With the 2.1.10 Cyber Triage release, you can now integrate with Splunk. This allows you to remotely start collections about suspicious endpoints and bring the results back to Splunk for multi-source correlations and alert triage.
This blog covers the basics of the integration. To get the latest version of Cyber Triage, contact us.
Capabilities Overview
The Cyber Triage add-on for Splunk provides two new capabilities, allowing you to:
- Trigger a collection of a remote endpoint to be started so that it can be investigated for malicious behavior
- Import the Cyber Triage analysis results into Splunk so that the data is available for future investigations
Both of these capabilities make your team more efficient. Resolving incidents faster maximizes your analysts’ time because she doesn’t need to wait for the collection to happen, and having the most context in your SIEM improves future alert triage.
To trigger a collection, you’ll need the Team version of Cyber Triage, which enables collaboration and has a REST API.
Installation
To integrate with Splunk, you’ll need to install the Cyber Triage Add-on into your Splunk installation. It will be available via “Find More Apps” or from Splunkbase.
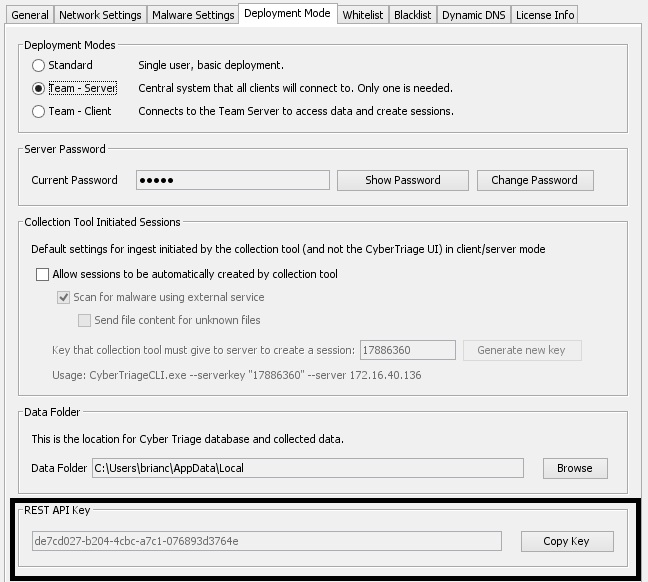
To configure the add-on, you’ll need to first get the REST API key from your Cyber Triage server. Go to the “Options” panel of the server and choose the “Deployment Mode” tab. The bottom of the window has your unique API key that you’ll need to enter into the Splunk add-on.
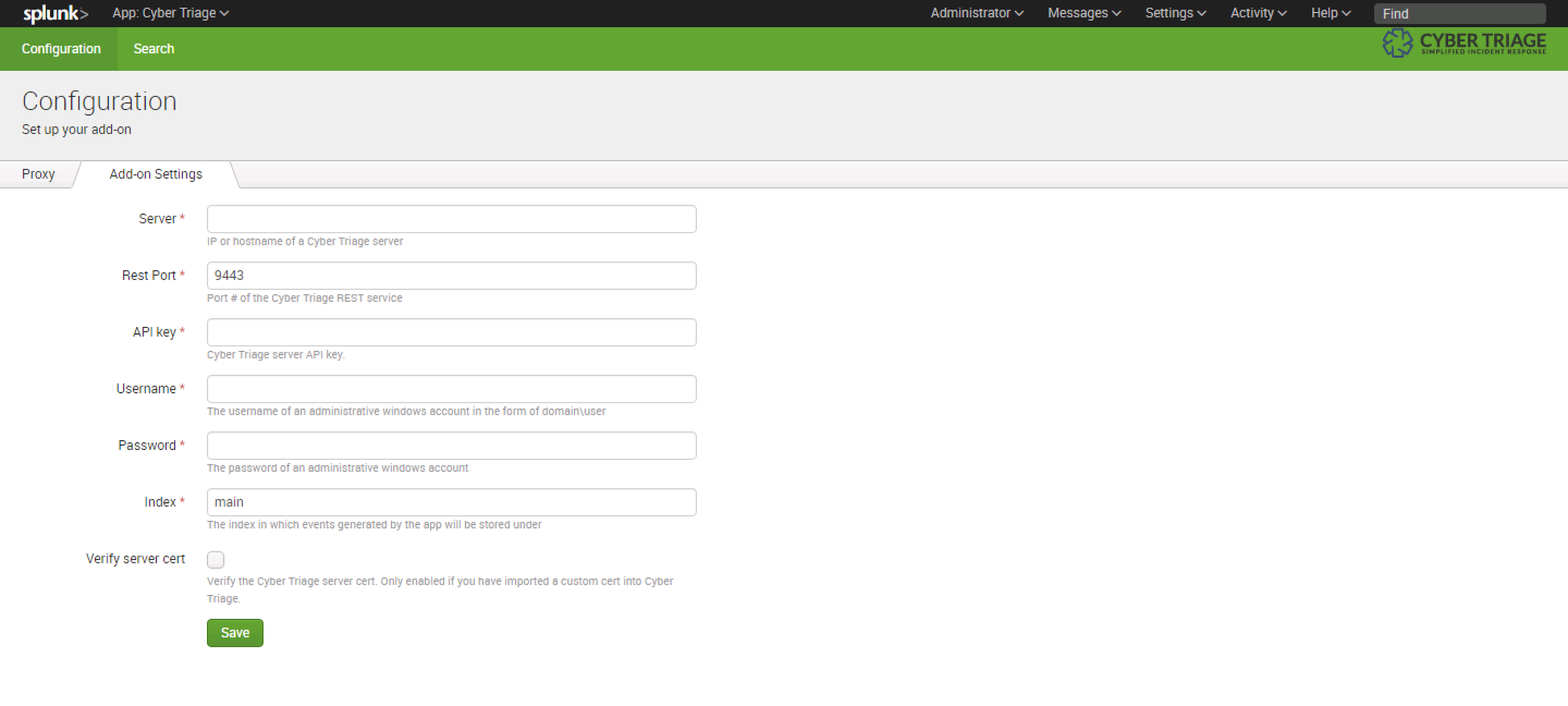
Next, configure the Splunk add-on, by specifying:
- Hostname where Cyber Triage Server is running
- REST API Key (from the previous “Options” panel)
- Login and password of an administrator account on the remote endpoints
Setting Up A Trigger
To configure Splunk to start a Cyber Triage investigation based on an alert, add a “Trigger Action” to your Splunk alert configuration. Choose the Cyber Triage “triage endpoint” action.
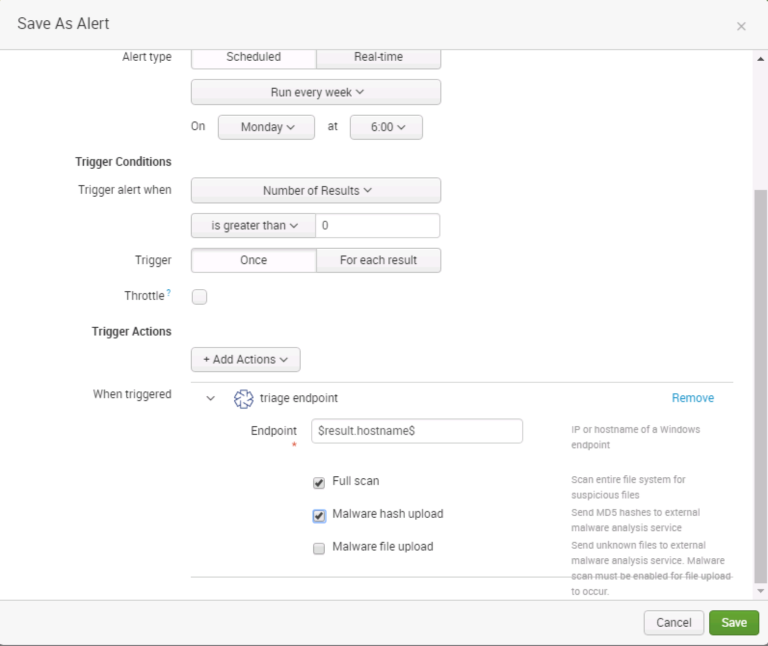
The action requires an IP or hostname of the endpoint you would like to investigate. To have that value passed into the action, choose the field from the event that contains that data (ex. $result.hostname$).
You can also choose to configure some of the analysis settings, such as performing a full scan (which looks at each file on the endpoint), uploading MD5 hashes to OPSWAT, and uploading file content to OPSWAT.
When the trigger action executes, it will produce an event that stores whether the action was successful. If the action was successful it will contain the session ID for the session that was created on the Cyber Triage server. The event is, by default, stored in the main index. You can change this setting in configuration panel for the Cyber Triage add-on.
Importing Data
Once you’ve conducted an investigation in Cyber Triage, you may want to archive the results in Splunk. When performing an investigation in Cyber Triage, you can correlate with previous incidents to see when an item was previously seen (such as a running process). When you import your data back into Splunk, you can now correlate with previous incidents during your initial alert triage stages before you decide to start a Cyber Triage investigation.
To use this feature, conduct your investigation in Cyber Triage as normal. Collect the endpoint data, review the suspicious items, and mark as good or bad. At the end, you should generate a JSON report (new in 2.1.10).
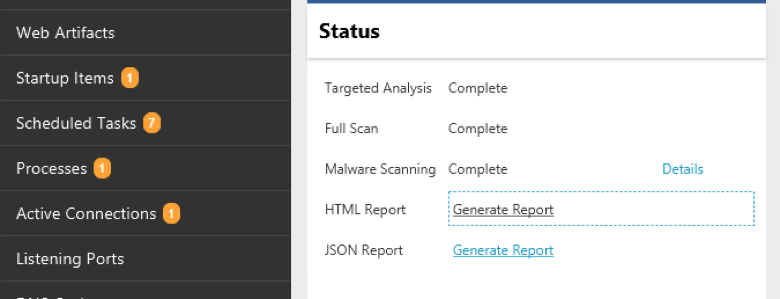
To bring that data into Splunk, choose the “Add Data” button and select the JSON report file. Next, choose the source module that will map the Cyber Triage data types to the Splunk CIM. This enables some events collected by Cyber Triage to be automatically integrated into CIM compliant searches, dashboard, alerts, etc. that you may already have. You can find the “cybertriage” source in the Application category.
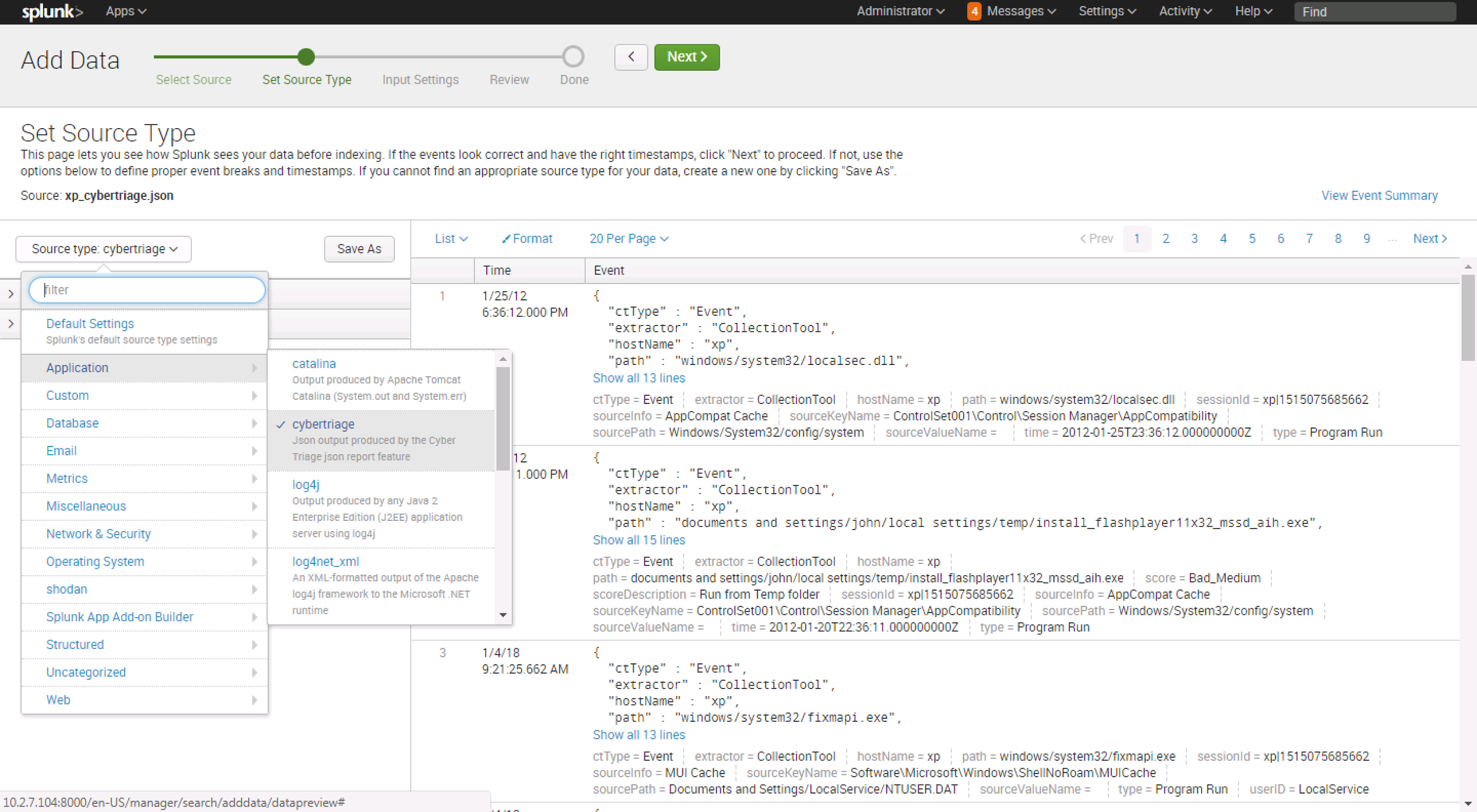
The data should now be available for you to search and later correlate with.
Integrate Today
These new Splunk integration features (in addition to the existing Phantom features), allow you to more efficiently respond to incidents. If you don’t have Cyber Triage Team, but want to try it, send a message to sales@cybertriage.com.
If you want to download the Standard (desktop) version of Cyber Triage, use this form.