With its agentless approach, the latest Cyber Triage release gives users more control over what endpoint forensic artifacts are collected. This enables:
- Faster data collection
- Faster decision making.
The 2.6 release has several other updates, including:
- Upgraded and improved Volatility integration for memory forensics
- HTML report updates
- More heuristics to flag suspicious artifacts.
This post focuses on the ability to specify what data types to collect.
Collect Only the Artifacts You Need
Triage means different things to different people at different times. Sometimes you want to review 10 types of artifacts and sometimes you want to review one. If you want to review only one, then you’re wasting time if you always collect 10.
To make your investigations as efficient as possible, you need control over what gets collected. Let’s look at some examples:
- You see suspicious network traffic from an endpoint and want to know what process has that port open. To do that, you’ll need to collect only network port and process information.
- You’re investigating an endpoint and see a suspicious remote login from another endpoint. You want to see who was remotely logged into that system to see if it was being used for lateral movement. For this, you need to collect only event logs from that remote system.
- You find a piece of malware located in the RunOnce registry key. You want to hunt the network to find other computers that have the same key. For this, you only need to collect the startup items.
When you know that you’ll be doing a full triage of an endpoint, it makes sense to get all of the data that you can. But if you have only one or two questions that you need to answer, it’s faster to get only the data you need.
Specifying Collection Artifacts
While many users appreciate the fact that Cyber Triage can collect lots of artifacts with only a few mouse clicks, we’ve now given you the option to make a more targeted collection. When you create a new session in Cyber Triage, you now get to pick each data type that’s collected:
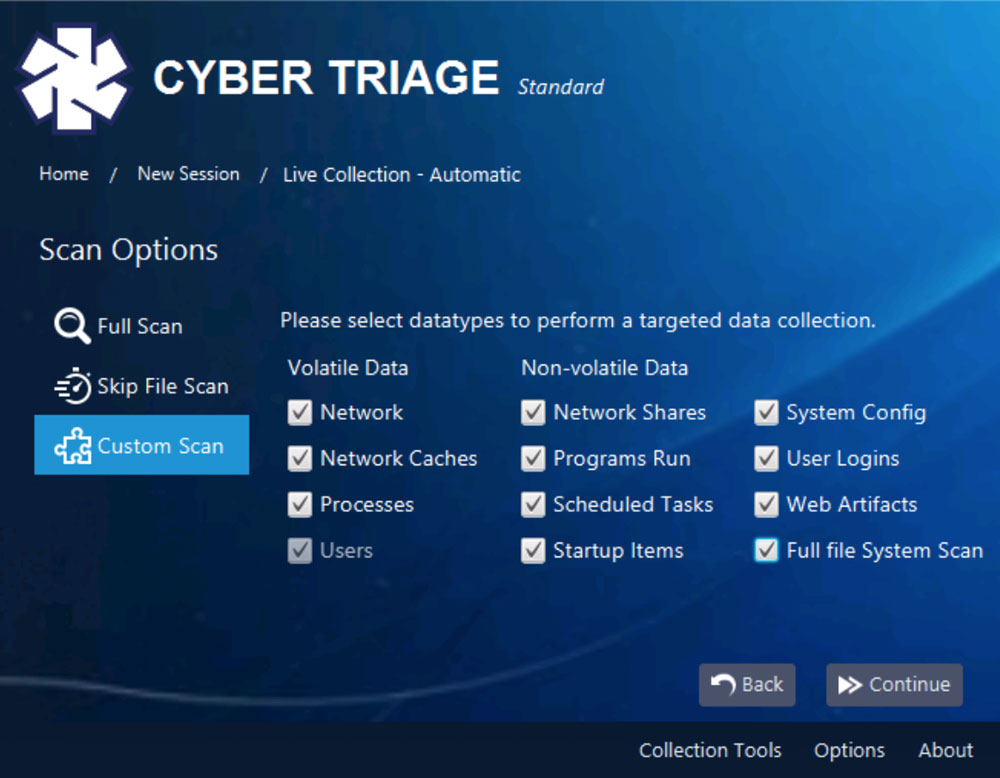
Full Scan will still allow you to collect everything and scan the entire drive without needing to think about the details. Skip File Scan collects everything, but skips the final scan of all files (which is the most time-intensive step). Custom Scan allows you to pick which types you want to collect:
- Network collects network connections and open ports
- Network Caches collects DNS cache, ARP cache and routing tables
- Processes collects process names, hierarchies and associated executables
- Users collects information about user accounts and who was logged in
- Network Shares collects information about network mounts and UNC references
- Programs Run collects data and executables from Shimcache, Prefetch, and other locations about the programs that were executed on the system
- Scheduled Tasks collects data and executables for programs that could be run based on a schedule or triggers
- Startup Items collects data and executables for programs that are started each time the computer starts
- System Configuration collects information about security and audit settings on the computer
- User Logins collects events about when users locally and remotely log in.
- Web Artifacts collects web cookies, history and downloaded information from browsers
- Full File System Scan looks at each file and collects those that are suspicious.
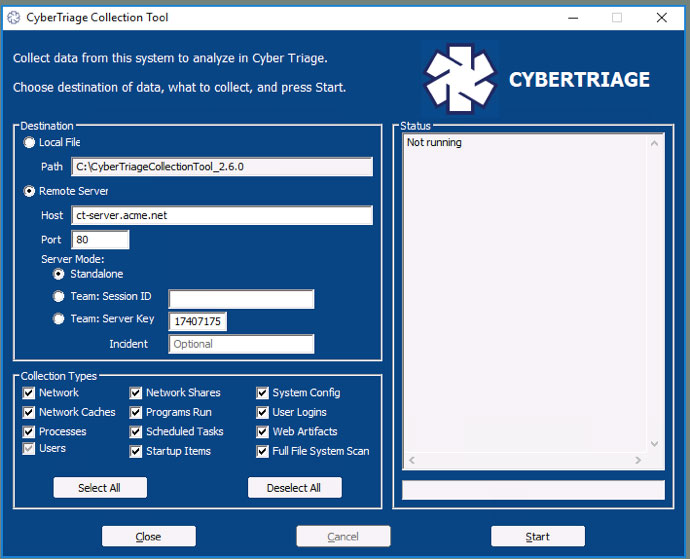
You also have the same options when running the Cyber Triage Collection tool from a USB drive:
Try It Out
This new feature can save you time when you know exactly what you want to collect. However, we’ve preserved the ability to collect everything that could be relevant and contain evidence.
If you want to automate your endpoint investigations and save time, then try out the latest Cyber Triage by using this form.