Crimes where digital evidence is critical, such as Internet Crimes Against Children (ICAC) cases, may result in the suspect claiming that someone else placed the evidence there. With Cyber Triage, you’ll easily know if the device had any signs of remote access.
You can simply point it at your disk image, let it run, and review the automated results. Cyber Triage will look for malware backdoors, commercial remote access software, and Windows authentications.
Many Types of Remote Access Artifacts
Devices can be accessed remotely in many ways, including:
- Software that ships with the computer, such as Remote Desktop.
- Commercial software, such as AnyDesk or LogMeIn
- Malicious Remote Access Trojan (RAT) software, such as Cobalt Strike or Xeno RAT.
Detecting the existence and use of these tools requires knowledge about what is possible and where the usage artifacts are stored. If an attacker wants to hide, there are several ways for them to try to blend in.
Ultimately, the suspect should also be able to show evidence of remote access if it exists, but it’s important that you look for that evidence to pre-empt their trojan defense (aka some other dude did it) and to identify exculpatory evidence.
Automated Remote Access Analysis
Cyber Triage uses its automated analysis pipelines to identify remote access with little interaction. It will flag the existence of remote access software and show you the remote Windows logins from event logs.
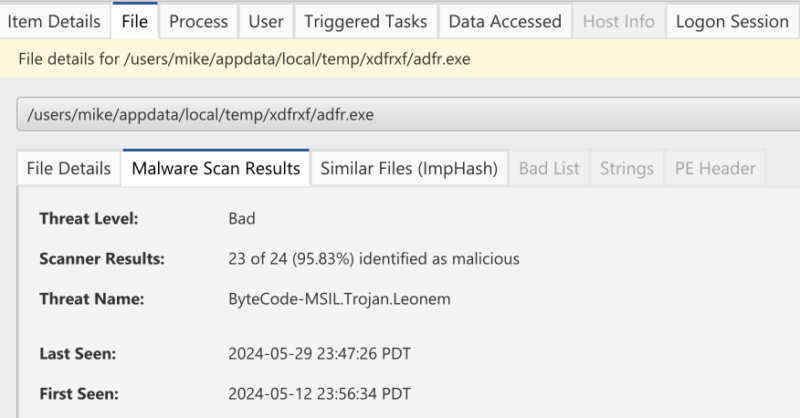
40+ Malware Engines
To detect malicious backdoor software, Cyber Triage analyzes executables with over 40 malware scanning engines to get broad detection coverage. All executables that are launched at computer startup, from a scheduled task, or that were recently manually launched will be analyzed.
You can also choose to upload executables to the Recorded Future sandbox for dynamic analysis and identify what network ports are opened or files created.
More details, such as offline scanning, can be found here.
Application Database
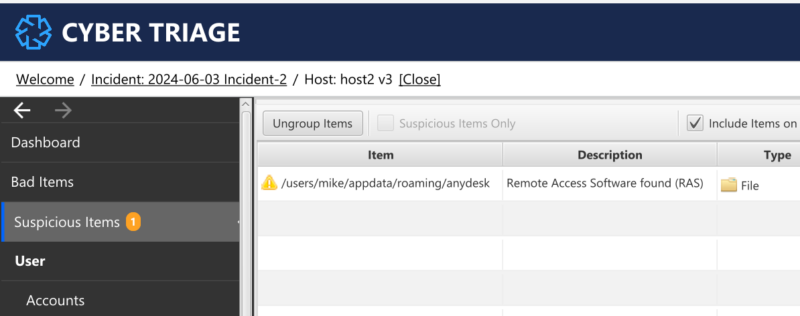
Commercial software, such as those used by IT departments for remote administration, is also used by attackers. Cyber Triage maintains a database of file names and hashes for commercial applications.
These databases are used during the automated analysis of the files to detect if commercial applications exist. If the attacker renames the executable file to hide it, Cyber Triage will still detect the log files and configuration folders, which will use the original name.
Windows Event Log Parsing
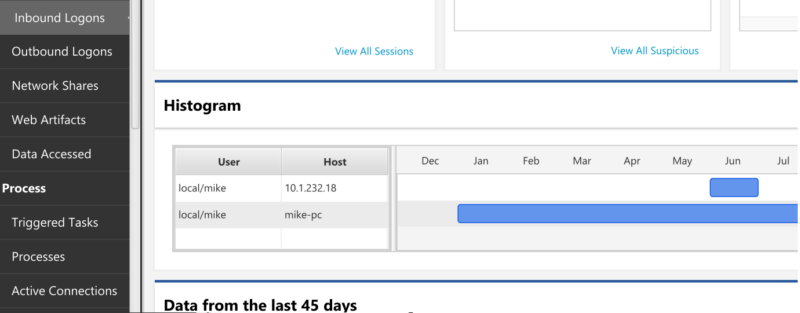
Event logs contain information about when a user logs in using Windows Remote Desktop, when the computer’s hard drive was mounted for file sharing, or when Powershell was remotely launched. While complicated to parse manually, they can contain clues when Windows remote access applications were used.
Cyber Triage parses and merges several logs and events to define a “logon session” for a user, which includes its start time, end time, and source. You can review these sessions within Cyber Triage to detect if all of the sessions are local or if any are remote.
Load and Review
Cyber Triage requires little user interaction to analyze your disk images for remote access. Simply load it, enable malware scanning, and let it parse and analyze the artifacts.
- You will be presented with a set of bad and suspicious items
- If there is malware, you should investigate its capabilities
- If there is a commercial remote access application, then you should review its logs
- You should review the inbound logons and understand why there is remote access:
If nothing was found and all logons are local, then there is no obvious evidence of remote access.
Try It Today
If you want more confidence in your investigations, try Cyber Triage. You will get a free, 7-day evaluation to load in previous cases or disk images to see what it shows.
Cyber Triage comes with free access to the Training Bundle, which includes a 4-hour hands on Basics course.