Want to learn the secrets of Shellbags? Stick around. DFIR expert Chris Ray lays out everything you want to know, from how they work to how to do DFIR analysis on them.
Now, let’s explore the mysteries of the shells contained in the bag.
Jump to…
What Are Shellbags?
Where Are Shellbags Stored?
Shellbags in Digital Forensics
How Shellbags Work
Investigating an Intrusion?
Shellbag Anti-Forensics
Analyzing Shellbags for Forensic Investigations
Challenges of Shellbag Analysis
What Are Shellbags?
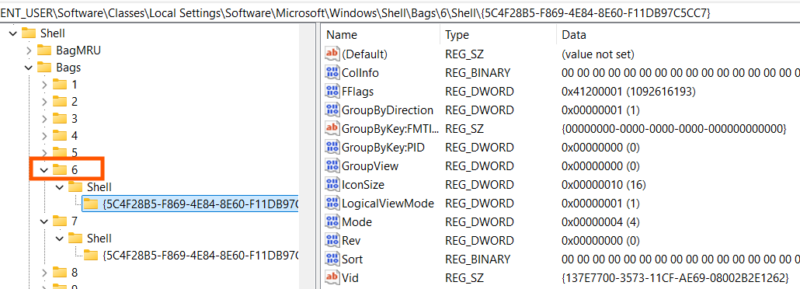
If you have ever noticed Windows remembered where you last left the Explorer window or the custom columns you’ve added for a specific folder view, then you have had a run-in with Shellbag data.
Shellbag Definition: “Shellbags” refers to a group of registry keys and key data Windows maintains to remember user viewing preferences in Windows Explorer and Windows Open/Save dialogs, like:
- Window location/size
- Columns to display
- Column sorting
- Icon size
Examples of Shellbags at Work
Viewing Preferences in Explorer before Changes
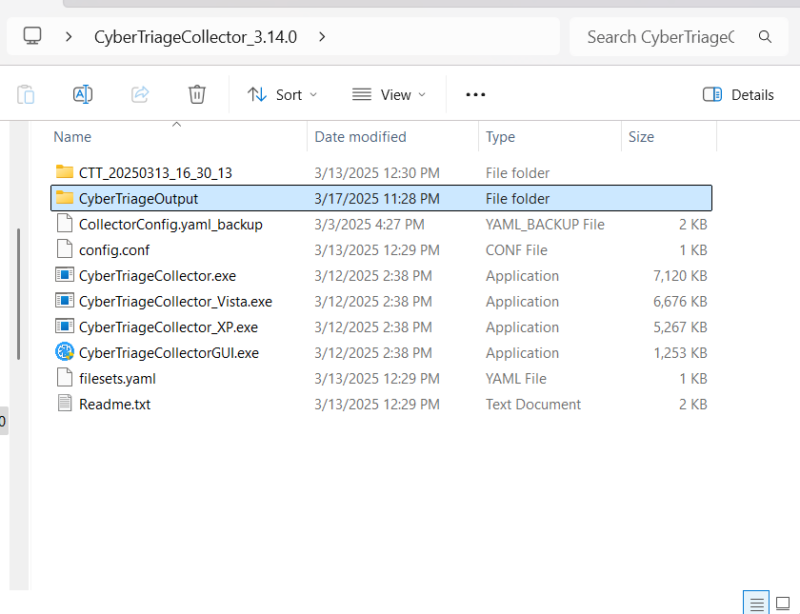
Viewing Preferences in Explorer after Changes
Viewing Preferences Are Different in Open/Save
Shellbags are also a key forensic artifact for answering the question:
What folders have users interacted with on the system?
This is largely because Shellbag registry keys keep track of every folder a user has visited, even after a folder has been deleted.
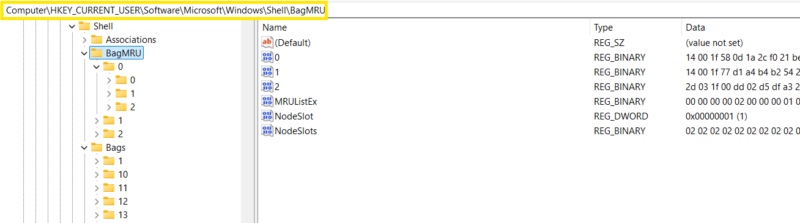
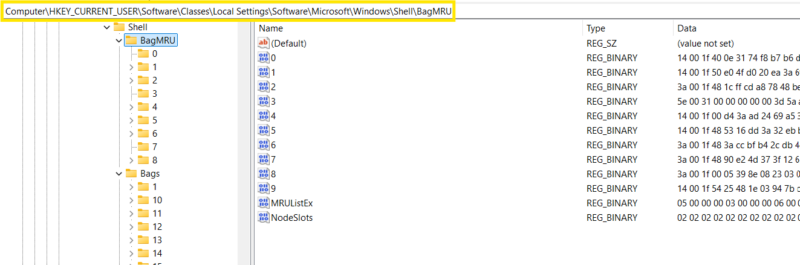
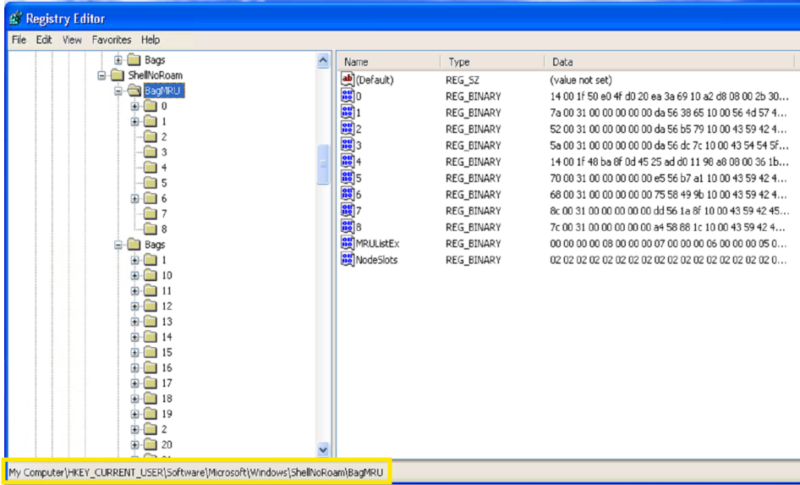
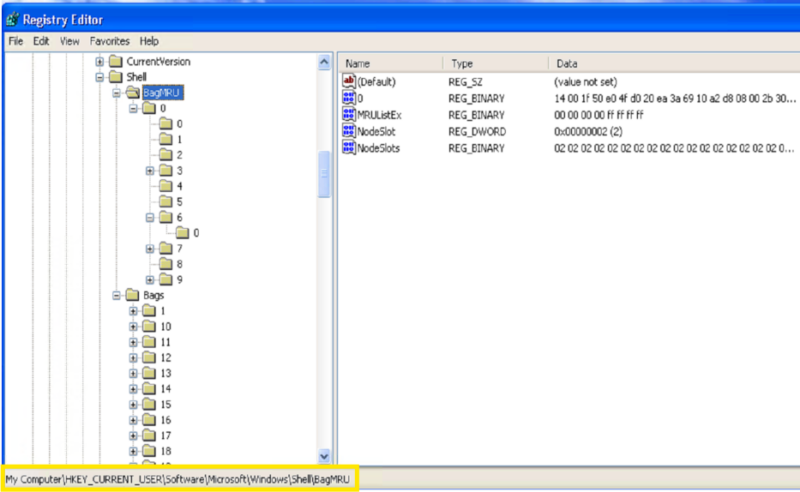
Where Are Shellbags Stored?
Windows Shellbags are stored in various locations within the registry depending on the Windows version and the type of data being logged.
The keys of interest for investigators are:
- Bags
- BagMRU
Those keys can be found under the following top-level Shellbag keys:
Shellbags in Digital Forensics
Shellbags can contain a wealth of information on which folders a user has accessed. However, because the exact details of how it works are not publicly available, it can be difficult to fully understand the data. Investigators should use other artifacts to verify findings and test specific scenarios to ensure they understand the data and how it got there.
That said, here is the key info from Shellbags:
| Info | Notes |
|---|---|
| Full path to folder | Even for deleted folders. |
| If folder was accessed | There are scenarios we will discuss later where an entry can show up but doesn’t indicate the user accessed folder content. |
| User who accessed folder | Based on the registry hive. |
| Modified, accessed, and created timestamps for folder accessed | This is only recorded the first time the folder is put into Shellbags. |
| First and last time user accessed folder | Based on the last write time of a registry key and can only be used in certain situations to infer the first and last access time for a folder. |
| User preferences applied to folder | This can help prove that a user had intent to interact with a given folder. |
How Shellbags Work
High-level Summary
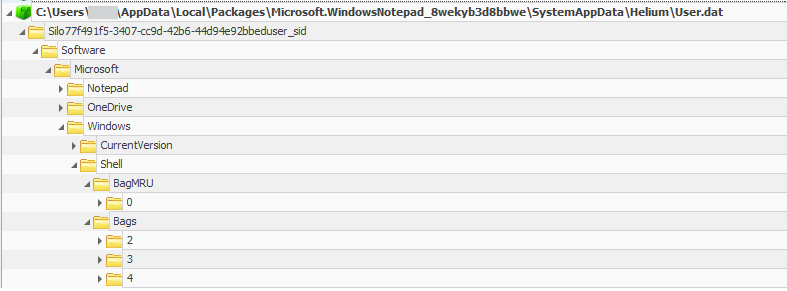
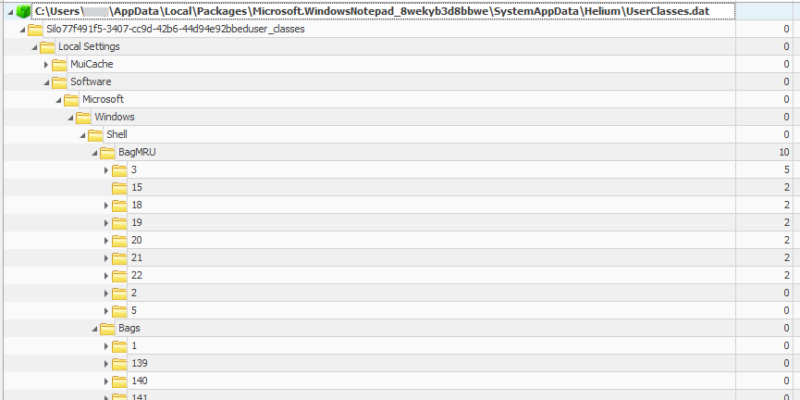
Shellbags are generated by Windows when browsing to folders or folder-like files (archive formats like .zip supported by explorer) in Windows Explorer or Windows Open/Save dialogs.
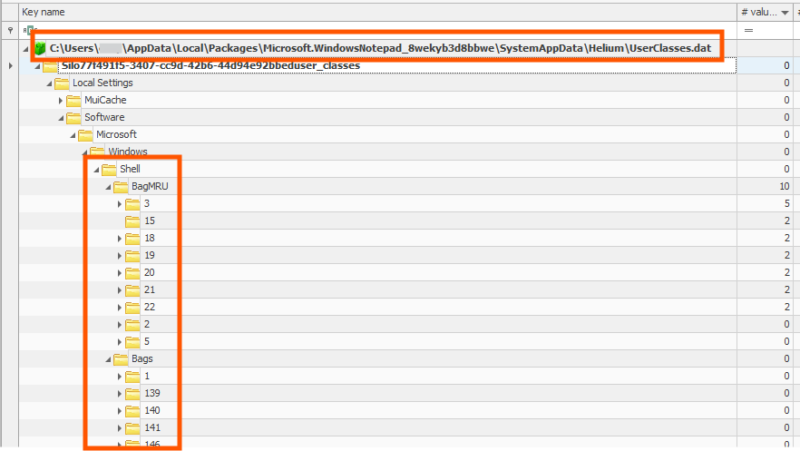
If the app that opens the Windows Open/Save dialog is a Windows App, Shellbag data will not be recorded in the normal user hives but in the app-specific registry hive.
Not every entry in Shellbags directly indicates a user has accessed the folder.
Example:
Shellbags will record each folder up to the folder opened, even if the user never directly browsed those folders. Folders not directly attempted to visit will not have a “Nodeslot.”
Example:
Shellbags will record a folder access attempt (the user does not have permission to access the folder). The corresponding Nodeslot under the “Bags” key will not have any view preferences, which are always populated when a folder has been successfully viewed.
More Detailed Breakdown
We will not dive into the technical details of how to parse out data from these keys, as it is not trivial and has been documented in numerous other write-ups. Instead, we will provide fundamentals on what the core key and values mean so you can understand how the components of the artifact operate.
There are two keys related to each of the upper-level ShellBag keys we previously mentioned.
They are:
- BagMRU
- Bags
Let’s look at each of these in turn:
| BagMRU | ||||||
|---|---|---|---|---|---|---|
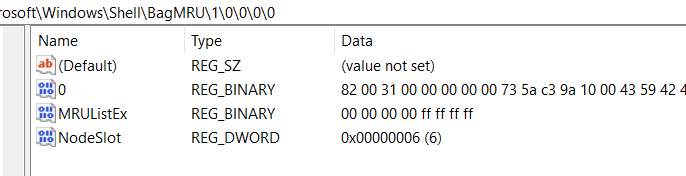
The “BagMRU” registry key is the main key that holds forensic value. It contains the full path to the folder accessed, as well as all of the timestamp information.
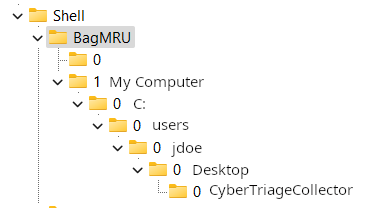 Each of the numbered keys/subkeys under BagMRU can contain the following values:
|
Investigating an Intrusion?
If you’re currently investigating an intrusion, our automated DFIR tool, Cyber Triage, could help you get to the bottom of things much faster.
Shellbag Anti-Forensics
Now that we have a basic understanding of the importance of Shellbags and how it operates, we need to understand where Shellbags fall short and how they can be evaded.
How to Prevent Logging
There is no way to natively turn off the Shellbag feature. However, it is still possible to prevent the logging of Shellbag data by adjusting the permissions on the Shellbag registry keys. This is a similar approach to the one we discussed in our MUICache blog.
# Define the registry key path $registryKeyPath = "HKCU:\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\BagMRU" # Get the current ACL $acl = Get-Acl -Path $registryKeyPath # Define the new access rule (deny write access for everyone) $denyWrite = New-Object System.Security.AccessControl.RegistryAccessRule( "Everyone", [System.Security.AccessControl.RegistryRights]::SetValue, [System.Security.AccessControl.AccessControlType]::Deny ) # Add the new access rule to the ACL $acl.SetAccessRule($denyWrite) # Apply the updated ACL to the registry key Set-Acl -Path $registryKeyPath -AclObject $acl
This PowerShell script adds a deny-all ACL to the BagMRU key.
This prevents Explorer from adding any new Shellbag data. This is limited to the current user and needs to be applied to the other shellbag locations to be thorough.
How to Evade Shellbags
Aside from preventing the Shellbags feature from working, attackers can evade it by exploring folders without the help of Windows Explorer or the Open/Save dialogs.
There are many ways to do this, but here are 2:
- Use PowerShell and command prompt to navigate and search folders.
- Browsing the file system using a GUI through a web browser.
Let’s explain the second strategy.
If you enter “file://c:” into your browser, you’ll be able to browse your file system with a GUI interface:*
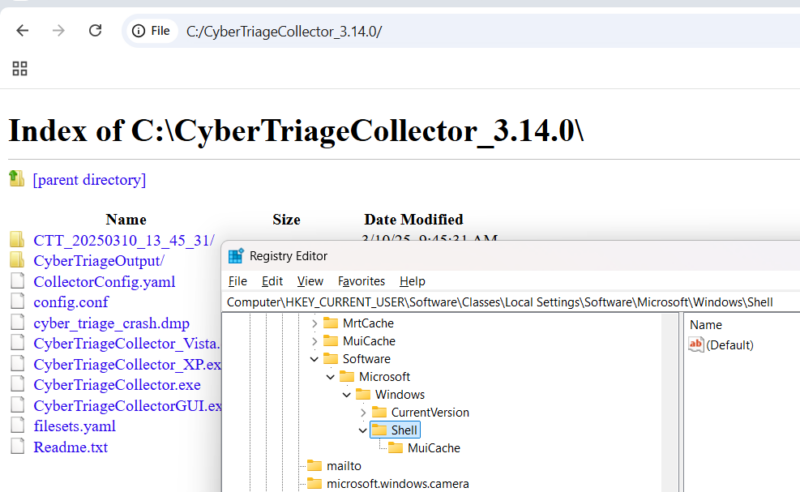
* Better yet, you can do this from a private browsing window to prevent other browser artifacts from recording the files and folders accessed.
Analyzing Shellbags for Forensic Investigations
Analyzing Shellbags is not easily done without special parsing due to its complex structure. As a result we must rely on tools to parse this data in a meaningful manner.
Many forensic tools can parse these artifacts, but 2 solid Shellbag analyzers are:
(Both were created by Eric Zimmerman.)
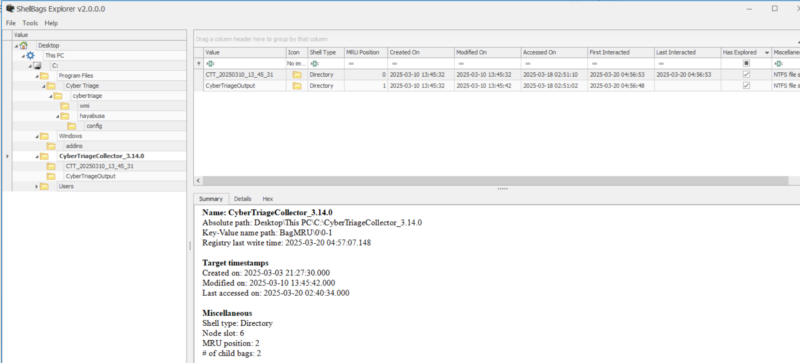
Shell Bag Explorer is a GUI tool while SBECMD is command line driven. Both support parsing folders of registry hives or the current users live registry hive if running as admin.
For the purpose of this, we will show Shell Bag Explorer to show how it makes reviewing shell bags much easier.
Key features:
- Reconstructs the file system view via available Shellbag data.
- Include detailed information for each of the shell items (details tab).
- Provides high-level summary for each folder:
- Folder name
- First/last interacted times if available
- Created/Modified/Accessed folder timestamps
- If the folder was actually visited by the user
Challenges of Shellbag Analysis
- Behavior changes between Operating system.
- Only records folders accessed and not individual files.
- Shellbag data is not easy to review without special parsing.
- Shellbag data has its limitations as it only records data from Windows Explorer and the open/save dialog.
To get a better understanding of how Shellbags work on older systems or a more technical review of the Shellbag data, review these resources:
- 4n4k: Shellbag Forensics: Addressing a Misconception
- Willi Ballenthin: Shellbags
- libyal: Windows Shell Item format specification
- 13Cubed: Shellbag Forensics
- GIAC: Windows ShellBag Forensics in Depth