Could you use some assistance with UserAssist forensics? This article by DFIR expert Chris Ray explains what UserAssist is, how it works, its forensic value, and so much more.
Let’s get into it.
Jump to…
Introduction to UserAssist
The Structure and Encoding of UserAssist Entries
How UserAssist Works
Forensic Value of UserAssist Data
When UserAssist Misses Data
UserAssist Forensics with Cyber Triage
Introduction to UserAssist
UserAssist is a Windows registry key that primarily records metadata relating to applications with a GUI component (similar to MUICache) and applications/lnk files launched from the Windows GUI.
| General Purpose | Improve user experience by recommending frequently used apps in the start menu. |
| Forensic Purpose | Find evidence of program execution.* |
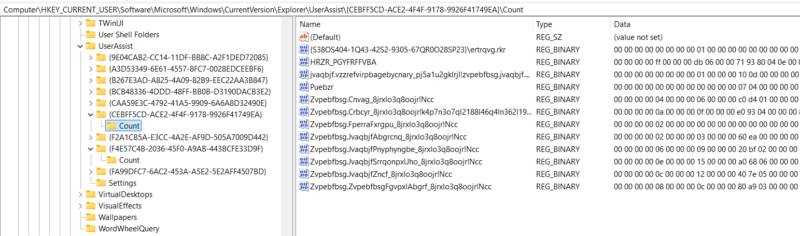
| Registry Location |
Live System: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist |
|---|---|
|
Dead Analysis: NTUser.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist |
|
| Main Keys of Interest** |
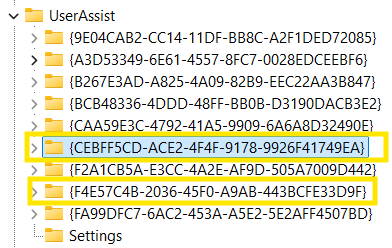
Exe-Related Artifacts: {CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\count
|
|
lnk-Related Artifacts: {F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\count
|
Notes
*On Windows 10 and later, not all entries indicate that a process actually ran. See, “How UserAssist Works” section for more info.
**There are other interesting keys on XP systems. We are focusing on Windows 10+ systems, as UserAssist on older systems has been written about numerous times; check some out here and here.
The Structure And Encoding of UserAssist Entries
UserAssist data isn’t stored in a straightforward format.
It’s obfuscated using Rot13 encoding and organized under specific GUID-labeled subkeys. Understanding how UserAssist structures and encodes its data is crucial for accurate forensic analysis.
There are 3 key elements:
- GUID keys
- Value names
- Value data
Let’s look at each.
GUID Keys
The GUID key signifies the type of data being recorded under that key. There are numerous GUIDs on Windows 7+ as documented here.
2 with significant forensic value are:
| Key Name | Notes |
|---|---|
{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}
|
Stores data on apps launched. |
{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}
|
Stores data on lnk files launched. |
Value Names
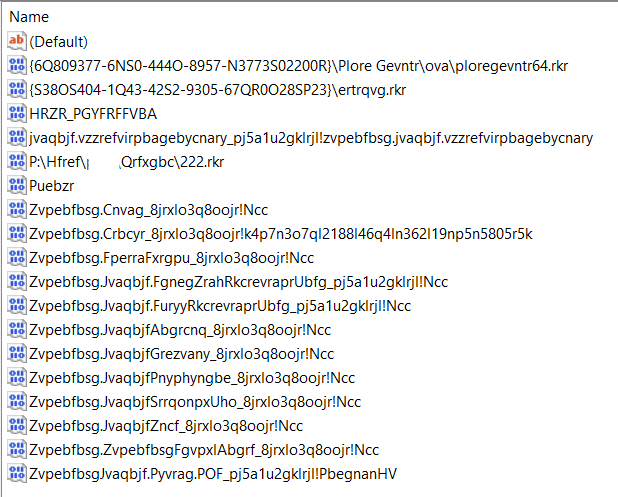
Each value name under “GUID\count” is the path to a program Rot13 encoded. This means any alphabetic character a-zA-Z is shifted over by 13 places. Z becomes M, A becomes N, etc.
Example: Rundll32.exe appears as ehaqyy32.rkr.
Note that not all entries will have a resolved path.
| Scenario | Example (After Decoding) |
|---|---|
| Windows Apps will show the package family name |
_Microsoft.WindowsNotepad_8wekyb3d8bbwe!App |
| Some paths will contain shell folder GUIDs |
{F38BF404-1D43-42F2-9305-67DE0B28FC23}\regedit.exe
|
Value Data
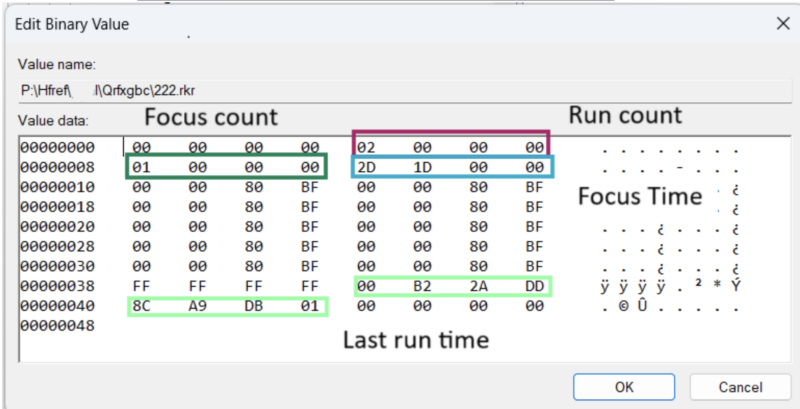
Value data is a binary blob known to contain the following info (starting at index 0):
| Name | Bytes | Definition |
|---|---|---|
| Run Count | 4-7 | Number of times app has been run. |
| Focus Count | 8-11 | Number of times app has been brought into focus (across all executions). |
| Focus Time | 12-15 | Total number of milliseconds app has been in focus (across all executions). |
| Last Run Time | 60-67 | Last time app was run – stored as Windows FILETIME. |
How UserAssist Works
This section outlines when UserAssist data is generated, based on tests from Win10+.
This is a general guideline on when to expect data to show up, but there are always edge cases that may not be accounted for.
We recommend verifying findings with other sources of evidence.
High Level
| Finding | Notes |
|---|---|
| For an entry to show up in a user’s UserAssist key, that user must be logged on interactively. | N/A |
When an application is run from the Windows GUI, a UserAssist entry will be created under:
{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\count
Run count and last run time will be updated. |
Windows GUI: desktop, taskbar, File Explorer, run dialog, Windows search/start menu. |
When a lnk file is run from the Windows GUI, UserAssist entries will be created under:
{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\count (for the exe)
{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\count (for the lnk)
Run count and last run time will be updated for both entries. |
Windows GUI: desktop, taskbar, File Explorer, run dialog, Windows search/start menu. |
When a GUI for an application is shown to a user, a UserAssist entry can be created under:
{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\count
Focus count and focus time will be updated. |
Note: Processes executed from the command line or other methods, not through the Windows GUI, can be recorded if the process has a GUI component. When this happens, the run count and last run time will not be updated; only focus time and focus count will be updated.
Note: The user account that a process runs as does not always match the user with the UserAssist entry. For example, a user logged in as User1 opens a command prompt as “Admin” and runs a GUI tool. The GUI tool will show up in User1’s UserAssist even though the process is running as the user “Admin.” |
When a file is opened from the Windows GUI, a UserAssist entry for the associated app responsible for opening that file will be created under:
{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\count
Run count and last run time will be updated. |
Example: If you open test.txt and your default program for handling .txt files is Notepad, then Notepad will be recorded as the exe in UserAssist.
Windows GUI: desktop, taskbar, explorer, run dialog, Windows search/start menu. |
Starting with Windows 10, if you use the “jump to file location” from the Windows Startup/search menu, then a useAssist entry will be created under:
{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\count
Run count and last run time are updated even though nothing was executed. |
This edge case on newer systems makes UserAssist data less reliable for determining process execution unless the entry is from the lnk GUID or has a non-zero focus time. |
Details
The following scenarios will result in:
- UserAssist entries being created.
- Run count/last run time being updated.
| Run Exe from |
|---|
|
| Run Lnk (pointing to exe) from* |
|---|
|
*Entries for both exe and lnk are created.
** lnk/exe was never run. This also only creates an entry for the exe and not the lnk file.
| Open .txt File Using Shell Run Dialog |
|---|
| Same as the “Run exe” section, except the exe in this case is the default app associated with the file extension. |
| Open .lnk File (pointing to .txt) from Shell Run Dialog |
|---|
| Same as the “Run lnk from” section except the exe in this case is the default app associated with the file extension. |
The following scenarios will not result in UserAssist entries being created (unless exe has a GUI component):
| Scenario | Instructions/Notes |
|---|---|
| Run from PowerShell/cmd |
|
| Run from Explorer search bar |
|
| Run via Windows CreateProcess API |
|
| Run via Windows ShellExecute API |
|
| “Open File Location” on lnk files |
|
| Right-click option from anywhere |
|
These tests were run on the latest versions of Windows 10/11.
All exes run during tests had no GUI component (unless otherwise specified) to ensure focus time and focus count did not result in making UserAssist entries.
Forensic Value of UserAssist Data
UserAssist data is a valuable artifact in digital forensic investigations, offering insights into user activity on a Windows system.
| Determining user activity | Identify processes and lnk files a user has run. |
|---|---|
| Identify the frequency and usage pattern for applications based on run count, focus time, and focus count. | |
| Identify that a user was logged on interactively during a process’s last run time. |
| Corroborating evidence | Cross-reference UserAssist data with Prefetch, Jump Lists, Event Logs, and SRUM for a fuller picture. |
|---|
| Limitations | Does not track command-line arguments. |
|---|---|
| Does not keep historical command execution times, just the last execution and number of times executed in total. | |
| Does not record all process execution like event log. Limited to exe/lnk launched from GUI and apps with a GUI component. |
When UserAssist Misses Data
While it’s important to understand what data is contained in the UserAssist artifact, it’s equally important to understand when data will not show up in the UserAssist artifact.
Several scenarios result in data not showing up in the RunMRU key:
- UserAssist history is disabled.
- UserAssist history has been cleared.
- Process activity happens outside scope of UserAssist monitoring.
Let’s look at each of these.
UserAssist History Is Disabled
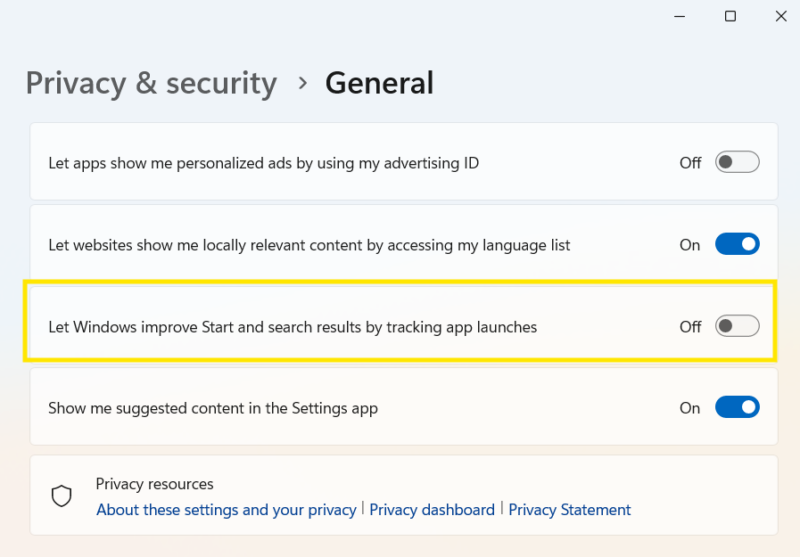
The UserAssist history can be disabled 2 ways, both are applied on a user-by-user basis:
Method 1: Disable Tracking app launch in Windows privacy settings.
Method 2: Update the UserAssistregistry key with a Deny All ACL.
We have previously discussed these methods in our runMRU blog. Check that out for more details.
UserAssist History Has Been Cleared
UserAssist history can be manually cleared by attackers by deleting the UserAssist key or specific subkeys/values. This will need to be done for every user the attacker has had interactive sessions with.
Process Activity Happens Outside Scope of UserAssist Monitoring
This is a major reason why we cannot rely on UserAssist alone. It’s not an audit log of process activity, but a Windows feature used to derive forensic value.
The data contained here will:
- Best Case: Contains the last execution time of a process with a run count.
- Worst Case: Not have evidence of process execution at all.
For example, a command line tool like ping or whoami, which may be used for recon by an attacker, will not be recorded in UserAssist when launched via command prompt.
The process will be missed if:
- It was not launched via the Windows GUI.
- It does not have a GUI component.
Extracting and Analyzing UserAssist Data
UserAssist is not an easy artifact to manually review, given the encoded process names and binary data.
Some UserAssist forensics tools:
| Cyber Triage | A commercial DFIR tool that processes many artifacts, including userAssist. |
| Registry Explorer | Registry view that comes with a plugin to parse UserAssist data. |
| RegRipper3 | Registry parsing tool that has plugins to parse UserAssist data, as well as settings to check if UserAssist has been disabled. |
| Autopsy | Open-source forensic platform with registry parsing capabilities. |
| NirSoft UserAssistView | Standalone GUI tool specifically for parsing UserAssist data. |
| Plaso | A Python-based engine used by several tools for automatic creation of timelines. UserAssist module here. |
UserAssist Forensics with Cyber Triage
UserAssist is what we call a data artifact.
Information extracted from UserAssist and other data artifacts is what we call information artifacts.
Information artifacts are a way of categorizing data artifacts, and UserAssist falls into the “process run” information artifacts category.
We recommend that investigators think about artifacts like this because it helps them focus on the right things. Many data artifacts have a similar computing function, but differ slightly in the details. If investigators think top-down, they can see the big picture more easily. If they think bottom up, they can easily get confused by details.
We built the Cyber Triage UI around this investigation philosophy.
Cyber Triage displays information artifacts regardless of the data artifact (UserAssist, MUICache, Prefetch, etc.) from which it came.
With UserAssist, we are looking at processes. So, Cyber Triage’s UI puts all the “processes run” artifacts together. Instead of reviewing single data artifacts like UserAssist— especially when it’s missing arguments and other key details — you see everything in a single view. So you have context that UserAssist alone can’t provide.
This enables you to figure out — really quickly — what a user executed.
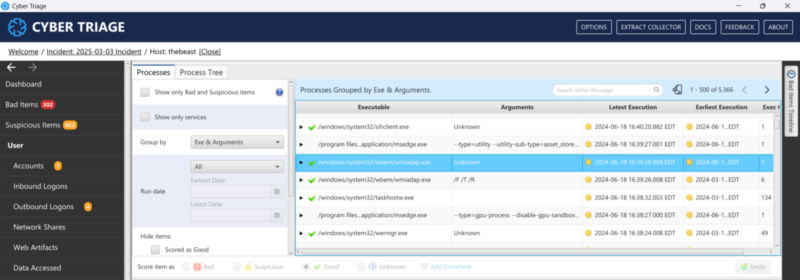
Cyber Triage’s process table is in the screenshot below.
It’s grouped by:
- Exe
- Arguments
The group can be updated to also include users if that is what we care about.
Groups show:
- Last execution time
- Earliest execution time
- Count of instances for each group
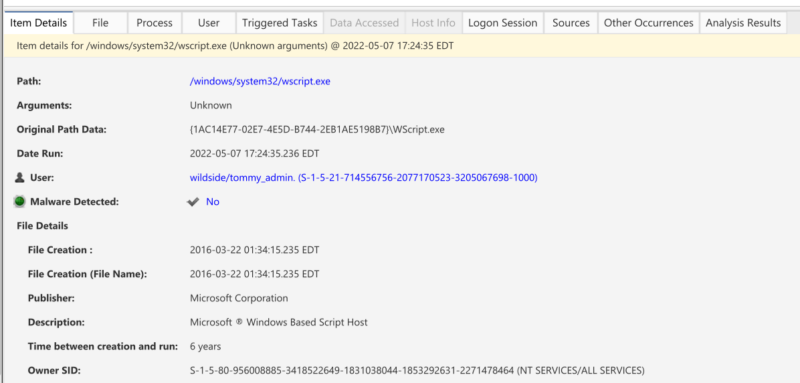
You can jump into each group and select individual process execution instances to get more details. Below is a process from UserAssist. The arguments are unknown.
You can view:
- Original data normalized from the data artifact
- Associated user
- Execution time
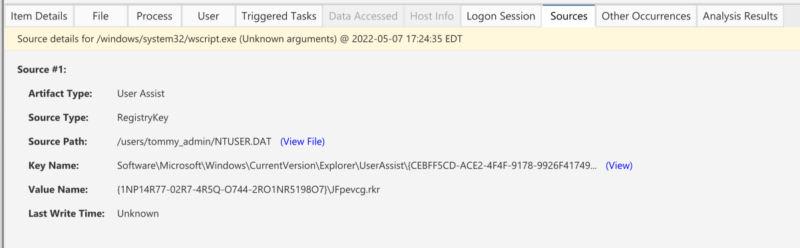
Curious about where an information artifact came from? The sources tab has those details, and other tabs provide context about the item you’re reviewing, too.
For instance, we are looking at a process and can jump to the “Triggered Tasks” view to see if there is any persistence for it or the “File” view to get details about the file on disk (if it exists):
To focus on a specific data artifact, the artifact sources table shows all the data artifacts Cyber Triage processes:
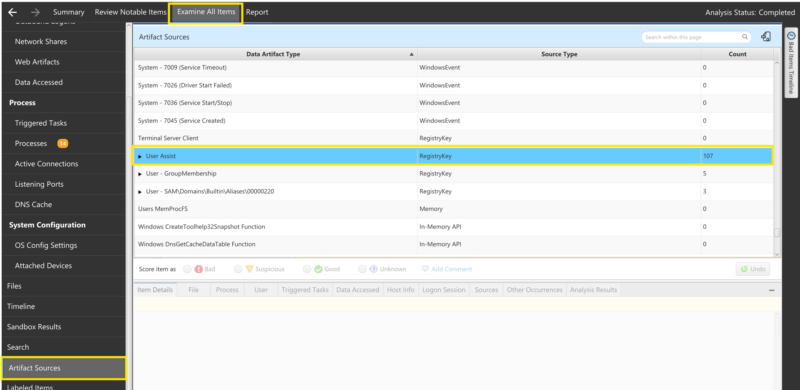
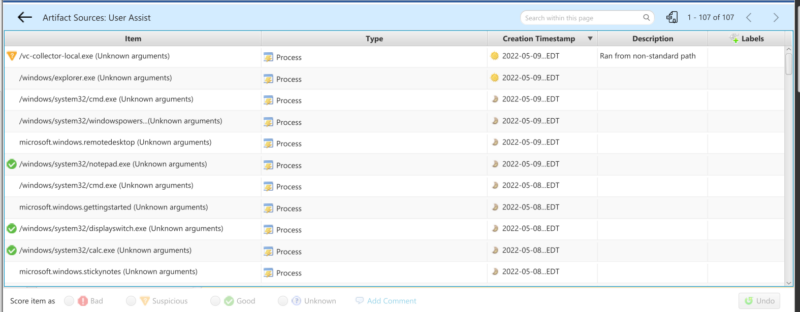
Opening up the UserAssist group lets you see all process execution artifacts pulled from UserAssist:
If you’d like to try investigating UserAssist with Cyber Triage now, try 7 days for free.