An incident first response is only as good as the time a responder can save. While automation can help scale the prioritization of many endpoints, as we wrote in our last blog post, it’s also important to be able to correlate all those results together. In a dynamic environment, a dashboard can help responders to see how priorities change with each newly detected threat.
Time-saving incident-level feature enhancements
Cyber Triage 1.3 introduced the ability to group related computers into an incident, including a basic dashboard that shows progress on each computer. Cyber Triage 1.4 enhances that dashboard, and provides additional incident-level features — threat propagation within the incident and incident-level reporting — designed to make the triage process smoother and more easily visualized.
The new dashboard makes it easier to assess results at a glance. The dashboard now includes a list of common threats and a graph to show which threats were common among computers.
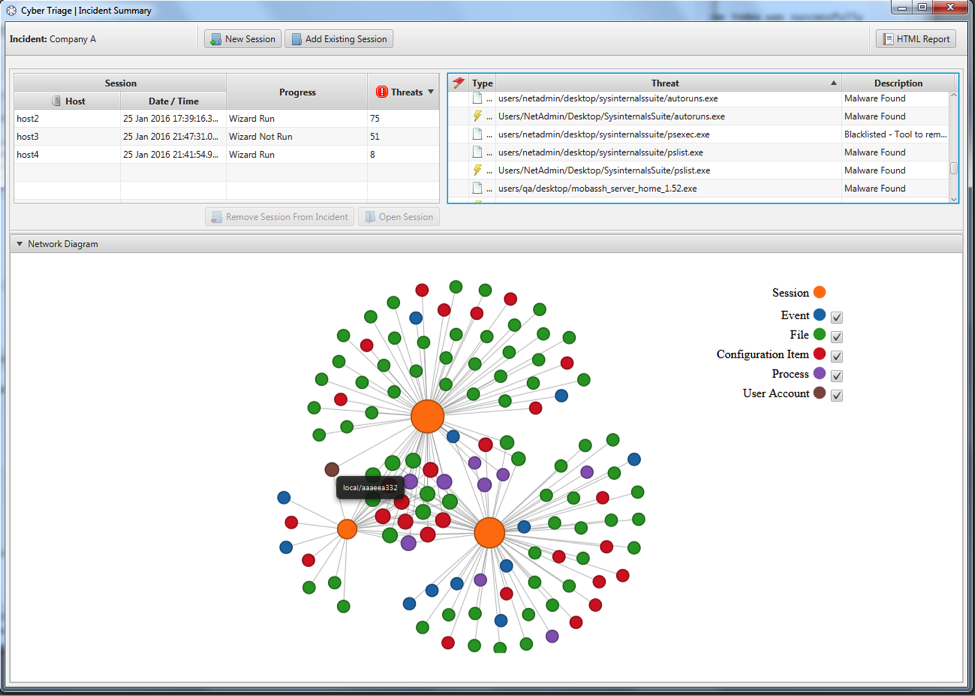
A set of related computers in an incident may contain the same threats. When a threat is found on one system, Cyber Triage now automatically marks it as bad on all hosts in the incident. This saves time and makes the process more consistent.
Along similar lines, Cyber Triage 1.4’s incident-level reporting allows you to generate a single report for all computers in the incident. This makes it easier to document and share your results with full context for other team members or clients.
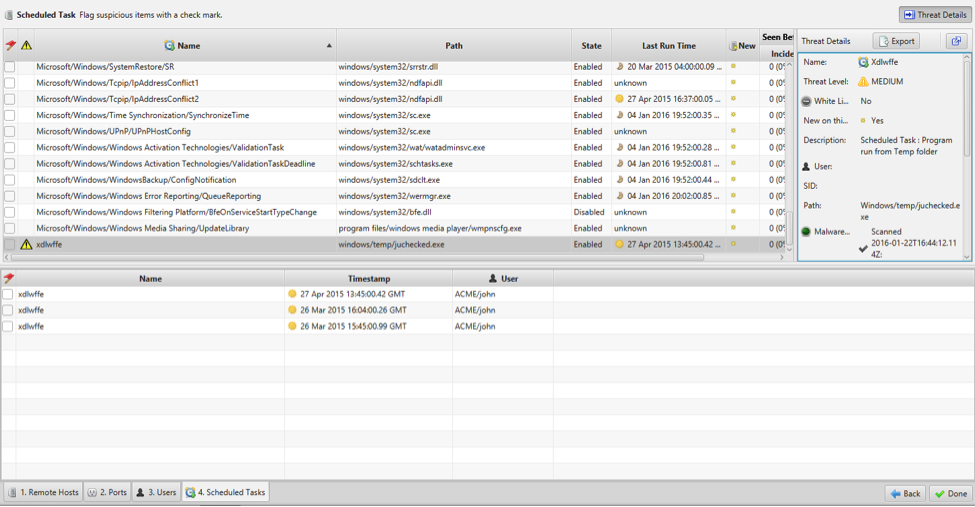
Review scheduled tasks for irregularities
Cyber Triage’s agent now collects and displays scheduled task information on a new wizard panel. This expands your visibility into the target computer by offering information on persistently running system background tasks. These tasks may or may not include threats, so Cyber Triage 1.4 allows you to evaluate information on scheduled activities and whether they reveal irregular activities or suspicious executables to investigate further.
Better blacklisting improves situational awareness
Threat intelligence integration continues in v1.4, as well, increasing the degree of control you have over the process. You can now blacklist more data types and import rules using a CSV file. To save time even further, you can automatically apply any items you add to the blacklist to other systems in the same incident.
Cyber Triage paves the way for our next release, scheduled for launch at the RSA Conference February 29 – March 3. If you’re planning to be there, stop by our booth #2732 for more information and free giveaways! If you’re not, watch this space for additional details — and in the meantime, contact us for a free demo.