The Cyber Triage Workflow
How Cyber Triage makes your investigations faster and more comprehensive.

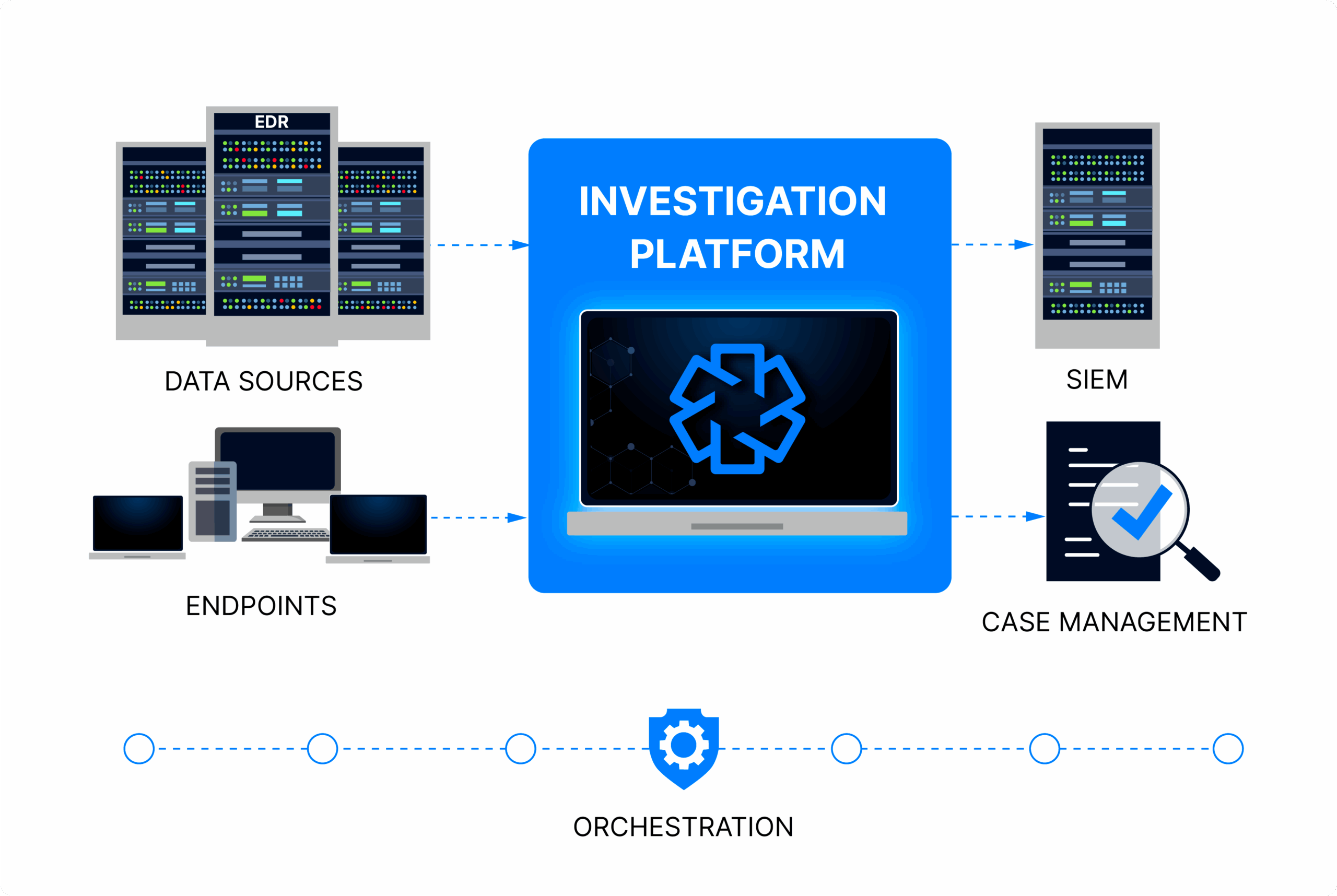
CollectUse the Cyber Triage Collector, EDR, or other 3rd party tool to collect endpoint data.
Step01

IngestImport data into Cyber Triage so that it can normalize it and prepare it for analysis.
Step02

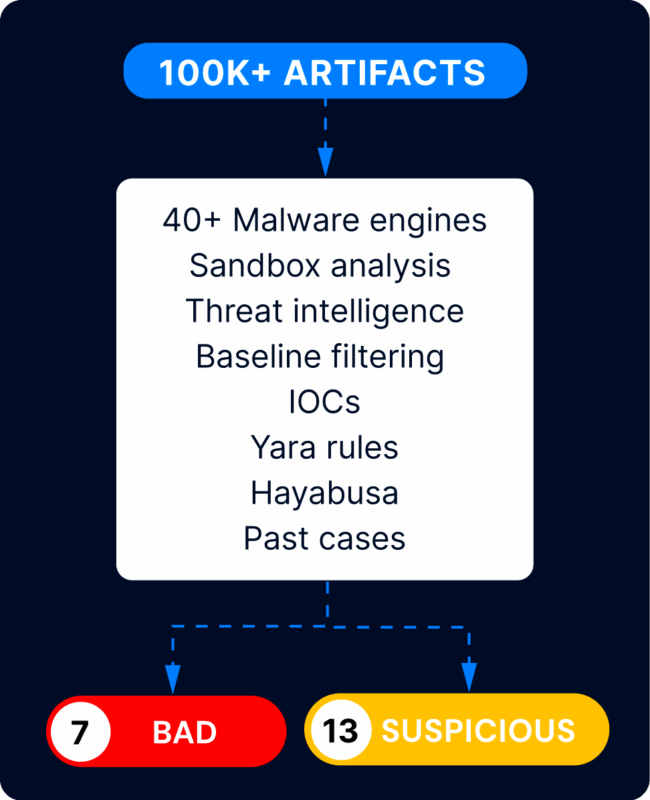
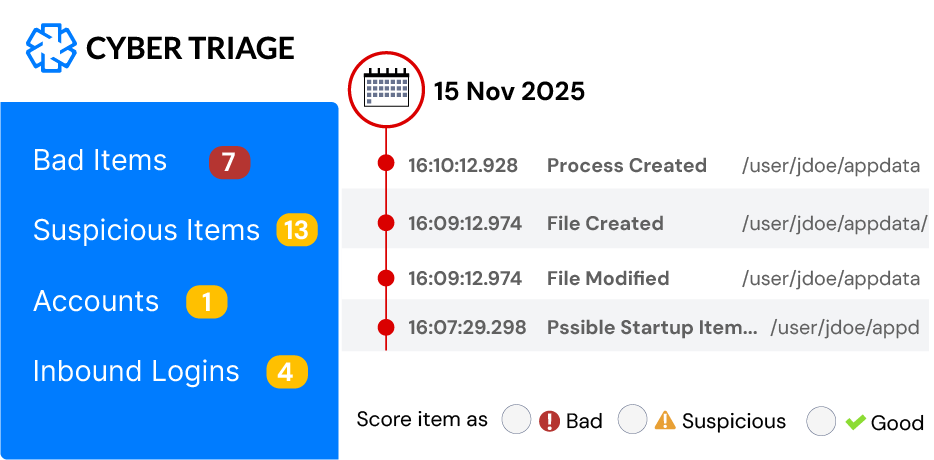
Automated AnalysisAutomated Analysis highlights bad and suspicious items for review.
Step03

Assisted ExaminationDuring review, related items are automatically found and recommended.
Step04

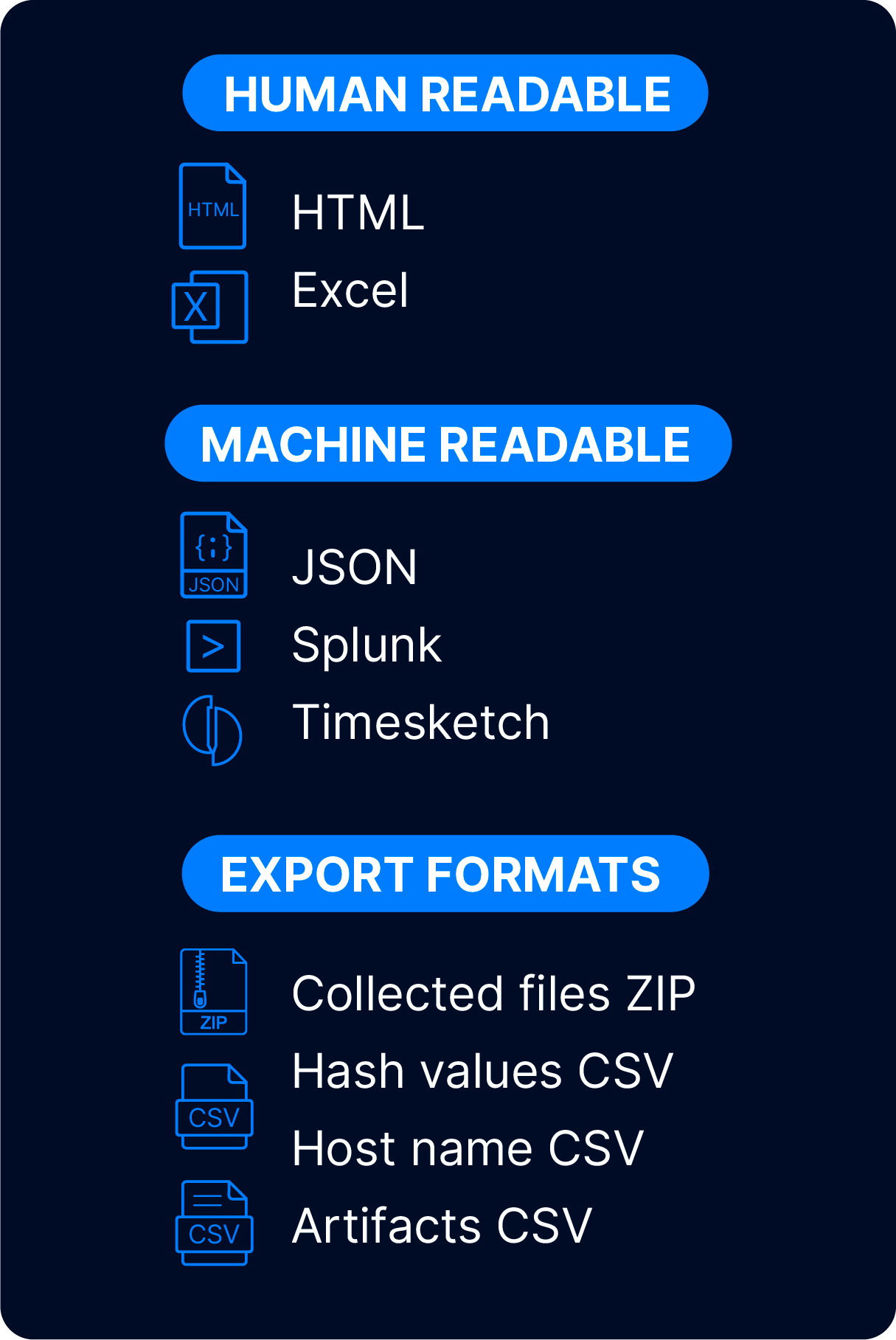
ReportFindings can be exported into multiple report formats, including HTML, JSON, Excel, and CSV.
Step05
Ingest
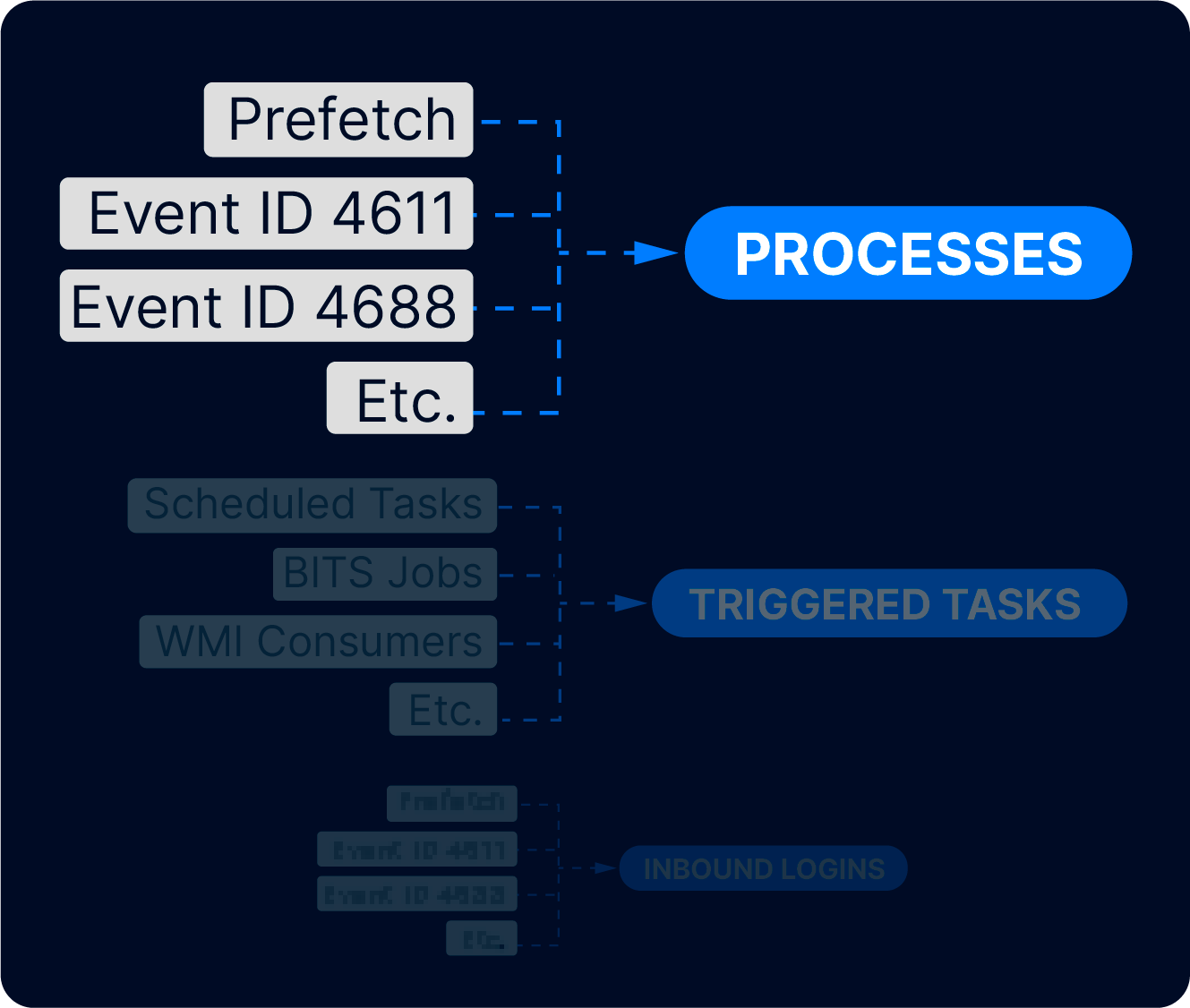
Cyber Triage simplifies investigations by focusing on high-level “Information Artifacts” instead of low-level “Data Artifacts.” When you add endpoint data into Cyber Triage, it will normalize and merge the low-level artifacts.
This results in less training required and less data to review.
Assisted Examination
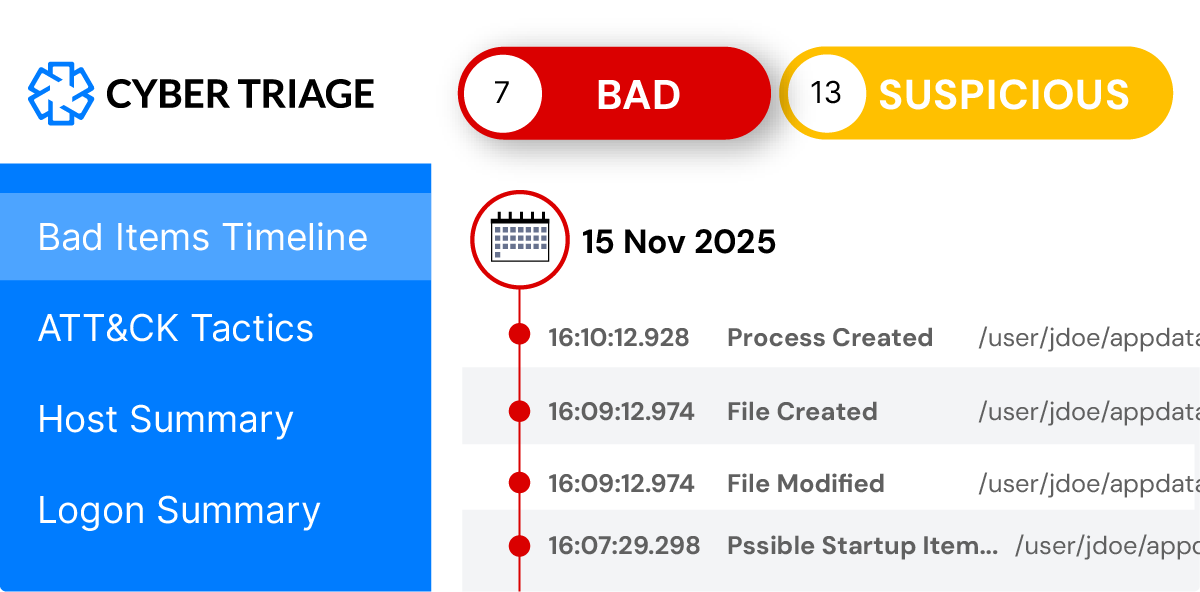
Ultimately, you need to decide what is relevant to the incident and understand the scope. Cyber Triage assists you by giving you context and providing recommendations as you investigate.
The Team versions also allow multiple investigators to collaborate on the same incident at the same time.
Report
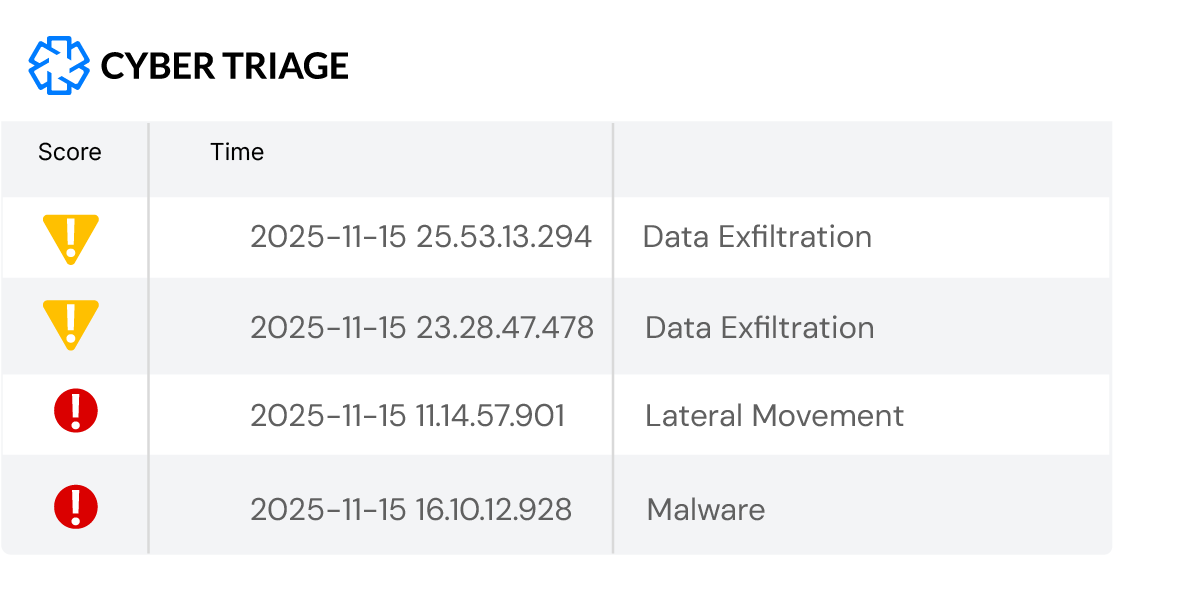
Your findings need to be shared with other humans and machines. Cyber Triage has a variety of output formats to support that.
We know you may want to use other DFIR tools in addition to Cyber Triage. We allow you to export all of your collected data in other standard formats.
Cyber Triage in Your Environment
What Users Say
“What used to take me four to six hours, I can do with Cyber Triage in a few clicks. It’s a huge time saver.”
Cybersecurity Architect
at Global Conglomerate

“My EDR’s UI doesn’t provide a clear view of the data. With Cyber Triage, I can tell a better story.”
Infosec Manager
at NASDAQ 100 firm

“I don’t have time to keep my skill set up. Cyber Triage ensures that my investigations are informed by the latest threat intelligence.”
Infosec Expert
at Billion-dollar manufacturer

Try Cyber Triage
Try Cyber Triage to see how it will make your intrusion investigations faster and more comprehensive. Fill out this form to get an installer. Get started with our scenario data (or your own).
Download your free 7-day evaluation
with scenario data