It’s important to quickly start collecting DFIR artifacts when an incident is detected. In this post, we will look at how to do that using Windows Defender, with a deep dive into the Live Response capability. This post is useful if you are a Defender user or are thinking about becoming one. EDRs do not have all of the data you need for an investigation.
Cyber Triage’s adaptive collection tool ensures you get all of the artifacts you need for an investigation.
Why You Need More Data than Windows Defender for Endpoint
When many companies first get an Endpoint Detection and Response (EDR) system, such as Defender for Endpoint, they think their incident response needs are 100% met since the word “Response” is in the name. However, they soon realize this is not the case.
EDR is great for basic alert validation, isolating the system, and basic remediation, but it’s not the only investigation tool you need during an incident.
Some specific reasons you need more than just an EDR:
- Attackers know how to avoid EDRs; therefore, you should assume the EDR could be missing something.
- EDRs only have the data they use for detection, and your investigation may need to go beyond that.
- EDRs have limited data retention policies, and the incident may have started before your EDR telemetry data rolls over.
- EDRs want low false positives, and this leads to missing important artifacts that could be relevant to your investigation.
And, if you don’t believe us that you need to go beyond what an EDR has, you need only refer to the EDR documentation. They all allow you to integrate additional DFIR collectors. They know they don’t have everything.
Windows Defender Response Methods
Defender has three general methods for advancing an endpoint investigation. Your access to them though depends on what subscription you have. They include:
- Collection Investigation Package: Additional data is brought back using the existing Defender agent. It’s data that is similar to SysInternals tools, such as autoruns and network connections. This comes back as a ZIP file containing text files you can manually parse.
- Automated Investigation: This process is less about additional data collection and more about scoping and remediation. It can remove files from endpoints and search other systems to see if they also have it. It does not do root cause analysis. This works on limited versions of Windows.
- Live Response: This gives you a command prompt on the remote system with the ability to run scripts and pull files back.
You can customize what happens with Live Response, and that’s how our customers deploy the Cyber Triage Collector. The Collector’s recursive collection capabilities allow it to collect more artifacts than the built-in EDR features and more than other DFIR collectors.
Collecting Artifacts with Live Response
Of the 3 options, Live Response has the most flexibility (and therefore complexity). Let’s dive into this capability a bit.
First, you need to configure the system for this to work. Instructions are provided by Microsoft.
There are some key concepts to keep in mind as you think about using it to collect additional data:
- Defender has a central “library” where you can store files (scripts, executables, configuration files, etc.) that will be pushed to the endpoint when a Live Response is started.
- You can use the command prompt to push and pull files from the endpoint, but each file must be less than 3GB.
- The files are saved to a “Download” folder in “C:\ProgramData”, but any program you launch will not have write permissions to that folder. You need to save it elsewhere.
- Defender will kill the session after no user activity for 30 minutes (even if a script is still running).
- In our testing, pressing a key every now and then doesn’t extend the time limit.
So, if you want to use additional tools to collect DFIR artifacts, the basic process would be:
- Add the files into the library
- Start a Live Response session and manually launch the commands
- If they produce output files, versus sending the data over the network, then you need to manually copy the files back.
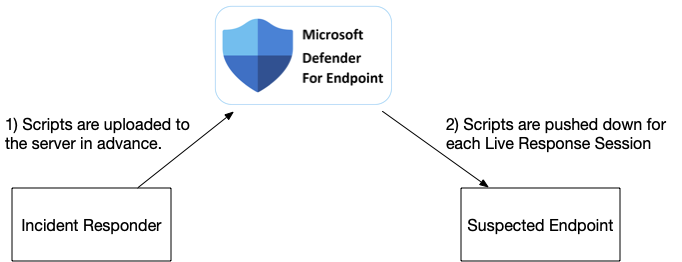
Deploying Cyber Triage Collector with Defender Live Response
The Cyber Triage Collector is a great way to get more information for your investigation. It’s a comprehensive collection tool that gets source files, executables, dlls, and lots of other artifacts. Results can be saved to a file, uploaded to S3, or sent to a waiting network server.
A common setup in a corporate environment is to use the EDR to launch the Collector, and it sends data back to the waiting server.
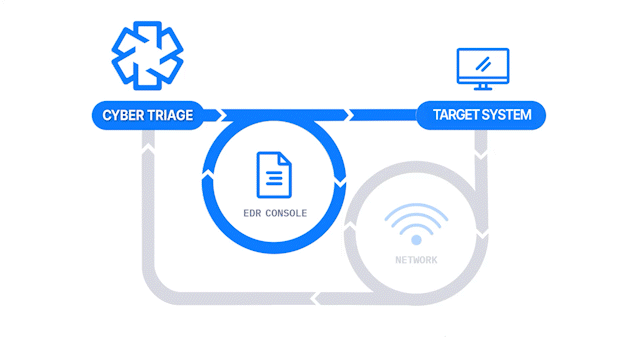
Because the Cyber Triage Collector is a single Windows EXE, you have two choices for using Live Response:
- You can put the Collector into the Live Response Library and launch it with the needed arguments. The downside of this is that it will get killed if it runs longer than 30 minutes.
- You can put a pre-configured Deployer Script in the library and launch it. This will in turn launch the Collector as a different process that will keep on running even if the session is killed after 30 minutes.
There are detailed instructions in the User Manual, but the basic steps are:
- Edit the Deployer script based on your environment. The default settings are to download the Collector from the cybertriage.com site, run it with default settings, and save the result to a local file. You may choose to have the data sent up to S3 or a server.
- Upload the script to the Defender Live Response library.
- Launch the script by typing in ‘run deploy_cyber_triage_collector.ps1’’
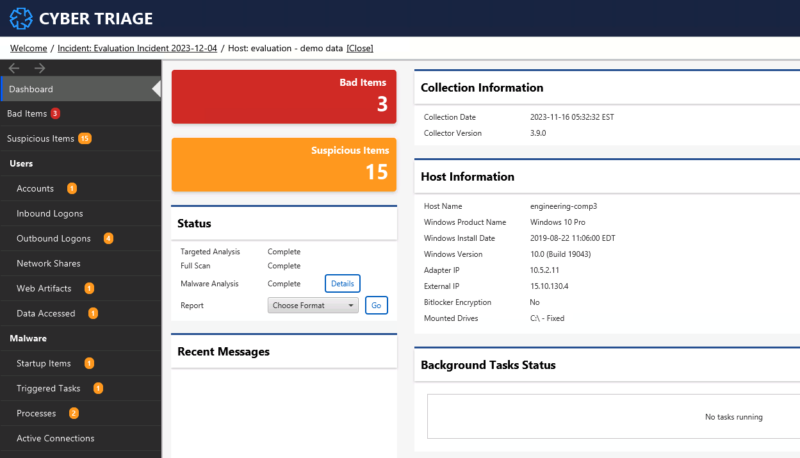
You can then open the collected data in Cyber Triage and see how it analyzed the data to identify the bad and suspicious artifacts. This is much faster than going through a set of text files to understand what the attacker did.
Integrate Today
If you are already a Cyber Triage and Windows Defender customer, then try out the integration today and contact support if you have any questions. If you are looking to get more data from Defender, then try out Cyber Triage using the evaluation form. Our team is available to help anyone with their integrations.