Ransomware cases are everywhere and Cyber Triage users are more frequently responding to them. Recent Cyber Triage releases (3.0.1 and 3.0.2) have been adding ransomware-specific features and this post covers them. Download the latest version from here.
Investigating Ransomware
At the end of the day, investigating a ransomware attack is a lot like investigating other types of attacks. All attacks ultimately go through a standard set of phases of:
- Obtaining initial access to a network
- Installing some form of persistence for future access.
- Performing reconnaissance to find things that are relevant to them.
- Undertaking their ultimate goal, which varies by group. It could be to monitor, steal data, or encrypt data.
The last step in the process is what what makes ransomware unique. The attacker encrypts data until a ransom is paid.
We’ve talked in past blog posts about the phases of responding to Ransomware, but the true value of Cyber Triage comes when you want to figure out how they got into the network, what persistence mechanisms they installed, and how they deployed the ransomware. If you don’t know those, then you can’t keep the attackers out (regardless of if you pay the ransom or not).
New Ransomware Features
The most recent Cyber Triage releases introduced some new features to make it easier to work your way backwards from an encrypted system.
Ransom Note Detection
In addition to encrypting files, attackers will leave behind a note to let you know where to send the ₿ (BitCoin). Cyber Triage will identify ransomware notes and flag the first and last ones created. This gives you a time span of when the encryption was happening. Cyber Triage does not flag every single ransom note because there are often thousands and at some point they don’t provide additional information.
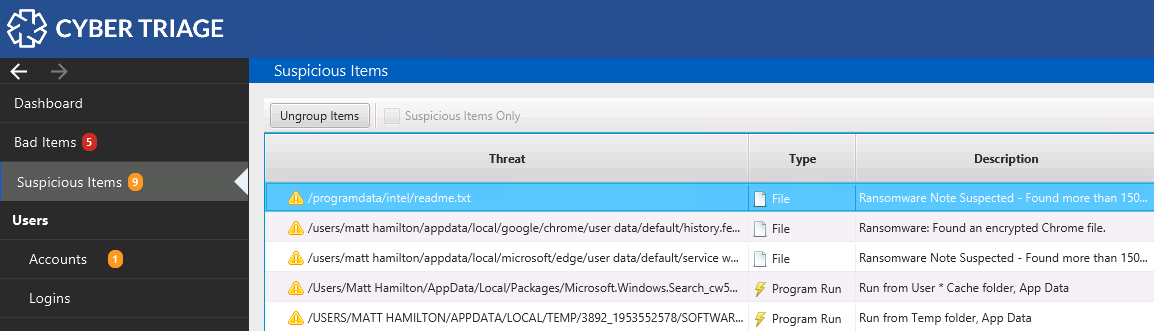
Cyber Triage uses two techniques to identify ransomware notes:
- A list of common ransomware note names.
- A heuristic that looks for lots of files with the same name and size. This allows you to detect notes that have unique names or really common names (such as readme.txt).
With this data, you can then work backwards to look at activity before the first files were encrypted. This may show what program was used (if it wasn’t already flagged by a malware scan), the user account involved, etc.
Encrypted Database Detection
Each flavor of ransomware is different and encrypts different files. Sometimes the ransomware will encrypt files that your DFIR tools rely on to extract artifacts from. As an investigator, you’ll want to know that you are not finding a certain kind of artifact because it’s encrypted versus the system wasn’t producing that form of artifact.
An easy example is web browsing history. The ransomware may move the browser database files and encrypt them. But, the browser will happily make a new empty database when it realizes the previous one is gone.
When you examine that system, it will have a database with no history or cookies. You may conclude the user didn’t use that type of browser or that maybe your investigation tool has a bug. But, in reality, the data has been moved and encrypted to a new file.
Cyber Triage will now look for encrypted versions of key files, such as browser databases, as it is collecting from the target system.
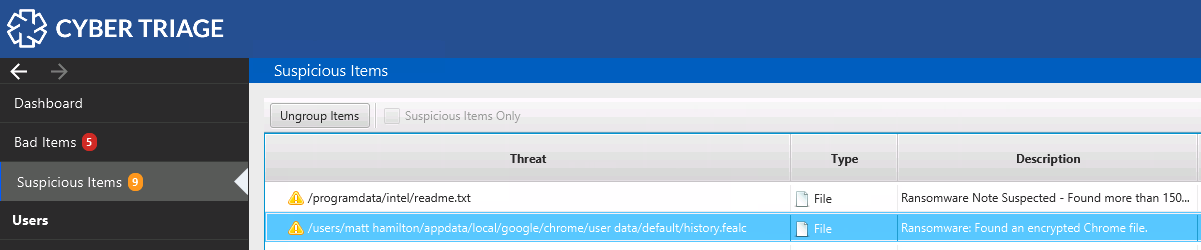
This allows you to easily realize that some artifacts are not visible because they are inside of encrypted files.
Existing Features
While these are two new ransomware-specific features, it’s important to remember that many of the existing features are also useful during a ransomware response.
- Collection and analysis of remote logins to look for lateral movement
- Collection and analysis of startup items to look for persistence mechanism
- Collection and analysis of programs run to look for launching of malware and reconnaissance tools.
Cyber Triage Basics
Cyber Triage allows you to easily and quickly collect and analyze digital forensic artifacts from live systems. It uses automated scoring techniques to quickly highlight the data that is most likely to be relevant and hide those that are not. Once you identify artifacts that are likely relevant, it will recommend additional ones.
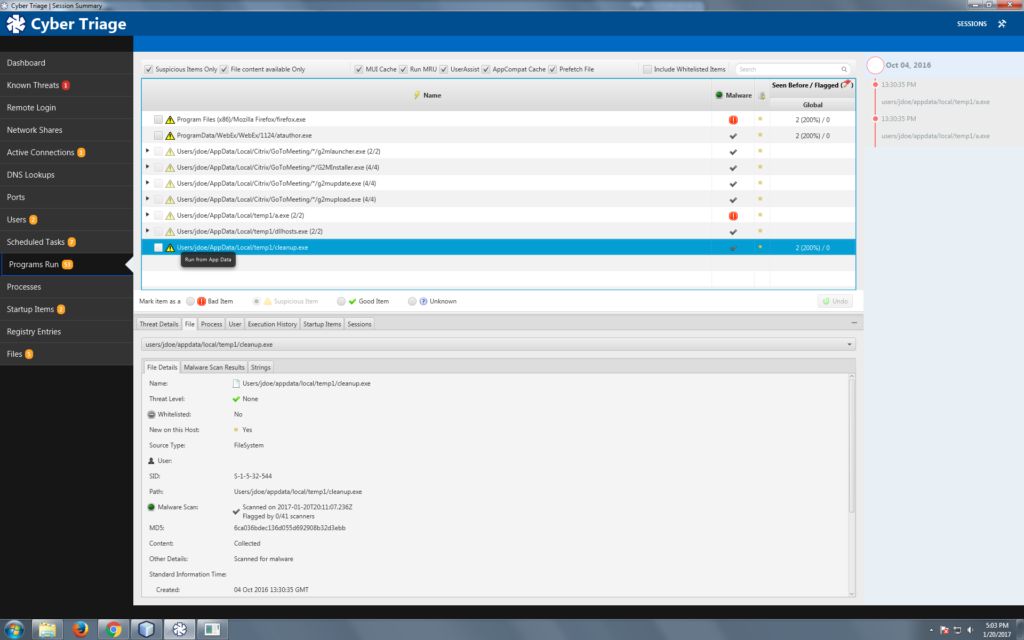
Cyber Triage uses advanced analytics to make sure you can complete your investigations faster and get the attackers out.
Use It Before You Need It
You don’t want to start looking into investigation software after your first ransomware case hits. Try out Cyber Triage today and see how its automation will help you solve investigations faster. Use this link for a free 7-day evaluation.
