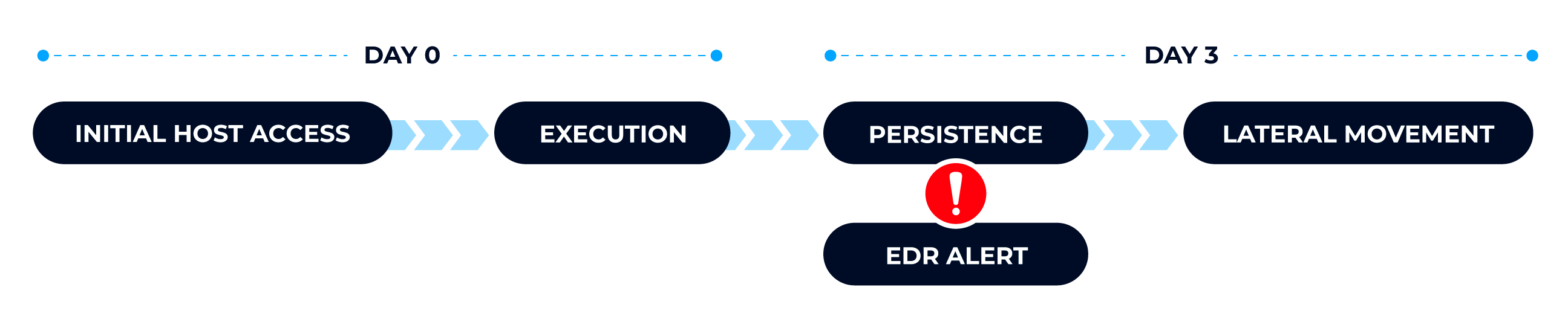
EDRs Can Miss Initial Activity
Endpoint Detection and Response (EDR) platforms can miss attacker activity. They could have been active for days before the first alert because they evaded the EDR, used tools already on the system, or other novel techniques.
Once you get an alert, you need to investigate the host to understand what else may have happened that was not detected.
EDRs Are Not Investigation Tools
EDRs contain lots of valuable endpoint data, but they are not optimized for an investigation. They are optimized for detection and containment.
It is tedious and error prone for a SOC analyst to manually perform queries on an EDR to look for suspicious processes or web activity. The queries produce thousands of entries that must be manually reviewed.
To quickly investigate recent activity on an endpoint, automated investigation tools are needed that will highlight activity for the SOC analyst to focus on.
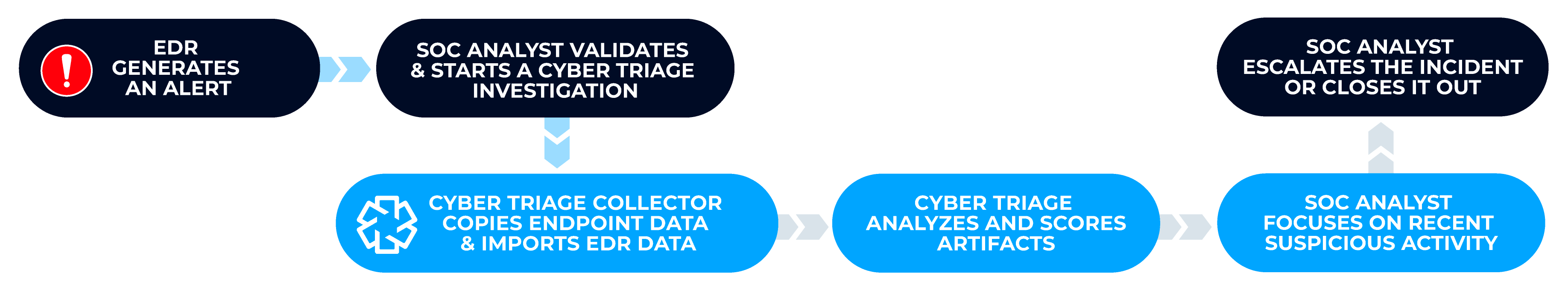
Investigate Alerts with Cyber Triage and Your EDR
Cyber Triage works with your EDR to ensure that alerts are investigated.
- Investigations are quickly started from within the EDR or SOAR.
- Data from both the EDR and the Cyber Triage Collector are merged to provide a more complete picture of activity.
- Recent changes and suspicious activity is highlighted for the analyst to focus on.
Cyber Triage’s automated analysis and scoring will ensure that all of the data is analyzed and the analyst can focus on a small number of artifacts and not thousands.
Quickly Start Investigations
Integrate Cyber Triage with your EDR or SOAR to quickly start an investigation from within a playbook or live response capability. This ensures that SOC analysts can quickly start collecting, preserving, and analyzing additional information.
Data from the EDR and Cyber Triage Collector will be merged (coming soon) to create a unified view of the host. This ensures that all existing data is leveraged, including that not observed by the EDR.

Focus on Recent and Suspicious Activity
Cyber Triage will highlight recent host activity that is suspicious and could be relevant to an attack. You do not need to manually review thousands of artifacts.
When investigating a host, you need to understand what other suspicious activity happened on the system. Cyber Triage’s automated analysis pipelines ensure you see that activity and understand what else happened.
Preserve Evidence for Future Investigations
Evidence can be deleted either from EDR retention periods or normal system activity. EDRs may retain data for only 7 to 30 days. If this alert was part of a bigger incident that is not fully understood for several days, then having the data preserved is critical.
Data collected into Cyber Triage is preserved even when the original data is deleted. Cyber Triage will use this collected to link with future investigations.

Everything You Need to Conduct Thorough and Accurate Investigations
Use the complete Cyber Triage Toolkit to quickly and correctly diagnose an intrusion, explain what happened and why, and to make sure it doesn’t happen again.
Being able to respond quickly to an intrusion and conduct a fast, accurate investigation will limit damage and make everyone breathe a little easier in what can be a very difficult situation.