When investigating an endpoint you need to look at user activity in addition to malware and system change indicators. Cyber Triage now provides analytics about user login behavior and activity. This makes it easier for incident responders to determine if a user account was compromised or if a local user downloaded malware, and respond appropriately.
Download the latest version of Cyber Triage from here and read more details below.
Users Are a Weak Link
User accounts are important to investigate because they can be compromised by attackers. The 2016 Verizon DIBs survey shows that 63 percent of attacks involved compromised accounts.
One reason is that users are often the easiest way to gain initial access into a company. Users are sent phishing emails with malware attachments or are tricked into downloading programs when browsing websites. Once the attacker has gotten the user to run malware, they can then use that computer as a launching point. Investigation of user activity can allow you to find the source of these attacks and disconnect the compromised computer.
Regardless of how the attacker got in, they may next steal the credentials of a legitimate user to avoid detection and get better access to data they want to steal. If your incident response process doesn’t investigate user activity, you may fail to identify accounts that have been taken over by an attacker. Logins at strange times or from strange sources are a common sign of a compromised account. You may also find the user running programs and accessing data that is unexpected for their job.
Investigating Users with Cyber Triage
Cyber Triage allows you to more easily investigate users. Its agentless-collection tool will copy data from various places on the target system and presents them in a consistent way for you to look for suspicious activity and draw conclusions.
The Users panel allows you to see login names and times to review what users logged into the system and who has administrator access.
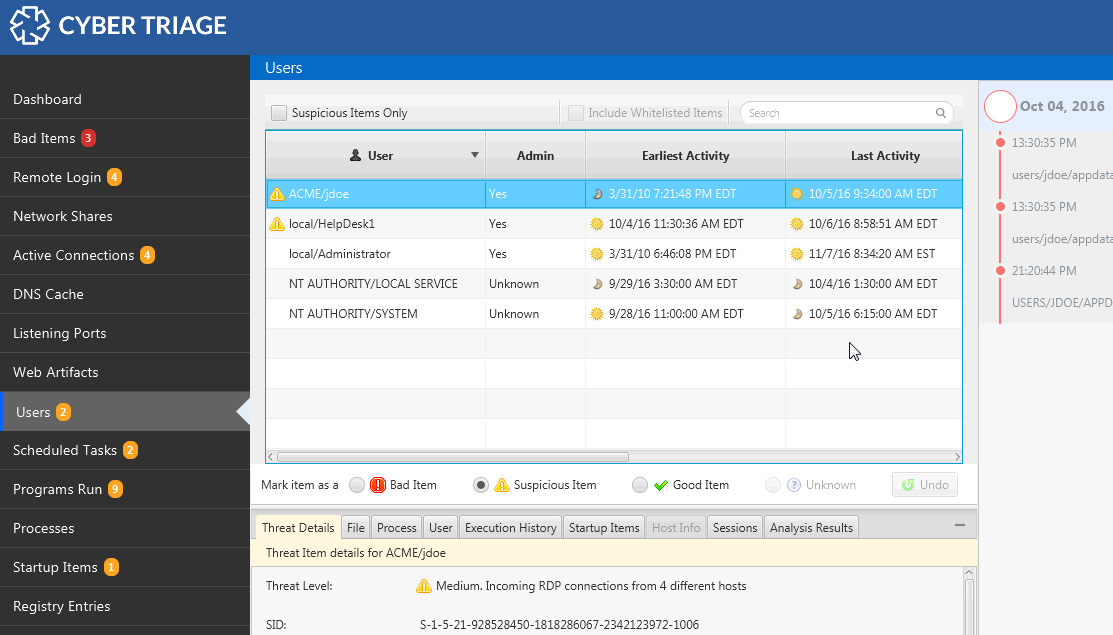
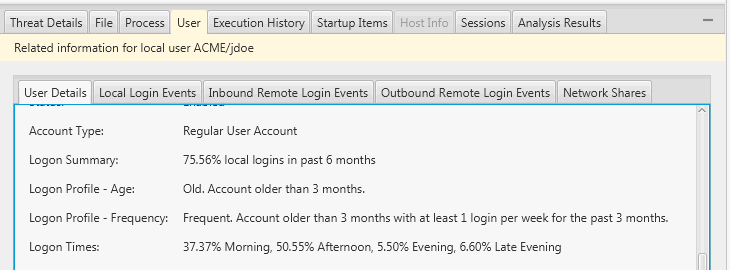
The most recent release, includes analytics for user activity. View what times a user typically logs into the system, how often, and how old their account is. These features allow you to determine if the user just started remotely logging into the system (perhaps as part of lateral movement when the attacker jumps between computers) or if they have been doing this for years. Without these analytics, you need to manually review all login events to build a mental model of the user.
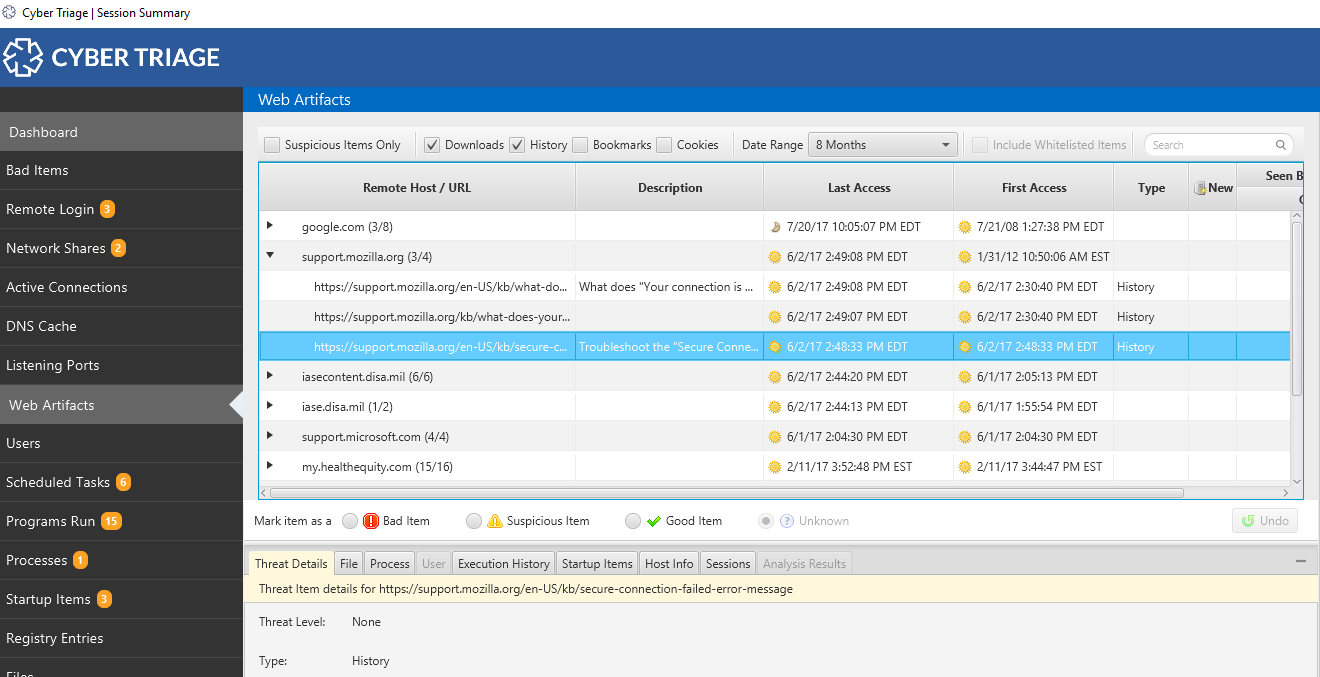
Also new in the most recent release, you can see user’s browser activity to see what files they downloaded and websites they visited. This helps you figure out if they downloaded a suspicious executable or searched for terms that may imply they are an insider threat.
Of course, you’ll want to look at more than just the login and browser activity. You’ll want to look at other user activity and Cyber Triage allows you to review:
- Programs the user ran (based on registry analysis, prefetch, and more)
- Network shares the user accessed (based on paths accessed, processes, programs run, etc.)
Users are Critical
When triaging an endpoint, you need to look for malware, system changes, and user activity. The new Cyber Triage features help you more quickly and effectively focus on the users. If you’d like to try Cyber Triage, use this form to get your free evaluation copy. The Lite (free) version of Cyber Triage includes the web browser collection, but not the user analytics.
Photo Credit: (c) Can Stock Photo / ollyy



