The latest 3.1.0 release of Cyber Triage has lots of new features in it to make you more efficient. The full list is here and this post is going to cover the two biggest features of artifact searching and OS Configuration Settings.
Get the latest evaluation version of Cyber Triage.
Artifact Search
What Is It?
This new feature allows you to search the data collected from a host for keywords. For example, if you search for “encryptor.exe”, you may get:
- File names that are named “encryptor.exe”,
- Program run entries for programs named “encryptor.exe”
- Web artifacts for when the file was downloaded
Why Do You Care?
We know you’re going to like this because it’s been a common request for a while, but our previous database prevented us from adding it. Responders can use this feature to look for specific host names, IP addresses, or folder names to find relevant artifacts based on something they already know.
The Cyber Triage scoring features help you find things you didn’t know about. Search is about helping you find things that you know a little something about.
Let’s tie this feature back into our usual themes of making you most efficient:
- Speed: The search feature will make your investigations faster by allowing you to more quickly find artifacts based on name or metadata. For existing Cyber Triage users, they previously had to go into each artifact type and do a search. They can now do one search instead of ten. The alternative for responders who use more ad-hoc tools is to search through dozens of text files.
- Comprehensiveness: This feature will make your investigations more comprehensive by helping to ensure that all artifacts are searched when you know what you’re looking for. It’s easy to forget about a set of collection tool outputs to look in or search.
How Do You Use it?
Once you’ve loaded data into Cyber Triage using one of the various collection methods, then you can use the “Search” menu item in the lower left.
Simply enter a search term in the top box and see the results. In this case, we searched for a malware name and found a file that had the malware family name in its metadata.
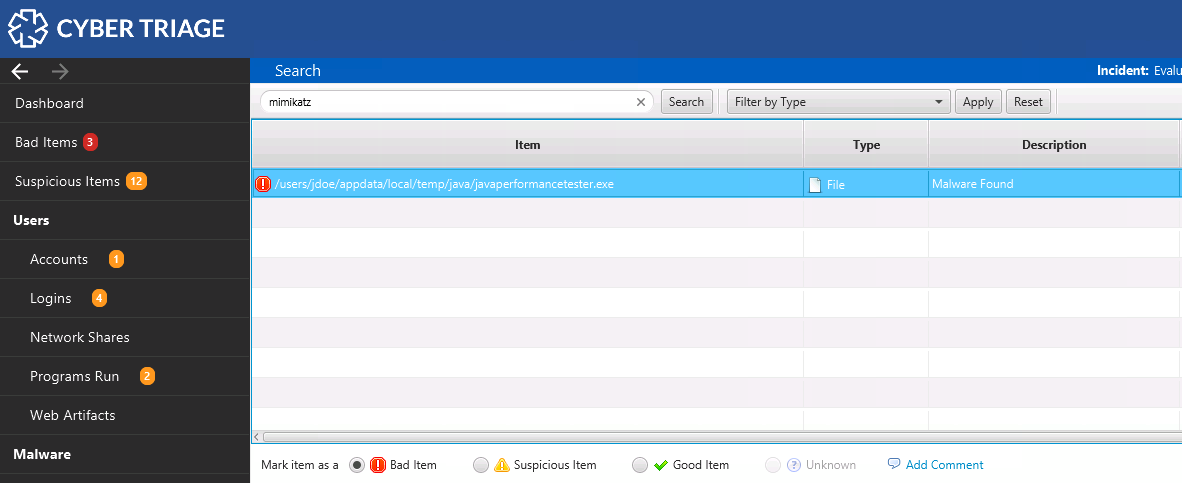
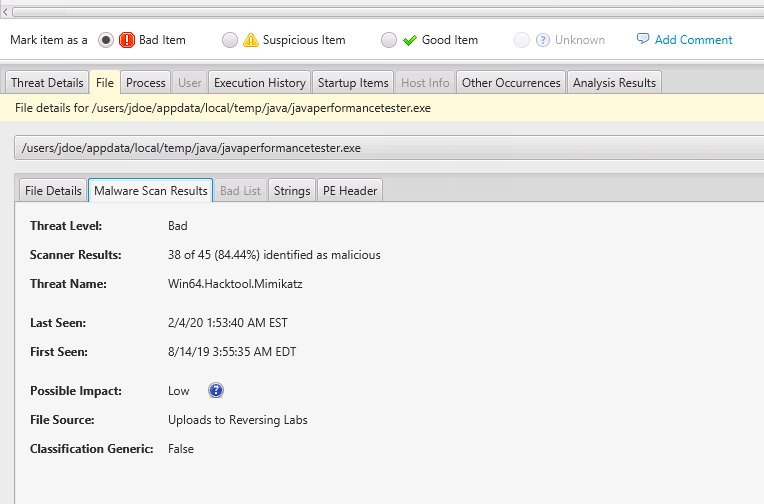
You can select any of the items and view the details on the bottom
OS Configuration Settings
What Is It?
The latest Cyber Triage release has several changes around OS Configuration Settings, which store various settings, such as if Windows Defender is enabled.
Notably, the new release:
- Allows OS Configuration settings to get scores.
- Assign settings to a group to make them easier to navigate. For example, there is a “Security” group and another called “Log and Audit Data”.
- Adds context about what a setting means. A future release will associate these settings with MITRE ATT&CK.
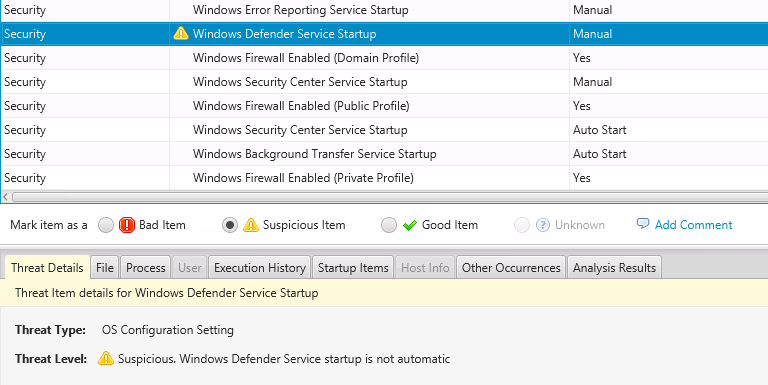
- Will score Windows Defender and Event Log as suspicious if they are disabled.
- Will detect when Windows Defender or Event Log are supposed to be running and are not.
Why Do You Care?
You need to understand some or all of the OS configuration during your response. Attackers can modify settings to make their attack easier. This release makes it easier for you to review the settings and allows Cyber Triage to flag suspicious settings.
These changes will help you by:
- Speed: You’ll more quickly identify settings that were changed because of the scoring. Cyber Triage will flag these in the background instead of you needing to review them individually. More analytics will be included in future releases for Volume Shadow, Automatic Updates, etc.
- Comprehensiveness: You’ll get a broad view of the OS setup from the diversity of settings that are collected. Cyber Triage has knowledge about where to find important settings and what the default settings are. While it is of course important for you to know what settings are and why they are relevant, it is very difficult for an examiner to know all of these.
How Do You Use It?
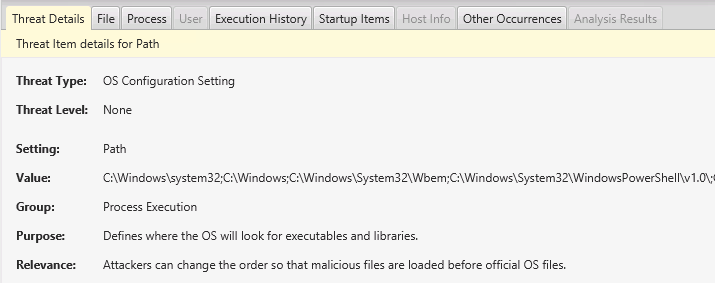
You can see the OS Configuration settings using the “OS Config Settings” menu on the left. Choose that and then review the settings that are grouped by one of:
- Log and Audit Data
- Network Resolution
- Process Execution
- Security
- etc
Select any of them and get the context and why this is important from the panel below.
If a service was not enabled, you’ll see it appear as a suspicious item.
Conclusion
Each Cyber Triage release is focused on making you more efficient and we hope you see the value of these new features. If you have a feature request, then please make sure you reach out to Customer Support.