Attackers can use WMI malware for just about anything. Execution, persistence, lateral movement… honestly, the list goes on. Fortunately for you, there are blogs like these that will help you understand exactly how bad guys use WMI.
And exactly how good guys – AKA you – can stop them.
Now let’s get to it.
Jump to…
Introduction to WMI Malware
How Attackers Use WMI Malware
Real-World Attacks
4 WMI Malware Detection Techniques
Find WMI Malware Easily
Introduction to WMI Malware
Windows Management Instrumentation (WMI) is a Microsoft framework for system management that doubles as a versatile tool for bad actors. As DFIR expert Chris Ray explains, “WMI activity is important to review for malicious behavior due to its wide abuse by threat actors. It provides an easy way for threat actors to create processes, tamper with system settings, and perform system recon all without needing to bring in additional tools.”
Why it’s dangerous:
- Standard Windows feature so threat actors can blend in.
- Enables “fileless” persistence, making file-based scanning useless.
- Allows threat actors to be less reliant on external tools.
How attackers access it:
Use in the attack life cycle:
Now, let’s take a closer look at each of these.
Get Technical on WMI
Want to learn more about the technical details of WMI? Here are a few resources we recommend:
- FireEye: WMI Forensics Whitepaper.
- 0xInfection: Offensive WMI series.
How Attackers Use WMI Malware
WMI for Execution
| Attackers Can Create a Process Locally |
|---|
Examples:
|
| Attackers Can Create a Process Remotely |
|---|
Examples:
|
| Attackers Can Create Services Locally |
|---|
|
Examples: Invoke-CimMethod -ClassName Win32_Service -MethodName Create -Arguments @{
Name = "Service name"
DisplayName = "Service display name"
PathName = "%comspec% ping google.com"
StartMode = "Automatic"
StartName = "LocalSystem"
}
|
| Attackers Can Create Services Remotely |
|---|
|
Examples: Invoke-CimMethod -ComputerName blocker -ClassName Win32_Service -MethodName Create -Arguments @{
Name = "Service name"
DisplayName = "Service display name"
PathName = "%comspec% ping google.com"
StartMode = "Automatic"
StartName = "LocalSystem"
}
|
Attackers can use WMI to initiate new processes on both local and remote systems via the create method for:
The WMIExec.py script is a commonly abused script that uses Win32_Process for remote process creation.
WMI for Discovery
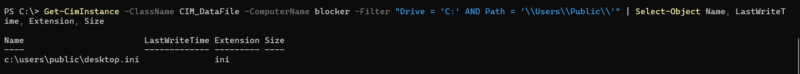
| Attackers Can List Directory Content Remotely |
|---|
Examples:
|
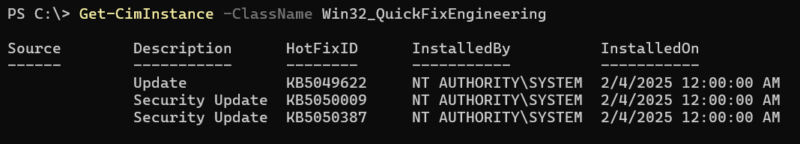
| Attackers Can Check Installed Patches |
|---|
Examples:
|
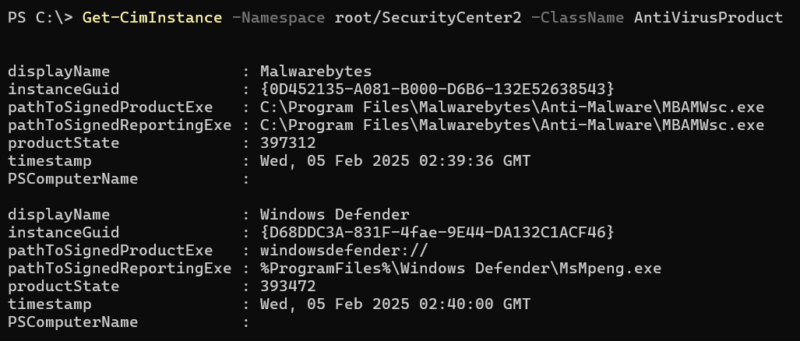
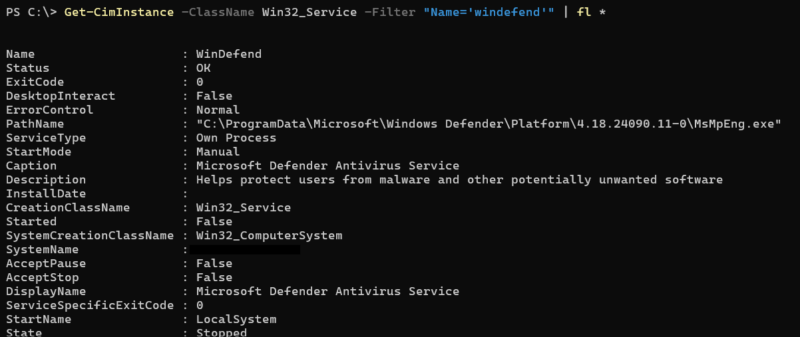
| Attackers Can View AV Software |
|---|
Examples:
|
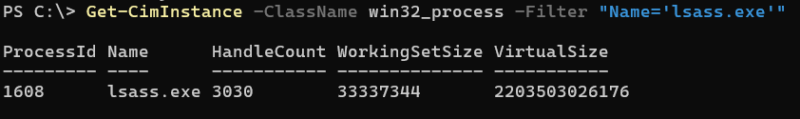
| Attackers Can View Running Processes |
|---|
Examples:
|
| Attackers Can View Active Services |
|---|
Examples:
|
Attackers can use WMI to collect a wide range of system data, both locally and remotely.
This includes:
- Checking installed antivirus software via the AntiVirusProduct class.
- Tracking Windows updates and patches via the Win32_QuickFixEngineering class.
- Listing active processes/services via the Win32_Process and Win32_Service classes.
- Listing content of directories via the CIM_DataFile class.
WMI for Defense Evasion
| Attackers Can Disable Firewall |
|---|
Examples:
|
| Attackers Can Disable Critical Services |
|---|
Examples:
|
| Attackers Can Clear Event Logs |
|---|
Examples:
|
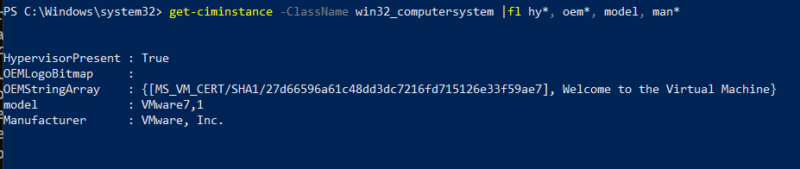
| Attackers Can Avoid Sandbox Analysis |
|---|
Examples:
|
Attackers can use WMI to tamper with system logs and critical services and evade detection.
This includes:
- Disable Windows Firewalls via MSFT_NetFirewallProfile.
- Disable critical Windows services via Win32_Service.
- Clearing event logs via NTEventLogFile class.
- Checking for virtualization/sandboxing via Win32_computersystem class.
WMI for Impact
| Attackers Can Block System Recovery |
|---|
Examples:
|
| Attackers Can Force System Reboot |
|---|
Examples:
|
Attackers can use WMI to disrupt system recovery and force reboots or shutdowns.
Here’s how:
- Win32_ShadowCopy class can be used to delete volume shadow copies, inhibiting system recovery.
- Win32_OperatingSystem class methods can force restarts/shutdown.
These tactics are often used in ransomware attacks to make recovery harder or in stealthy intrusions to cover their tracks.
WMI for Persistence
| Attackers Can Create WMI Consumers |
|---|
| For examples and more on WMI Consumers for persistence, read: |
| Attackers Can Create Services |
|---|
| See the execution section for examples. |
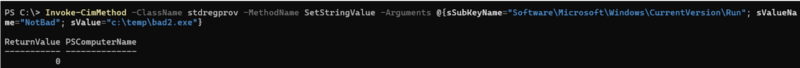
| Attackers Can Create Autorun Keys |
|---|
Attackers can use WMI to set up persistence mechanisms.
This includes:
- Creating persistent consumers (similar to scheduled tasks).
- Creating services via the Win32_Service Create method.
- Changing registry autorun keys via stdRegProv methods.
A tool called WMIPersis.py simplifies this process by automating event consumer-based persistence.
Real-World Attacks
ShrinkLocker Ransomware
| Where WMI Was Used | |
|---|---|
| Win32_ComputerSystem |
|
| Win32_OperatingSystem |
|
| Win32_OptionalFeature |
|
| StdRegProv |
|
| Win32_PerfRawData_Tcpip_NetworkInterface |
|
| Win32_Service |
|
| Win32_Volume |
|
| Win32_EncryptableVolume |
|
Blue Mockingbird Cryptominer
| Where WMI Was Used | |
|---|---|
| Create persistence via COR_PROFILER |
|
Metador
| Where WMI Was Used | |
|---|---|
| WMI persistence via WMI persistent consumers |
|
Learn More About Real WMI Malware Incidents
- Bitdefender: A Decade of WMI Abuse – an Overview of Techniques in Modern Malware.
- MITRE: WMI procedure examples.
4 WMI Malware Detection Techniques
| #1 Monitor for WMI Consumer Persistence | |
|---|---|
| Why |
|
| Where | |
| What to look for |
|
| #2 Monitor for Unusual Children of Scrcons.exe | |
|---|---|
| Why |
|
| Where | |
| What to look for |
|
| #3 Monitor for Unusual Children of Wmiprvse.exe | |
|---|---|
| Why |
|
| Where | |
| What to look for |
|
| #4 Monitor Process History for Unusual Usage of WMI Commands | |
|---|---|
| Why |
|
| Where | |
| What to look for |
|
Find WMI Malware Easily
It’s important for investigators to understand the fundamentals of WMI, the technical details and classic strategies aren’t really required anymore. Once you understand the basics, investigators should focus on the big picture of an investigation.
And it’s the job of software to take care of the rest.
Cyber Triage is just such software. Cyber Triage automates the collection of all the artifacts (like WMI) investigators need and scores them according to how suspicious they are using Automated Analysis.
It radically speeds up (and improves the accuracy) of investigations.