Cyber Triage version 3.3.0 introduces many new features to make your responses faster and this blog covers three highlights. The full list of changes is here and this blog will focus on:
- New “Data Accessed” Artifact Category – The “Data Accessed” category includes files that the user opened or saved. Cyber Triage now parses several Most Recently Used (MRU) artifacts and displays them. This can help you determine what user’s were looking at.
- Malicious PDF / MS Office Documents Detection – Many of the new Data Accessed artifacts will be PDF and Office documents and they are now locally scanned for malicious attributes. This helps detect if the user was targeted by malicious content.
- Import Logical Files – Continuing on the theme of allowing users to import data without using the Cyber Triage collection tool, you can now import logical file structures. This allows you to take advantage of the Cyber Triage scoring even if you collect with some other method.
Get the latest evaluation version of Cyber Triage.
New “Data Accessed” Artifact Category
What Is It?
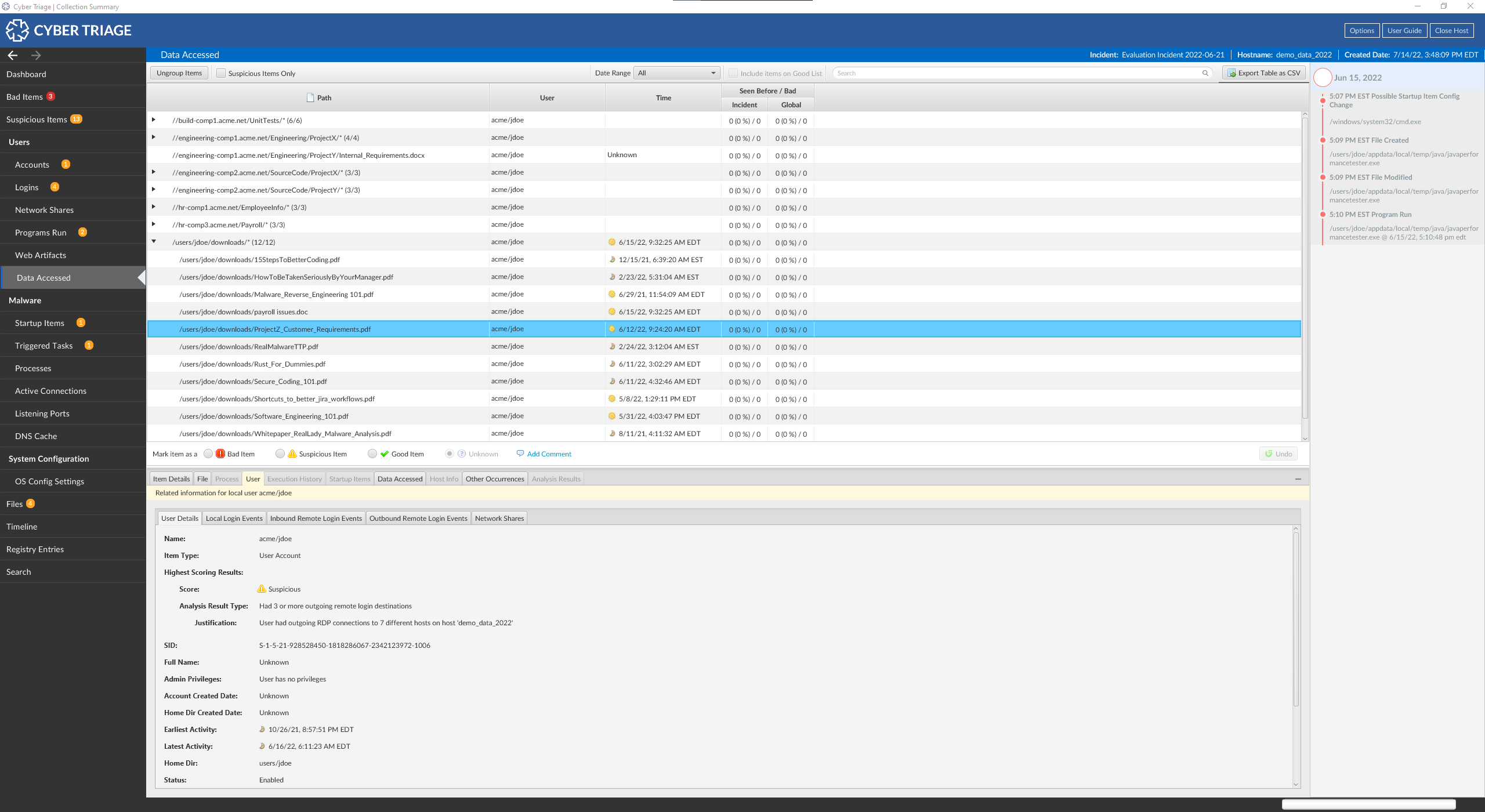
This new feature adds a brand new section to the UI that shows what files was opened or saved by a user on the host machine. This can help the responder identify if a user account was opening random documents and may show if a malicious file was opened.
To populate this section, we now parse new artifacts into Cyber Triage, such as:
- Recent Folder and LNK files
- Most Recently Used (MRU) by extension for open/save dialogs
- Files opened by IE / Edge browsers
- Office MRU
- With more on the way!
Example Use Cases:
- Attacker Activity on Host Machine: Attackers will open files if they are looking for sensitive information. If you have detected potentially malicious activity on a host computer, you can use this artifact category to drill down into the data that a “user” has accessed. If the account was compromised, this can help you determine what the attacker was looking for.
- Phishing Attack: If an attacker sent a victim a malicious Office or PDF file as an email attachment, it would then be listed as a recently opened file. That will quickly point Cyber Triage to that file.
How To Use It:
In the Navigation Menu on the left side of the Cyber Triage dashboard, you will see a new section entitled “Data Accessed”. Click this button and you will be brought to a new section which outlines the data available for review.
In this section, you will see any data (files, etc) that were accessed by user’s on the host machine.
Adobe PDF and Microsoft Office Doc Scanning
What Is It?
Cyber Triage now offers scanning and scoring of Adobe PDF and Microsoft Office files to determine if potentially deployable packages are embedded within them. We added this feature to scan documents collected with the new Data Accessed artifact category.
While many online services can scan documents, many of our users are concerned about uploading files with PII. Therefore, we implemented a basic scanner within Cyber Triage.
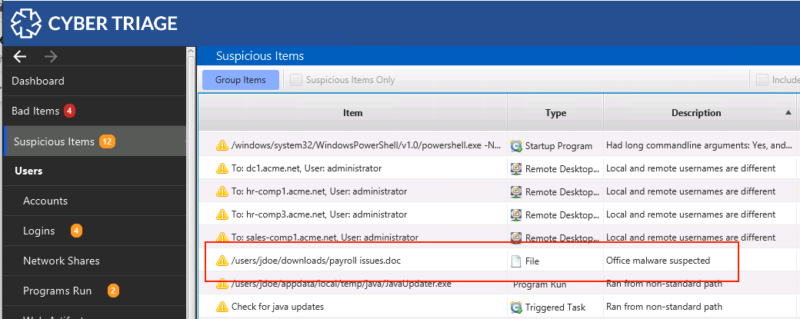
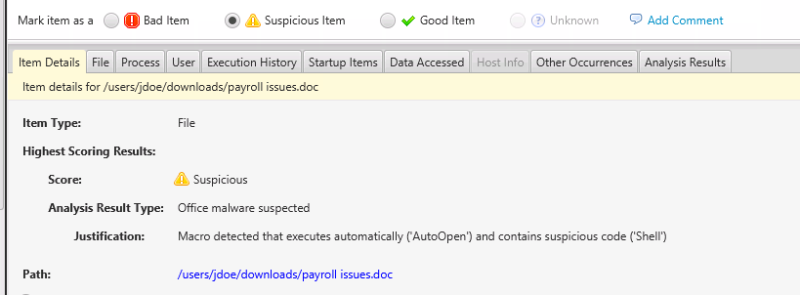
In this first implementation, Cyber Triage focuses on flagging files that have Automatic Actions that occur when a user opens a file or displays a page or that have scripting in them.
Example Use Cases:
- Phishing Attack: A victim is sent a malicious document and opens it. Upon examination, the malicious document is collected by Cyber Triage and brought to the attention of the examiner.
How To Use It:
There is nothing special to do. Any Office or PDF file that is collected will go down the analysis pipelines and reviewed. If it contains any potentially malicious elements, Cyber Triage will mark it as suspicious.
The viewer on the bottom will indicate why Cyber Triage flagged it. In the below example, it’s because a program was launched via “Shell” when the document was opened.
Import Logical Files / Folders
What Is It?
Sometimes responders and victims will copy individual files from a system and provide them to you for analysis. We recommend using our Collection Tool, but we also want to support scenarios where it wasn’t used.
With Cyber Triage 3.3.0, you can now import a folder of files and it will then parse files and score artifact. This continues on our theme from the previous release when we made it possible to import data from a KAPE VHD. In fact, with this new feature, you can import the contents of a KAPE Zip file too (but you need to unzip it first).
Example Use Case:
- Logical File Dumps: An incident responder cannot get a full disk image of a device or use the Collection Tool, and has only received a logical file dump of the device. Cyber Triage can now examine and score these files.
How To Use It:
Before we go into the specific workflow, it’s important to know that files must be at the same relative path in order for Cyber Triage to detect and parse them. As an example, let’s consider the SAM registry hive.
- It needs to be located in a folder with “windows\system32\config” as the parent. For example, “c:\cases\ACME\host1\windows\system32\config\SAM”
- You would point Cyber Triage to the “c:\cases\ACME\host1” folder
- That folder should also have the SOFTWARE and SYSTEM hives if you also want them to be parsed.
Now let’s look at the process:
- Create an Incident and choose “Add New Host” from the incident dashboard.
- Simply use the new “Logical Files” button on the Add Host panel to access this new feature.
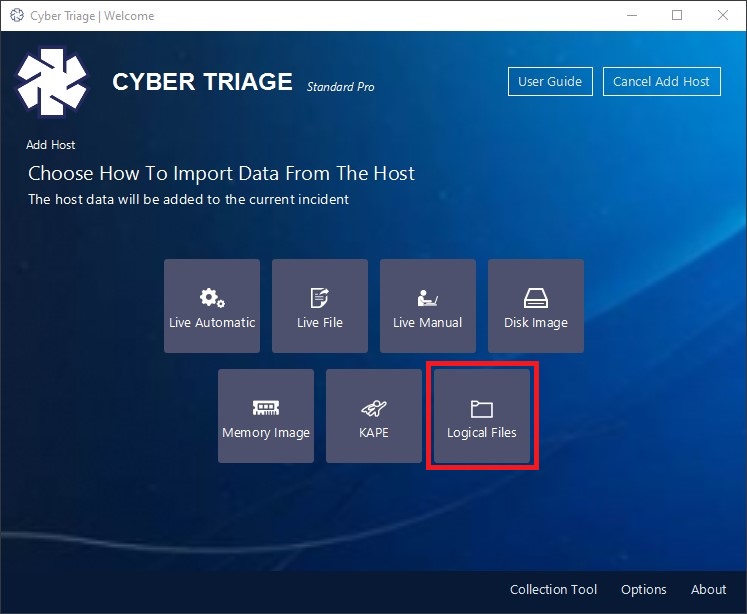
- Give your collection a name and point Cyber Triage to the folder containing your logical files.
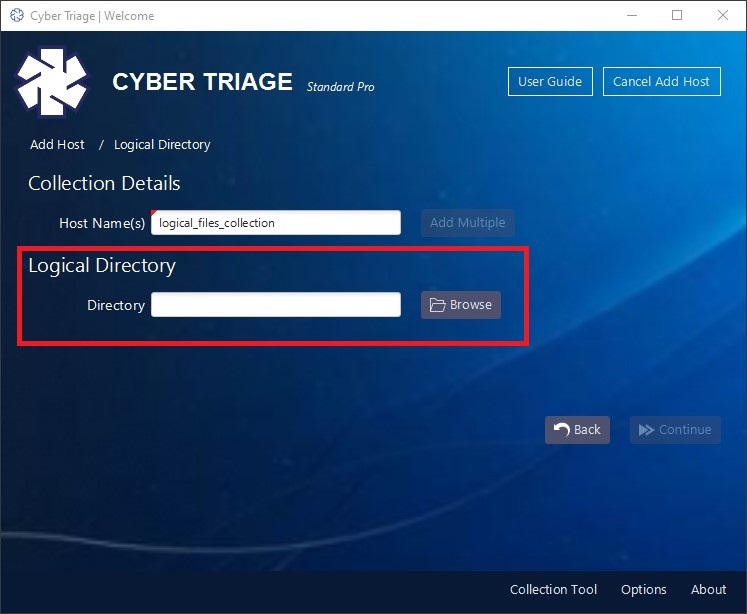
You will then be prompted to configure what types of non-volatile data to extract from the imported files. You may see warnings if Cyber Triage looks for files that do not exist in your collected data.
And that’s it for 3.3.0!
We hope you enjoy this release. If there are any questions or you need assistance with any of these new features (or any questions at all) please reach out to support@cybertriage.com.
Get the latest evaluation version of Cyber Triage. Or check out the Cyber Triage User Guide for help.