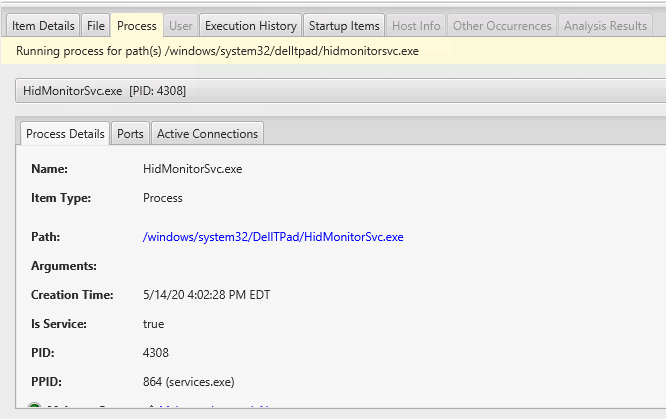
The Execution History tab will show you if there was any evidence of the process, such as from Prefetch or AppCompatCache. The UI allows you to pivot between various data types.
The TriggeredTask view is similar, It also groups by parent folder and has some slightly different filters. You can choose to include WMI Actions and to hide disabled Scheduled Tasks.
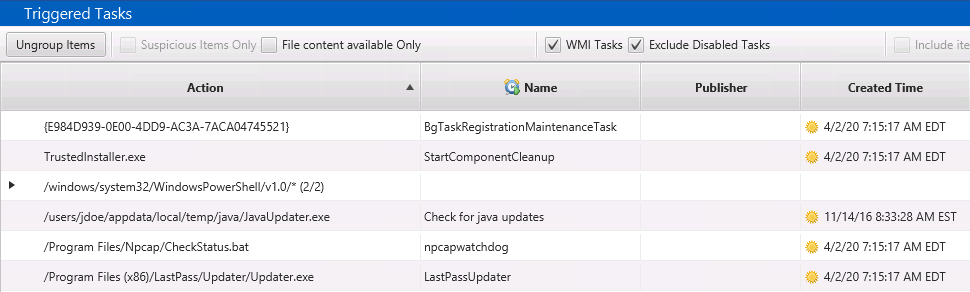
The bottom views are the same as for selecting a Startup Item.
For more info, refer to the Intro to IR: Malware Persistence for more details on what kinds of items you’ll want to identify.
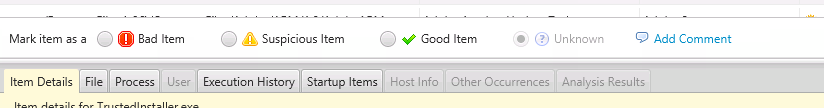
As with every other item in Cyber Triage, when you find a suspicious item, you can manually score it.
The paid version of Cyber Triage will scan the executables and DLLs associated with the triggered tasks and startup items with 40+ malware engines and apply other heuristics, such as anomalous path detection or suspicious PowerShell commands.
Are There Malicious Processes Running?
The Process tab will give you a tree of the processes that were running at the time of collection. The tree is organized by parent process and you can see arguments that were used, start times, and the user it was running as.
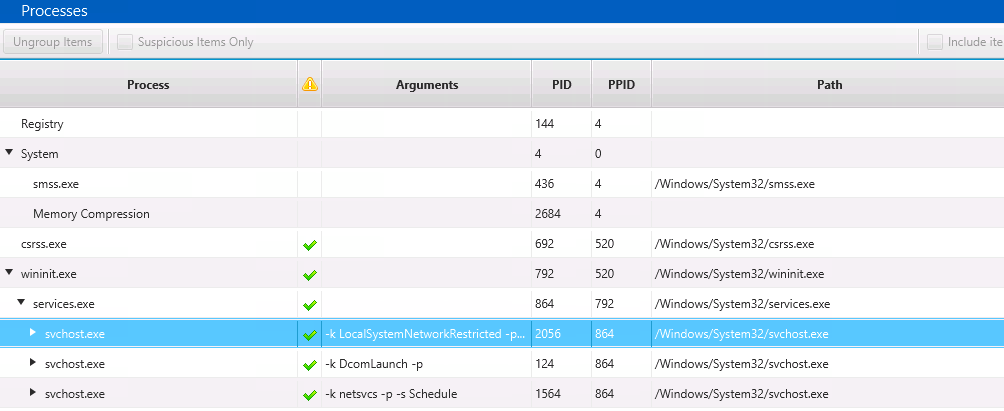
This view is similar to what you’d get out of other text-based tools that show running processes, but the UI allows you to dive into the details. For example, you can look at the open network that a process has.
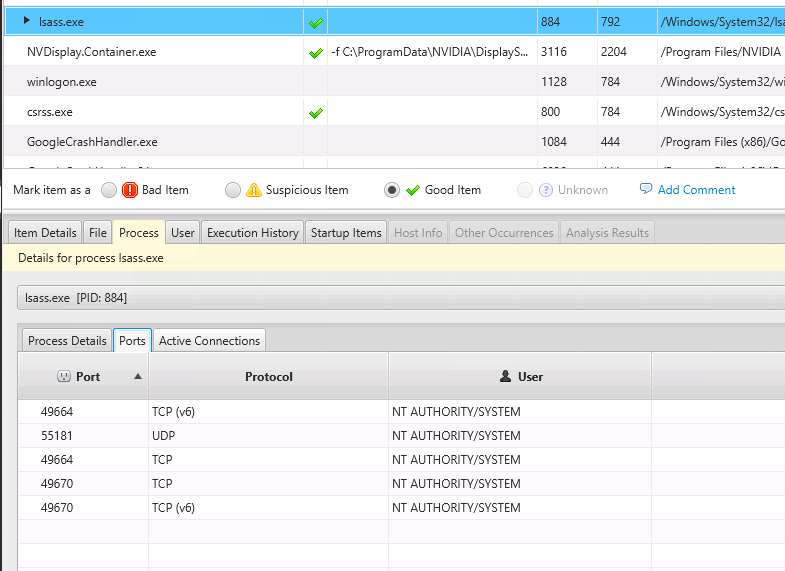
The paid version of Cyber Triage will mark processes as bad or suspicious based on malware scan results, the path of the process, and other heuristics that are often associated with malware.
The Intro to IR: Detecting Running Malware post went into much more detail about what to look for and various ways that malware hides itself.
Are There Suspicious Network Connections?
The Active Connections tab shows TCP connections that existed at the time of collection. They are organized by the process that had them open. This makes it easier to focus on anomalous processes. In the below screenshot, FireFox had 56 connections that we can initially ignore.
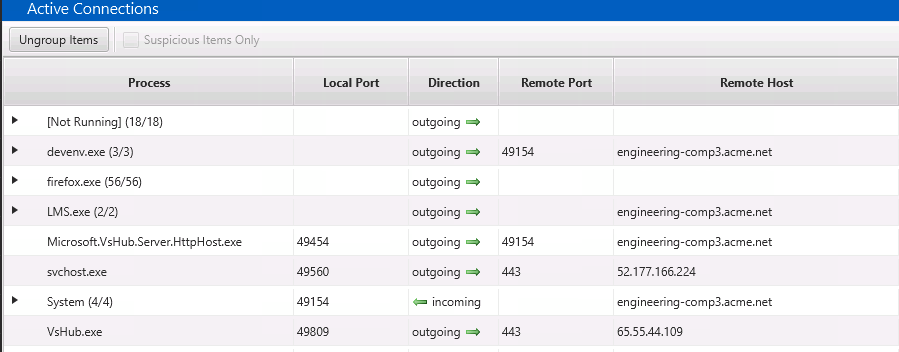
You should review this data to look for unexpected processes with network connections or any unexpected remote destinations.
You can use the bottom to get more information about the external host:
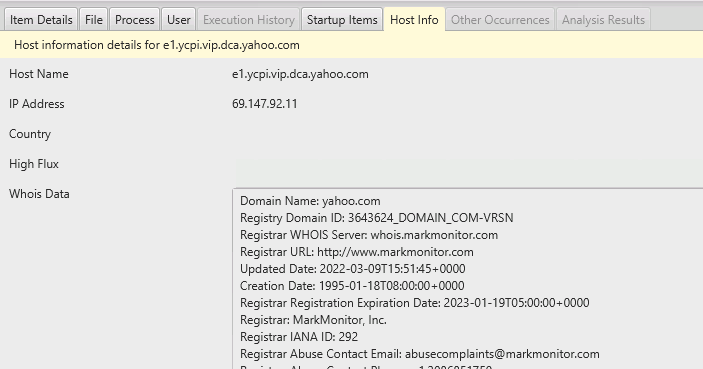
The paid version of Cyber Triage will flag connections based on port numbers and host names.
Are There Suspicious Ports Listening?
You can also review for unexpected TCP and UDP ports that are listening by choosing the “Listening Ports” tab. This too is grouped by process to make it easier to focus on anomalous processes.
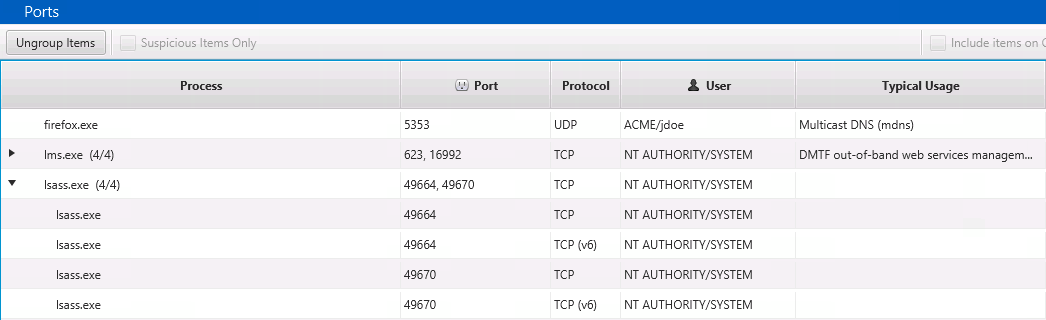
Once you’ve identified a port you want to investigate further, the bottom area allows you to dive into the details, active connections, and execution history of the process that opened it. Below is an example of other active connections associated with the Firefox process that had a listening port.
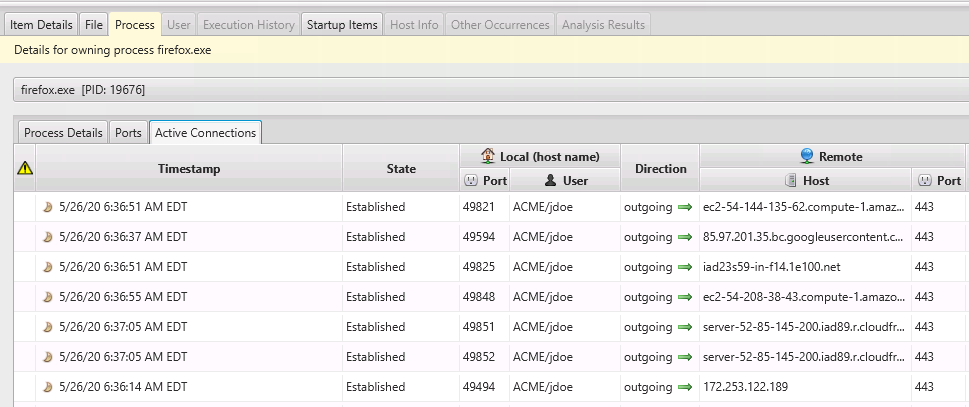
The paid version of Cyber Triage will flag ports as suspicious if they open by unexpected processes or are not typically open on an endpoint (or server).
Conclusion
Malware is a big part of any investigation and Cyber Triage Lite has features dedicated to the review of malware-related artifacts.
