RunMRU shouldn’t be a mystery. Nor should how to investigate it.
Read this blog post to learn what RunMRU is, how it works, and anything else investigators should know about this Windows artifact.
Jump to…
What Is RunMRU Registry Key?
How RunMRU Works
Forensic Importance of RunMRU
When RunMRU Misses Data
How to Investigate RunMRU with Cyber Triage
Keep Learning About DFIR Artifacts
What Is RunMRU Registry Key?
RunMRU (Most Recently Used) is a Windows registry key that stores a list of the last 26 commands entered in the Run dialog (Win + R) on a per-user basis. The command’s execution order can be obtained from the “MRUList” value in the key. It keeps an ordered list (left being most recent) of recently used commands (hence the name MRU).

The RunMRU key is located in a user’s NTUSER.DAT registry file under each user’s profile directory: c:\users\[user_name]
Dead Analysis
Registry File: C:\users\[user_name]\NTUSER.DAT Key: Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
Live Analysis
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
How RunMRU Works
RunMRU is one of the simplest and most straightforward forensic artifacts you will encounter.
| How It Works at A High Level | |
|---|---|
| Stores commands entered in the run dialog | RunMRU key is updated each time a command is run from the run dialog box.* |
| Assigns commands to lettered entries |
|
| Maintains execution order in MRUList |
|
NOTE
* If an invalid action is entered in the dialog box, such as a file that does not exist, it will not be recorded.
| Here’s A Detailed Analysis | |
|---|---|
| How Users Can Bring Up the Run Dialog Box The Run dialog box is implemented in an exported function in shell32.dll and can be invoked in numerous ways, all of which call the underlying function from shell32.dll. |
|
| #1 | Win + R |
| #2 | Windows Start Menu Search → Run |
| #3 | Task Manager → Run new Task |
| #4 | Shell:::{2559a1f3-21d7-11d4-bdaf-00c04f60b9f0}* |
| #5 | rundll32.exe shell32.dll,#61** |
| #6 | Programmatically bring up Run dialog via Shell.FileRun() or IShellDispatch.FileRun(). |
Any of the above methods will result in a Run dialog box being brought up, all of which rely on the same RunMRU key for prepopulating the list of previous commands (as long as the same user is being used).
NOTES
* This can be run directly from the Run dialog box or Explorer search bar as is. To run from command prompt, you’ll need to prepend ‘explorer.exe’.
** Runs the method directly from shell32.dll via its ordinal value of 61.
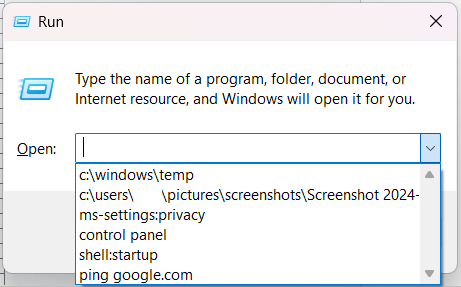
What Happens When Run Box Is Opened
When a Run box is opened, it queries for the MRUList value for the user that the process is running as. Once the MRUList has been obtained, each value is queried to build the command history in the proper order, as seen below.
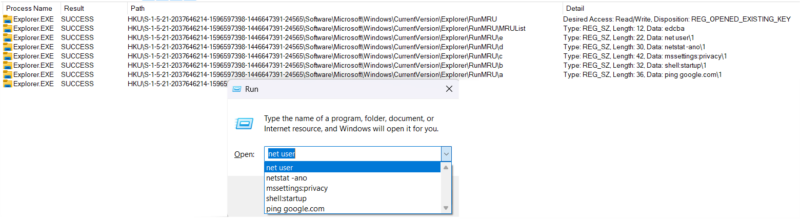
What Happens When Run Box Executes A Command
When a command is run from the Run box, the new command is written to the key, and the new MRUList is written to the key as well.
NOTE
The Run box is querying all of the values again, but they do not appear to be used for anything. Tests show if the value is missing or different than what the Run box had in its history, it will still not be updated. The only data ever added to the key is the latest command run.
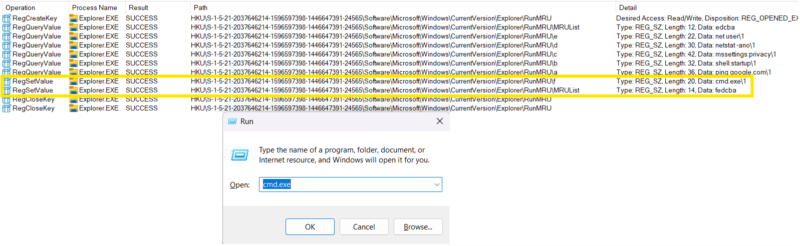
What Is the Max Number of Items Stored in RunMRU
The maximum number of entries that can be stored in a single user’s RunMRU key is 26 entries, named a-z. Once command 27 comes in, it will overwrite the least recently used command, as seen below. If a command is already in the list, it will not write a new entry but instead update its place in the MRUList.



Forensic Importance of RunMRU
The key pieces of information that can be used from RunMRU are:
- User that executed command.
- Full command executed as typed by user.
- General order of execution for commands.
Having said this, RunMRU doesn’t hold a significant amount of forensic value for the following reasons:
- Limited history: Last 26 commands per user.
- Limited scope: Only applies to commands executed from run dialog box.
- Lack of timestamps: Order of execution can be determined, but only the time of the most recently executed command can be determined based on the registry’s last write time.
Some scenarios where RunMRU could be more forensically relevant would be insider threat investigations where the user has used the RunMRU box. For example, a disgruntled admin using the Run box more than a standard user. Other scenarios involve malicious actors tricking users into executing stuff from the Run dialog box.
| Examples Include | |
|---|---|
| Tech support scammers tricking victims into running commands, such as to open up a website to download RMM tools. | Read more here. |
| Malware using fake captchas to trick users into pasting malicious commands into the Run box. | Read more here, here, here, and here. |
When RunMRU Misses Data
While it’s important to understand what data is contained in the RunMRU artifact, it’s equally important to understand when data will not show up in the RunMRU artifact.
Several scenarios result in data not showing up in the RunMRU key:
- RunMRU History Is Disabled.
- When Process Activity Happens Outside of the Run Box.
- RunMRU History Has Been Cleared.
Let’s look at each of these.
RunMRU History Is Disabled
The RunMRU history can be disabled 2 ways, both are applied on a user-by-user basis:
Method 1: Disable tracking app launch in Windows privacy settings.
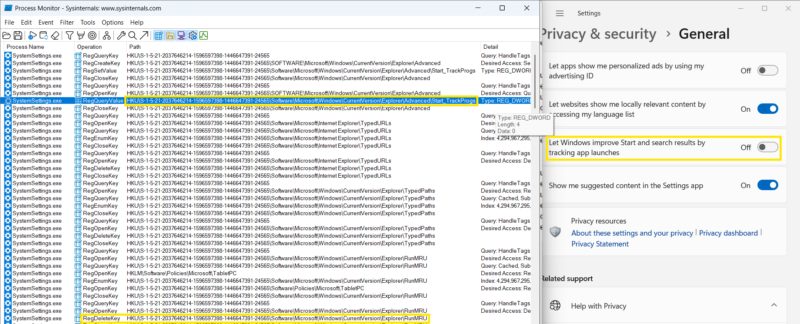
By turning off the “Let Windows improve Start and search results by tracking app launches” privacy setting, you disable the use of the run box history as seen in the above screenshot. Once the switch is made, the “Start_TrackProgs” value is set to 0 (indicating that the setting has been disabled). This also deletes the RunMRU key to clear any preexisting command history.
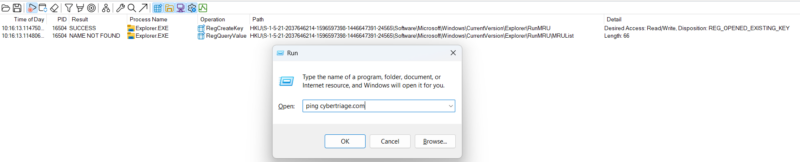
The above image shows there is no history being obtained by the run box, as seen in the sysmon output. To further confirm this, the “ping cybertriage.com” command is run.
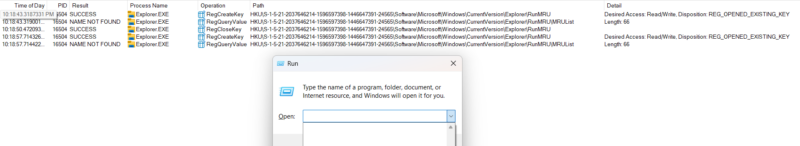
After executing “ping cybertriage.com,” we see that Explorer did not attempt to add the new command to the RunMRU key like we saw before. This is because of the privacy setting change made earlier.
Method 2: Update the RunMRU registry key with a Deny All ACL.
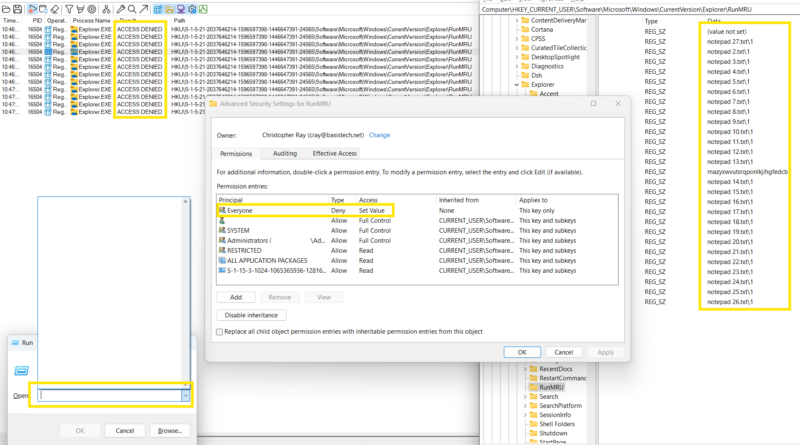
Here, we see that adding a deny-all ACL to the registry key can have the same effect as the privacy setting. The main difference behind the scenes: Explorer is still trying to read/update the RunMRU key, but it’s failing to do so because of access denied errors.
When Process Activity Happens Outside of the Run Box
This is a major reason why RunMRU does not have a lot of forensic utility. It does not record anything not explicitly typed into the Run box, making it very easy to avoid.
RunMRU History Has Been Cleared
Attackers can manually clear RunMRU history by deleting the RunMRU key or specific values. This will need to be done for every user the attacker has run commands with from the run box.
How to Investigate RunMRU with Cyber Triage
RunMRU is what we call a data artifact. The information extracted from data artifacts, like RunMRU, we refer to as information artifacts. Data artifacts like RunMRU are “process run” information artifacts.
The reason we suggest that investigators think about artifacts in this way is because it helps them focus on the right things. There are many different data artifacts similar in terms of their computing function, but have slight differences in the details. If investigators think top-down, they start to piece together what happened more easily. If they think bottom up, they can easily get lost in the weeds.
Read more about our philosophy and these terms in our information artifact blog.
This is why the Cyber Triage UI displays information artifacts regardless of what data artifact (RunMRU, MUICache, Prefetch, etc.) it came from. In the case of RunMRU, we are looking at processes, so Cyber Triage groups all the relevant data artifacts together. So, instead of reviewing single data artifacts like RunMRU — especially when it lacks critical details like execution time — you see everything in a single view. This provides context that RunMRU alone can’t.
This allows you to quickly answer the question:
“What did a user execute?”
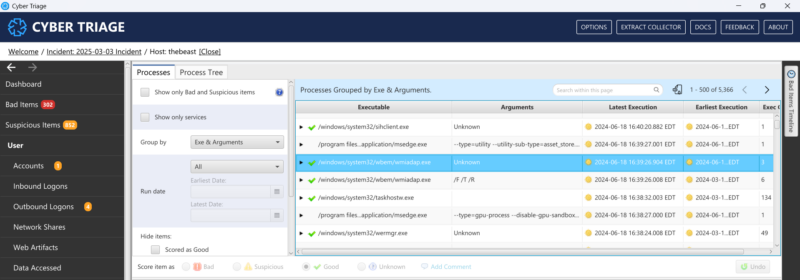
The screenshot below shows the Cyber Triage process table.
It is grouped by:
- Exe
- Arguments
The group can be updated to also include users if that is what we care about.
The groups will show:
- Earliest execution time
- Last execution time
- A count of instances for each group
You can jump into each group and select individual process execution instances to get more details. Below is a process from RunMRU. The execution time is unknown. You can view the original data we normalized from the data artifact along with the associated user:
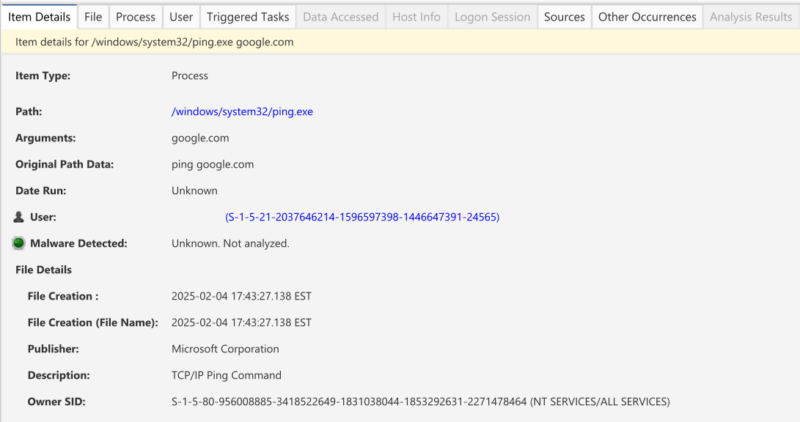
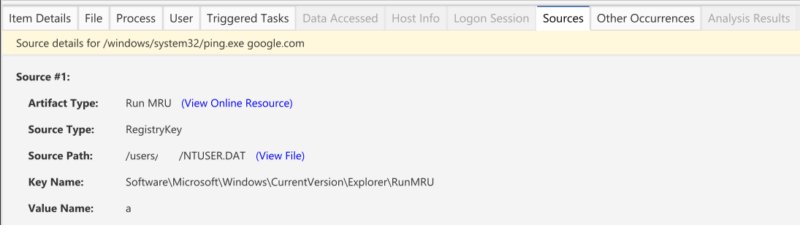
Curious about where an information artifact came from? Jump to the sources tab for those details. Other tabs can provide context about the item you are looking at.
For instance, we are looking at a process and can jump to the “Triggered Tasks” view to see if there is any persistence for it or the “File” view to get details about the file on disk (if it exists):
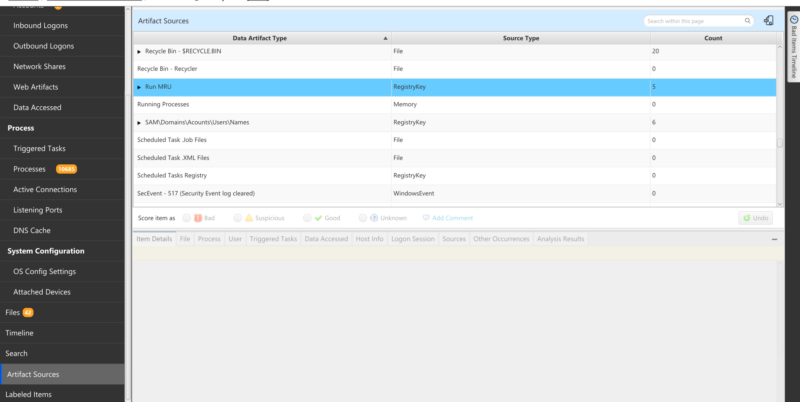
Want to focus on a specific data artifact? Jump to the artifact sources table to view all the data artifacts Cyber Triage processes:
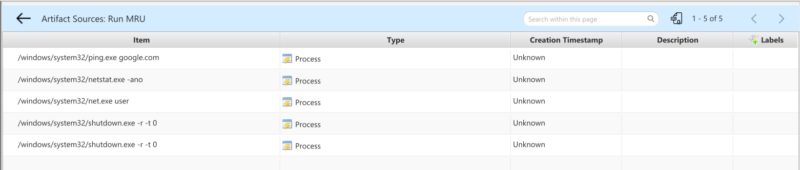
Opening up the RunMRU group lets you see all process execution artifacts pulled from RunMRU:
If you’d like to try investigating RunMRU with Cyber Triage now, try 7 days for free.
Keep Learning About DFIR Artifacts
If you found this RunMRU article useful, check out our other artifact analysis posts:
- Jump Lists Forensics 2025
- How to Investigate Malware WMI Event Consumers 2025
- WMI Malware: The Complete Forensics Guide
- MUICache: 2025 Guide for IT and Investigators
- DFIR Breakdown: Impacket Remote Execution Activity – Smbexec
- DFIR Breakdown: Impacket Remote Execution Activity – atexec
- DFIR Next Steps: What To Do After You Find a Suspicious Use of curl.exe
- DFIR Next Steps: What To Do After You Find a Suspicious Use of certutil.exe
